
Understanding Layer 2 switch port security
Safe Switch
A switch port is the entryway into a network. Depending on network size, there may be thousands of access ports or more distributed across a campus or building. Imagine thousands of doors all over your house: Do you have enough security to prevent unauthorized people from entering?
MAC Address Table
If someone wants to launch an attack through an unsecured port, a switch's Media Access Control (MAC) address table is a good choice. A successful attack to the MAC address table can change the network traffic destination, compromise data confidentiality, and even make the network unavailable, all in a very short time. In this article, I explain how a switch uses the MAC address table, introduce some common methods for attacking the MAC address table and finish up with a security solution to protect a switch from attack.
Layer 2 Switch Operation
A switch provides Data Link Layer (or Layer 2) connectivity on an Ethernet network. Devices transmit data frames based on a unique 48-bit MAC address (Figure 1). The data frame contains a destination address and the sender's source address. When the switch receives the data frame, it looks for the destination address in its MAC address table and forwards the frame to the port specified with the destination address. In some situations, if the switch cannot find a valid record for the destination MAC address, it will send the data frame to all ports except the originating port. This type of broadcast delivery is not a good practice because it wastes bandwidth, and anyone on the same network segment could receive the data frame and exploit the data to gain information for an intrusion attempt.

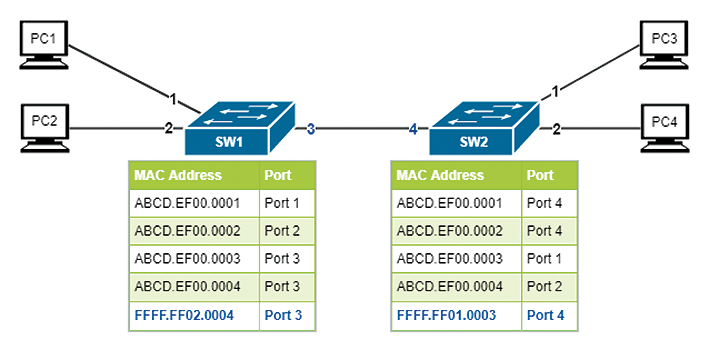
When a network contains two or more switches, each switch maintains its own MAC address table. Each table also stores the MAC address of the neighboring switch's interface, because switches exchange data for control plane purposes, such as loop prevention, multicast control, and VLAN management (Figure 2).
MAC Address Learning
Because manual entry is inefficient, typing the records one by one into the configuration file is seldom done. By default, when a switch receives a data frame, it reads the frame's source address and stores it in the MAC address table, along with a reference to the port that received the frame. This process is called MAC address learning. When the switch is booted up in the very beginning, it has no records in the MAC address table, so the switch will do its delivery job by broadcast. As traffic begins to arrive from different ports, the switch learns MAC addresses. The number of MAC address table records grows, and eventually the frame will start delivering data directly, rather than by broadcast.
A typical aging time for a MAC record is 300 seconds; if a switch does not receive any data frames from a source for 300 seconds, it assumes that the MAC address owner is no longer attached to the network, and the record is cleared.
Vulnerability
You may have noticed that this default MAC address learning process does not contain an authentication step. Any host connected to the switch can interrupt the MAC address table records by sending data frames, and the switch cannot verify the authenticity of the frame's source MAC address. In the following example, I introduce three common attacks that work by sending a data frame with a fake source MAC address. You can easily find tools on the Internet to launch this kind of attack. These tools are also available through Linux penetration testing distros, such as Kali Linux [1].
MAC Flooding Attack
Space is limited in the switch's MAC address table. The maximum number of records ranges from several thousand for entry-level models to hundreds of thousands for advance models. What happens if the MAC address table is full? Depending on the coding of the switch's operating system, three possible results are:
1. Old records are removed immediately to free up space for learning new MAC addresses.
2. The switch stops learning new MAC addresses until old records are flushed.
3. The system halts.
Hackers may hope to see results 1 and 2, because the resumption of broadcasts gives the intruder a chance to capture sensitive information.
You can check the maximum capacity of a switch's MAC address table by using the switch's operating system. For Cisco IOS, use the following command to check the MAC address table's available space:
SW#show mac address-table count Mac Entries for Vlan 1: --------------------------- Dynamic Address Count : 3 Static Address Count : 0 Total Mac Addresses : 3 Total Mac Address Space Available: 6021
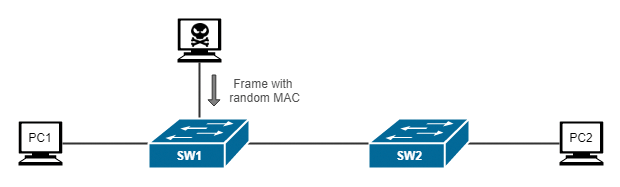
In a MAC flooding attack, an attacker attempts to generate a large number of data frames with different MAC addresses (generated randomly) and send them to the switch (Figure 3). The switch learns every single frame's source address and stores the addresses in the MAC address table until it is full.
You can use macof [2], which is preinstalled on Kali Linux, to implement the MAC flooding attack. Simply open the command console and type
macof -e [interface]
to start the attack. Listing 1 generates random MAC addresses and sends them out to the interface.
Listing 1: Generating random MAC addresses
root@kali:~# macof -e eth1 e3:8b:88:3:b4:cd d8:25:98:35:61:87 0.0.0.0.9537 > 0.0.0.0.18576: S 1905213613:1905213613(0) win 512 91:33:3b:3:a0:f5 d6:11:53:f:5e:c8 0.0.0.0.8066 > 0.0.0.0.49105: S 428779274:428779274(0) win 512 c4:27:40:74:3d:11 b9:a5:d3:1d:e:bf 0.0.0.0.8772 > 0.0.0.0.42343: S 1206065071:1206065071(0) win 512 9a:d7:d9:6a:fd:ee 9b:e8:7:15:e4:1d 0.0.0.0.44381 > 0.0.0.0.7072: S 352131538:352131538(0) win 512 42:33:77:69:9b:65 ef:3b:4c:19:e2:bd 0.0.0.0.24920 > 0.0.0.0.19837: S 1039619585:1039619585(0) win 512 a:60:b2:3d:fc:af d3:7c:5b:36:4a:61 0.0.0.0.17578 > 0.0.0.0.4432: S 727135709:727135709(0) win 512 18:75:26:4c:a8:23 10:81:2a:12:e1:be 0.0.0.0.42271 > 0.0.0.0.61161: S 1071867223:1071867223(0) win 512 98:15:eb:38:f3:c1 c8:d7:c1:61:be:a3 0.0.0.0.30693 > 0.0.0.0.57646: S 1759104040:1759104040(0) win 512 dc:6d:43:15:be:52 99:19:41:22:4e:36 0.0.0.0.29211 > 0.0.0.0.63665: S 481173385:481173385(0) win 512 42:d5:ac:47:75:fd 2:3c:f5:3a:29:b0 0.0.0.0.14787 > 0.0.0.0.57718: S 1888990933:1888990933(0) win 512 4d:ed:18:48:f0:f5 4b:ba:a5:66:ef:ee 0.0.0.0.54900 > 0.0.0.0.37268: S 397896255:397896255(0) win 512 <--Output Omitted-->
If you check the MAC address table count after a few seconds, you will find that all available spaces are filled by the fake records. As I mentioned before, MAC records will be deleted after 300 seconds. Consequently, the attacker may keep the program running by sending the fake MAC addresses to the network to ensure that all available switch spaces are filled up with the fake records:
SW#show mac address-table count Mac Entries for Vlan 1: --------------------------- Dynamic Address Count : 6024 Static Address Count : 0 Total Mac Addresses : 6024 Total Mac Address Space Available: 0
After all correct records are timed out and the table is full of fake records, the attacker can capture the network broadcast traffic with sniffing software using a tool such as Wireshark.
MAC Spoofing
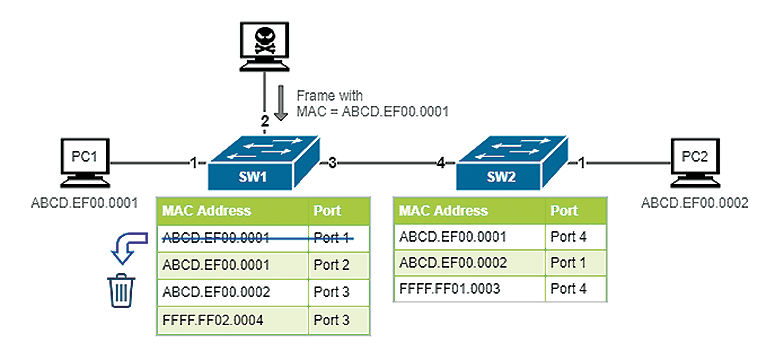
In MAC spoofing, the attacker sends a frame with the same source address as another device on the network instead of sending a random MAC address. The attacker sends out the frames with spoofed source MAC addresses frequently, say more than 10 frames per second, to ensure always winning the MAC address table completion. All the frames that should be sent to the victim will then go to the attacker, because the network switches have the wrong records in their MAC address tables (Figure 4).
The Ettercap [3] utility, also available on Kali Linux, is often used to launch a MAC spoofing attack. First, you launch Ettercap (Figure 5). Next, select Sniff | Unified Sniffing to identify the attack interface (Figure 6), followed by Hosts | Scan to scan for hosts. Then, choose Hosts | Hosts to see all the hosts attached to the network. Finally, select Mitm | Port Stealing to start the attack (Figure 7).
Man-in-the-Middle Attack
A man-in-the-middle attack, an advanced version of MAC spoofing, also lets the attacker receive data intended for the victim. The attacker simultaneously relays the messages to the victim, so the victim does not know anyone else is listening. The beauty of this type of attack is that all users can access the network as usual and neither the source nor the destination node have any indication of the attack. If an attacker pretends to be an Internet gateway, all traffic flows through the attacker's device; he or she can observe every connection, look into the packet contents, and analyze users' behaviors. Even with SSL encryption, commonly used in Internet connections, attackers have found ways to work around the protection through social engineering. For example, the attacker could send phishing email to the victim that appears to come from a familiar website.
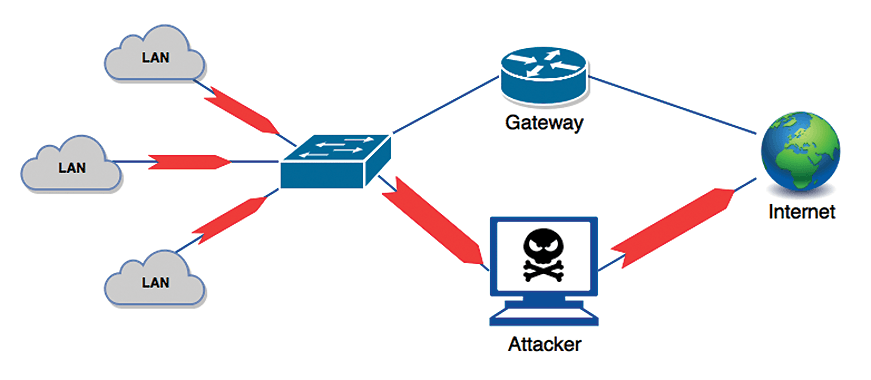
In addition to enabling surveillance, this kind of attack allows the attacker to change the network's entire traffic pattern (Figure 8). Changes in the traffic path can also bypass the enterprise firewalls and causes LAN hosts to lose virus and malware protection. The attacker may also redirect the traffic by using a rogue DNS server to a fake web server that will collect private information.
Port Security
To protect the MAC address table from attack, you can enable the port security feature [4] on a switch so that only authorized MAC addresses are allowed to attach to the switch. I will use Cisco IOS as an example here.
To change the switch port to access mode and enable the port security feature, you use the following commands:
Switch(config)#interface FastEthernet 0/1 Switch(config-if)#switchport mode access Switch(config-if)#switchport port-security
Then, statically add the authorized MAC address to the port.
Switch(config-if)#switchport port-security mac-address ABCD.EF00.0001
From now on, only the host with a MAC address equal to ABCD.EF00.0001 can attach to the switch port FastEthernet 0/1. If any hosts with unauthorized MAC addresses are plugged in to the port, an error message appears, and the port will be put into an errdisable state. No traffic is allowed to pass through until the network administrator resets the port.
However, an enterprise network may have thousands of network ports. The network administrator will be late for lunch logging in to the switch and resetting the port every time someone plugs in an unauthorized device. You can tell the switch to reset the port automatically after some predefined time:
Switch(config)#errdisable recovery cause psecure-violation Switch(config)#errdisable recovery interval 600
sticky
Configuring MAC address entries may be another reason why a network administrator is late for lunch. Compared with one-by-one manual input, sticky is a more scalable setting. By enabling the port security sticky feature at the switch port, the switch will automatically add the first MAC address that connects the port to the configuration file. Use the following command to enable sticky:
Switch(config-if)#switchport port-security mac-address sticky
In some situations, you may need to configure port security to allow more than one MAC address to connect to a port. For example, you may need to add a small switch temporarily for a group of users to share a port. If so, you'll need to increase the maximum accepted MAC addresses for the port that will connect to this new switch from a default value of 1 to the number of connected devices. Remember that the switch itself will need to communicate with other switches, so the total number of new MAC addresses should be the number of hosts plus one.
Switch(config-if)#switchport port-security maximum 5
802.1X
Another approach to port security is implemented through the IEEE 802.1X network standard [5], which is a scalable, wired network authentication solution for port-based network access control. As shown in Figure 9, the client device (supplicant) requests to attach to the switch port by using the Extensible Authentication Protocol (EAP). The EAP message includes authentication information such as username, password, MAC address, or even digital certificate. When the switch (authenticator) receives the request, it sends the credential to an authentication server, which may be a Remote Authentication Dial-In User Service (RADIUS) server or an agent that connects to an Active Directory server. Finally, the authenticator allows the request if the provided information is validated.

Conclusion
Although wireless connections are very common nowadays, wired networks are still widely used for commercial office networks because of their high speed, stability, and security. The basic design of the wired Ethernet network puts the security on the perimeter and assumes all users on the local network are trusted. An intruder who is able to attach to a switch within the local network can easily gather information for an attack – unless you implement some form of port security. Individual port security configuration should be used on small- to medium-sized networks. For a large network infrastructure, you might want to consider the more scalable 802.1X authentication solution.
