
Windows 10 Updates with WSUS
Medicine Cabinet
Windows Server Update Services (WSUS) is installed as a server role on Windows Server 2016. To be able to install Windows 10 updates, including upgrades such as the Anniversary Update (Redstone 1, Windows 10 v1607), you also need to complete some settings in the WSUS management console. Additionally, you need to add the new Group Policy templates (ADMX files) for Windows 10 v1607 [1] to your network. These are available for Windows Server 2012 R2 and 2016. The new ADMX files provide far more setting options than the default options in Windows Server 2016.
It is particularly important that the WSUS server have the latest updates; otherwise, the installation files for the Windows 10 updates will fail. In particular, decrypting the ESD files on the WSUS server with Windows Server 2012 R2 causes problems. Microsoft has addressed the issue in the Knowledge Base [2]. For Windows Server 2012 R2, the KB3095113 [3] update also plays an important role; therefore, install the necessary updates on the servers. When distributing Windows 10 updates, Windows Server 2016 is usually less troublesome than its predecessors.
WSUS's problems with Windows Server 2012 R2 when distributing Windows 10 updates mostly relate to the WSUS console being unable to connect to the server as soon as certain updates are installed. You can typically run the following command at the command line to resolve this:
> C:\Program Files\Update Services\Tools\wsusutil.exe" postinstall /servicing
Additionally, you need to install the HTTP Activation feature via the Server Manager – you will find it in the .NET Framework 4.5 features. Even if the feature causes problems, you should install it; otherwise, the Anniversary Update and its successor cannot be distributed on the network.
Setting up WSUS and Configuring Group Policies
Windows 10 is generally connected to WSUS as it is to Windows 7-8.1. You can therefore use the same default settings as with previous versions. Also, more options are available for Windows 10, which you should use with WSUS. The previously mentioned Group Policy templates are necessary to use the new features. Copy them onto the domain controller (DC) or onto the local computer, which then lets you manage the Group Policies. After that, WSUS and Windows 10 collaborate in a far better way.
You need to adapt the owner of the directory and the permissions so that the new ADMX files can be copied to the C:\Windows\PolicyDefinitions directory on the DC and the server on which the policy is edited. Also be sure to copy the ADML files to the appropriate language subdirectory (e.g., en-us for American English).
The new functions for managing Windows 10 v1607 updates are now also available in Windows Server 2016. You will find the Computer Configuration | Policies | Administrative Templates | Windows Components | Delivery Optimization menu item on servers with Windows Server 2012 R2/2016.
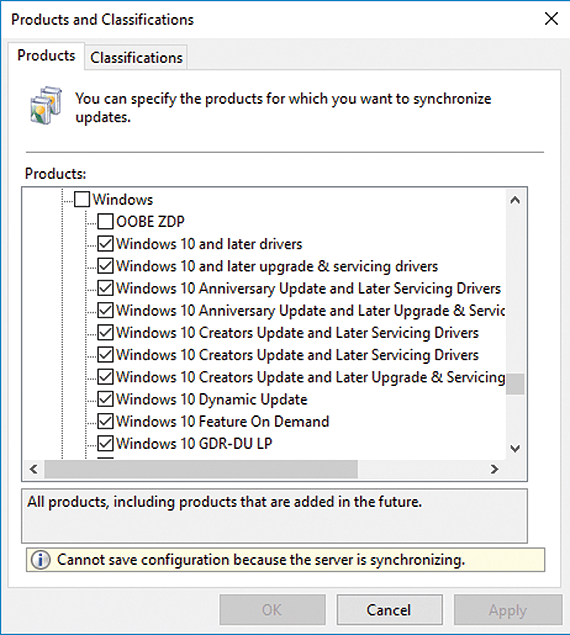
Then, in the management console's WSUS options, enable the Upgrades menu item below Products and Classifications in the Classifications tab. After doing so, updates, such as the Windows 10 v1607, can be distributed via WSUS. After changing these settings, resynchronization is required. In the WSUS options, you will also want to enable the various menu items for Windows 10 below Products and Classifications in the Products tab. The Windows 10 Anniversary Update and Later Servicing Drivers setting is especially important for distributing the Anniversary Update, but the other Windows 10 options also play a role (Figure 1).
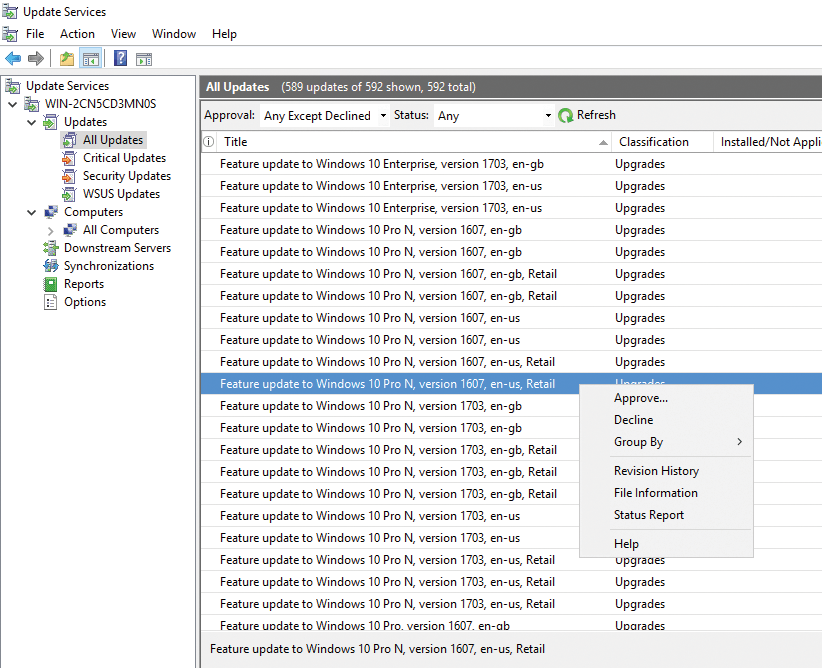
After WSUS has synced, the various Windows 10 updates appear in the console's All Updates field. You will also find the Anniversary Update here. When approving the Anniversary Update, you also need to confirm the compulsory license terms, but this is a once-only action. Then the update can be distributed. This will also work in a similar way for the next major updates for Windows 10.
Grouping Computers
For Windows 10 updates, it may make sense to create different computer groups in WSUS and add the computers via Group Policy Object (GPO). This helps to distribute major updates, like the Anniversary Update, and to conserve the network's resources in a better way. This means that updates are rolled out gradually and not to all computers at the same time. In the Computers menu item, you can see all the connected computers below Unassigned Computers in the WSUS console. You will want to create a separate group of computers for Windows 10 computers here. Use the context menu to create the group and add members to it. Once you have created the group and set up the Group Policy so that Windows 10 computers receive updates from WSUS, Windows 10 updates can be approved in the Updates section. Synchronizing before doing this is important.
Once all the computers are assigned, you can choose the computer groups in which to install the updates with the Patch Approval Wizard. Within the groups, you can immediately see from each computer's context menu whether or not the patches are installed. To manage the settings via Group Policy, use the options below Computer Configuration | Policies | Administrative Templates | Windows Components | Windows Update. Using the Enable client-side targeting setting, you can choose to which computer group computers will be assigned when they are connected to WSUS. Additionally, enable the Use Group Policy or registry settings on computers option in the Options | Computers section of the WSUS management console. Incidentally, the definition updates for Windows Defender can also be distributed to workstations and servers via WSUS. It is important to release the Windows Defender updates for Windows 10 and Windows Server 2016 here.
If you want to use the reports in WSUS, the Microsoft Report Viewer 2012 Runtime tool [4] must be installed on the server. In addition, the common language run time (CLR0 types for SQL Server 2012 [5] are required on the server. To display update reports, click on Reports in the left panel of the WSUS management console and then the Update Status Summary option. Then filter the resulting list based on your desired criteria. Next, click Run Report in the window's toolbar. You can then save or print the reports as Excel spreadsheets or PDFs. To do so, click on the save icon in the toolbar.
Using SSL in WSUS
By default, WSUS uses HTTP to communicate with the client and the management console. In security-sensitive environments, you will want to enable SSL; this also makes sense for the Windows 10 connection. To do this, you first need to install a certificate on the server. Use a similar approach to installing server certificates in IIS Manager. You can also use an internal certification authority.
After you have installed the server certificate, call Sites | WSUS Administration in the IIS Manager. Click on Edit Bindings to edit the binding for SSL to port 8531. You can now select the installed certificate. Additionally, you need to call the SSL settings for the following subordinate directories of the WSUS administration tool:
- ApiRemoting30
- ClientWebService
- DssAuthWebService
- ServerSyncWebService
- SimpleAuthWebService
and then enable the Require SSL checkbox. After you have enabled SSL for WSUS, you will receive an error message when you open the WSUS management console. For the console to work again, first open a command line and change to the C:\Programs\Update Services\Tools directory. Then type the following command:
> wsusutil ConfigureSSL certificate name
In the next step, remove the obsolete HTTP connection in the WSUS management console and add a new connection from the context menu. Type in the server name and the correct port number to connect to SSL. Also enable the Use Secure Sockets Layer (SSL) to connect to this server checkbox. After connecting to the server, click on the server name in the console. In the Connection field at the bottom, you will see that it now uses SSL to communicate.
Be sure to add Port 8531 to the Group Policy for the client connections. The HTTP port 8530 is no longer available. You will find the settings in Computer Configuration | Policies | Administrative Templates | Windows Components | Windows Update. Modify the Specify intranet Microsoft update service location setting when you get there.
Connecting Windows 10 Computers
For the Windows 10 clients to be able to download and install updates from WSUS, they must be configured so that they do not download patches off the Internet but rather use the internal WSUS. Nothing has changed in Windows 10 compared with its predecessors. WSUS does not automatically distribute the patches to clients. Instead, it only downloads the updates from the Internet and makes them available as soon as you approve the installation. The clients get the patches from the WSUS server and install them automatically, depending on the local settings or the settings in the Group Policy. These settings are part of the basic principles for the distribution of Windows 10 updates. You can configure the automatic updates in the Group Policy Management Editor below Computer Configuration | Policies | Administrative Templates | Windows Components | Windows Update.
Workstations can be configured so that they automatically download and install updates from WSUS. The first option for this is Specify intranet Microsoft update service location. Enable this option to connect Windows servers and workstations to WSUS. Since WSUS is a web application, you need to use an HTTP address to specify the server name: http://Servername:Port. WSUS can, as previously mentioned, also use HTTPS. The second important option is the update behavior, which you can determine via Configure Automatic Updates. The following options are available:
- Notify for download and notify for install: Windows notifies users before downloading and installing the update.
- Auto download and notify for install: The client will automatically download the updates; however, installation does not automatically take place. This setting is suitable for servers.
- Auto download and schedule the install: The client is automatically provided with the necessary updates and installs these at a specified time. If the clients are not switched on at this time, Windows starts updating at the next launch.
- Allow local admin to choose setting: Allows local administrators to select the configuration settings themselves.
Checking the Connection to WSUS
To check whether a computer is successfully connected to WSUS and the settings are working in your Group Policy, just run rsop.msc as an administrator on the computer. The settings for the Group Policies are shown in the window. After configuring the Group Policy, it may take some time for the workstations and servers to connect to WSUS and appear in the WSUS management interface. On the individual computers, you can force an immediate connection to WSUS at the command prompt by entering:
wuauclt.exe /detectnow
If the client is not yet connected, enter
gpupdate /force
and then:
wuauclt.exe /reportnow /detectnow
As soon as a Windows 10 computer is connected to WSUS, the Check online for updates from Microsoft Update link appears in the local update management tool. This link does not appear without a connection to WSUS, because updates are otherwise installed over the Internet.
In the WSUS console, you can select and approve several updates in a single step via the context menu. Select the Windows 10 group here. Some Windows 10 upgrades are also available via the All Updates menu item (i.e., the ability to run function updates on Windows 10 computers). With some updates, such as Windows 10 v1607, you need to confirm the license terms centrally only once. As soon as updates for Windows 10 become available, the Windows 10 computer starts searching for them and installs them in line with the configured policies. It can of course take a few minutes for the installation to complete. Information relating to this will appear when you double-click on a computer in the Windows 10 computer group. You can see here whether or not it was possible to install the updates.
Configuring Group Policies for Windows 10
If you have installed the new ADMX files for Windows 10 v1607 on the DCs, you can complete the adjustments for Windows 10. The Computer Configuration | Policies | Administrative Templates | Windows Components | Delivery Optimization menu item plays a special role here. In particular, you need to adjust the Download Mode and the bandwidth so that Windows 10 computers can efficiently download updates without using too much bandwidth.
The Bypass option can be a useful Download Mode and applies to Windows 10 computers that are not connected to WSUS. Enabling the Bypass option means that the new download mode is passed over and BITS technology is still used. This option also fixes download problems for Windows 10 without the use of WSUS and prevents Windows 10 machines hogging your network's entire bandwidth and Internet connection during updates. However, you should also check and adjust the values (all KBps) in Maximum Download Bandwidth, Max Upload Bandwidth, and Minimum Background QoS.
To protect the WSUS server, Windows computers can also pass on updates to each other. You thus have the option of controlling the distribution of Windows 10 machine updates to other computers at the same Active Directory site. On request, you can create separate groups (e.g., for small offices). During the corresponding configuration, Windows 10 machines exchange updates between these groups without WSUS. More on this later.
Microsoft has completely changed the management of updates in Windows 10. You can roll back installed updates via group policies in Windows 10 Pro and Enterprise editions, which mainly affects new features and regular updates, but not security patches. You will find the setting in Computer Configuration | Policies | Administrative Templates | Windows Components | Windows Update | Defer Upgrades and Updates. These options are only available if you have installed the new Windows 10 Group Policy templates (Figure 2).
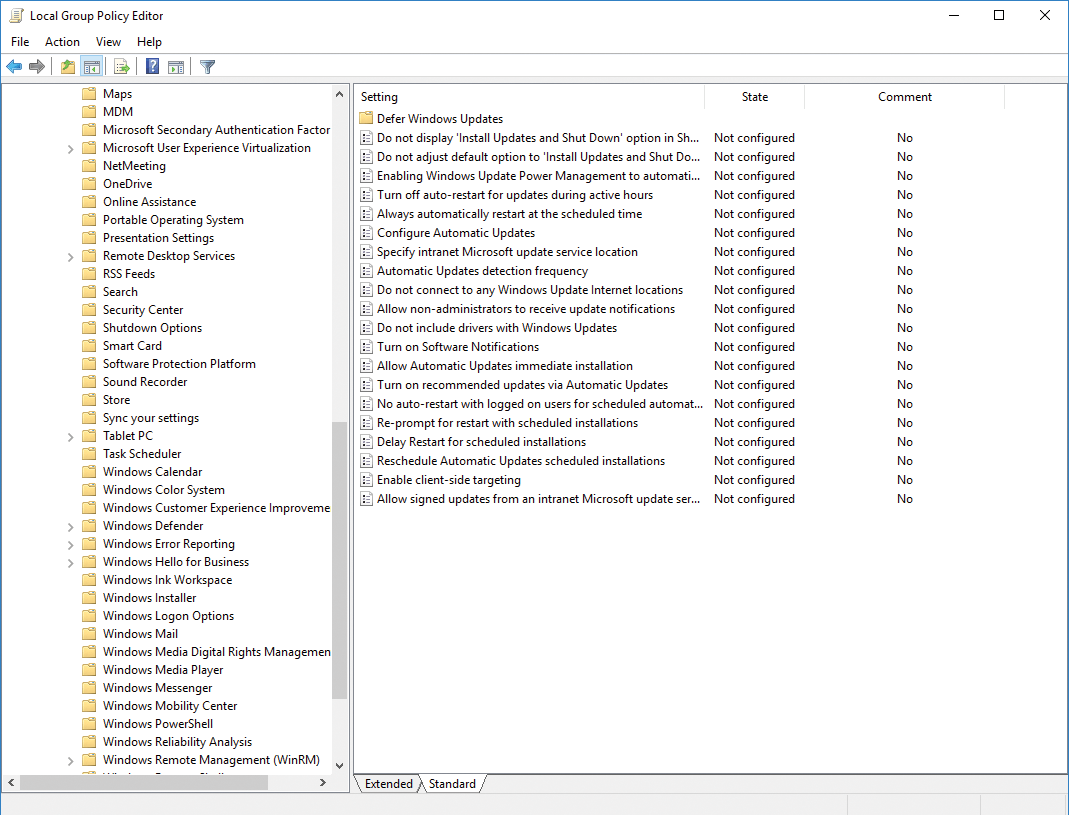
This field lets you choose to install Windows 10 updates with new features with a delay of up to 180 days. To do this, set the Select when Feature Updates are received value to Current Branch for Business and, for example, 180 days. This is the maximum delay period.
Turn off auto-restart for updates during active hours can be set for Windows 10 so that the computer does not reboot within the specified times. Additionally, you can prevent Windows 10 and Server 2016 from installing drivers via Windows updates by selecting Do not include drivers with Windows Updates in the Computer Settings | Administrative Templates | Windows Components | Windows Update settings.
Using Peer-To-Peer or Upstream Servers
As mentioned, Windows 10 computers can deploy updates for other Windows 10 computers on the network and even on the Internet (peer-to-peer). The advantage of this is that not every computer in your branch offices needs to download its updates from Windows Update or from a WSUS server. Instead, it can source the updates from other computers on the same network. The settings for this can also be found in Windows 10 without Group Policies under Settings | Update and Security | Windows Update | Advanced Options | Chose how updates are installed.
If you use multiple WSUS servers in the enterprise, it is not necessary for all these servers to synchronize with Microsoft. Instead, you can establish an upstream server, from which other WSUS servers source their updates. If so desired, you have the option of not only synchronizing the updates, but also the settings. By doing so, you can install a single WSUS server and set up and distribute its data and patches to other WSUS servers throughout the enterprise. This is useful as an alternative to peer-to-peer distribution of Windows 10 on the network. For the settings in this area, go to the Update Source and Proxy Server options. You can also configure the updates via proxy servers here, of course, with the option to provide a username and password.
Once you have set up the source WSUS server, call the Options | Update Source and Proxy Server on the lower level WSUS servers. Enable the Synchronize from another Windows Server Update Services server option. If you have not configured SSL, enter the server name and port 8530 in the window. If you already use SSL, use the appropriate port.
In the window for configuring the upstream server, you can stipulate that the lower level WSUS servers also receive the settings from the parent server. To do this, enable the This server is a replica of the upstream server option. After you have enabled this option, you do not need to release any updates to the lower level servers because this option is also synchronized. After several hours, the servers should be synchronized. You can see the lower level WSUS servers in the Downstream Servers field of the WSUS management console. In this section, you can add the server to the current management console and also manage multiple servers in this way in a WSUS console.
Create Your Own Custom Patch CDs
Administrators who often install Windows clients or servers (e.g., also for pilot environments) need to download and install any necessary patches either via WSUS or Windows Update for each manual installation (see the "Integrating Office Updates in Windows 10" box). The process can extend the installation time significantly, especially on slower Internet connections. If you want to set up more than one computer, it can take hours for the servers or workstations to update. In these cases, it makes sense to use an update CD/DVD or ISO file with all the important patches that can be installed automatically in one fell swoop. You could also create a USB stick.
The WSUS Offline Update [6] freeware tool helps with this process (Figure 4). The tool automatically downloads the WSUS catalog file from Microsoft and then all the patches that you selected. You don't have to install the tool; simply launch it. The current version supports Windows 10 and Windows Server 2016. However, Windows XP and Server 2003 are sidelined. With the free tool, if necessary, you can load all existing updates for Windows 10 and Windows Server 2016 in a single action and create an ISO file. You can then either burn this file onto a disk or deploy it on a server then launch the upgrade. All the patches are installed using a wizard. On request, the wizard can reboot or shut down the server after the update.
To launch the tool, call the UpdateGenerator.exe file. After the launch, you can determine which Windows versions you want to download updates for in the Windows tab. The current version supports Windows 10 and Windows Server 2016. Once you have selected the products, you can specify several options in the lower directory. The options are self-explanatory. It makes sense to enable the Include C++ Runtime Libraries and .NET Frameworks and the per selected product and language option under Create ISO image(s). The advantage of this is that you can also use the ISOs with virtual servers. On traditional servers, you can simply save the downloaded updates to a USB flash drive. You can also specify whether you want to download just 64-bit patches (x64 Global) or updates for 32-bit computers (x86 Global).
If you don't want to download the updates directly via Windows Update, but rather on the basis of an existing WSUS server, you can enter the URL of a WSUS server by clicking the WSUS button. When you press Start, the tool downloads the patches and, on request, creates the ISO files for the update.
To update a server or workstation with WSUS Offline Update, either mount the ISO file, burn it to a CD/DVD, or copy the contents of the \wsus-offline\client directory to a USB stick. You will find all tool updates, as well as the necessary installation files, in this folder. This directory is also considered when creating ISO files. Launch the update using the UpdateInstaller.exe tool, which launches a graphical interface that lets you specify how the update is performed.
In addition to WSUS Offline Update, another free tool lets you update Windows and other Microsoft products: Get WSUS Content .NET [7]. After downloading, first unpack the archive; then, launch setup.exe. The tool checks whether all conditions are in place on the PC.
Updates from Command Prompt and PowerShell
In Windows 10 and Windows Server 2016, you can install and uninstall updates at the command prompt or with PowerShell and the wusa.exe tool:
> wusa.exe MSU_patch_file /quiet /norestart
The /quiet option installs without feedback; the computer does not reboot when you stipulate the /norestart option, even if the patch requires this. You can remove updates with the /uninstall option:
> wusa.exe /uninstall /kb:knowledgebase_number_of_patch
You can also display the installed updates in the command prompt on Windows 10 and Windows Server by entering:
wmic qfe
Installed updates can also be displayed in PowerShell with the Get-Hotfix cmdlet,
> Get-Hotfix -computername Name
which not only displays the local computer updates, but also updates that are installed on computers on the network.
Conclusions
Updates are distributed in Windows 10 much as in previous versions. However, many new features and setting options play an important role in WSUS with Windows Server 2012 R2 or Windows Server 2016. Administrators should consider the new Windows 10 settings and plan the distribution of large-scale Windows 10 updates well to avoid overloading the network.
