
Monitor Active Directory with Azure AD Connect Health
Fitness Routine
The monitoring focus of Azure Active Directory Connect Health [1] is the Azure AD Connect servers that synchronize data from Active Directory (AD) with Microsoft Azure. Information and performance data from local domain controllers (DCs) also are monitored and displayed in the web interface. In addition to modern operating systems such as Windows Server 2016 and 2012 (R2), you can connect Server 2008 R2 Active Directory Federation Services (AD FS) servers and DCs. The service does not target companies that do not use Microsoft Azure and Azure AD, however.
Where organizations synchronize usernames and passwords between different forests and the Azure AD, the tool provides detailed insights into whether the data is replicated properly. This kind of tool is necessary to provide synchronization support, especially when using multiple DCs, sites, and domains, because it keeps an eye on server data and performance information and notifies you in case of problems. Because monitoring takes place in the cloud, enterprises do not need their own server infrastructure for the service. Instead, the data is transferred via an agent that is installed on the servers. Last but not least, the service ensures superior security, because unsuccessful and failed login attempts against Azure AD and AD FS can be logged.
Monitoring Local and Azure AD
Hybrid deployments with Exchange and Office 365, SharePoint, and SharePoint Online in Office 365 also can be monitored. Wherever authentication against Azure AD is intended and an exchange of usernames and passwords with a local AD occurs, you need to create an option for verifying the exchange of the authentication data, in particular for local changes to passwords that need to be synchronized in the cloud. Even if only small volumes of data are being synchronized, problems in this area would mean that users could not access critical cloud services and thus would have to turn to support and the IT department for help.
In detail, you can use Azure AD Connect Health to monitor errors in your DC connections to the cloud, the replication of data between local DCs, problems with synchronization between Azure AD and a conventional AD, and the performance of DCs with regard to authentication and replication. You can also keep an eye on AD FS, which, with Azure AD Connect Health, plays an important role in combination with cloud services.
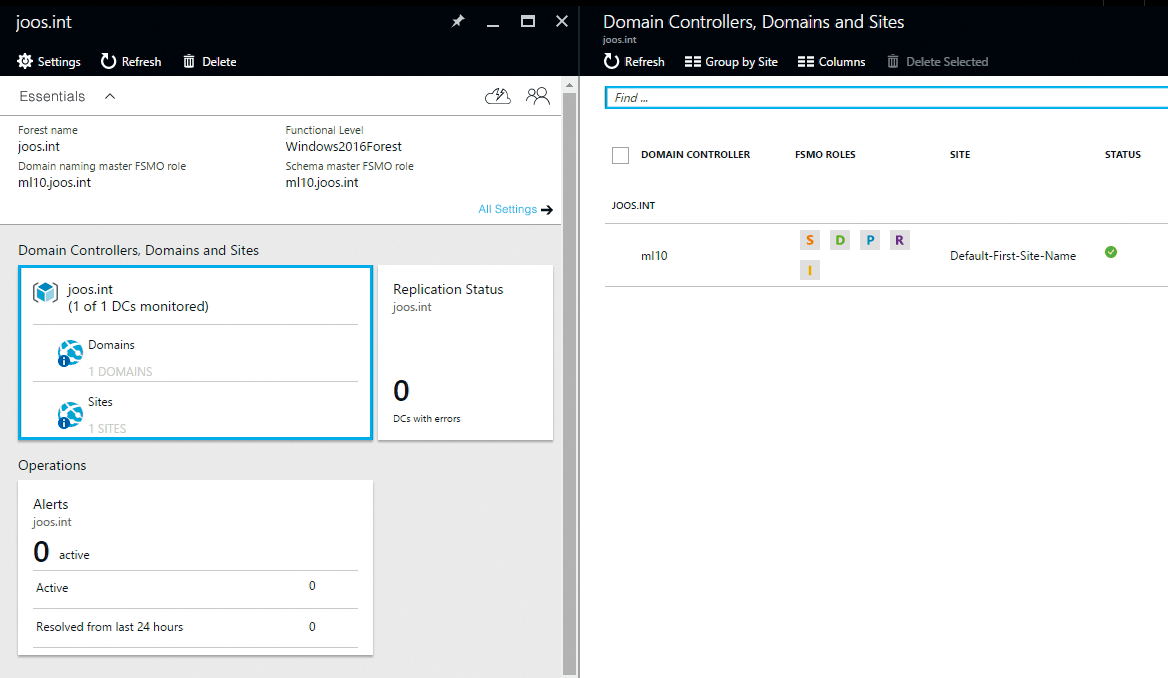
In principle, the more servers you connect, the more interesting Azure AD Connect Health becomes, because you receive a full complement of relevant information for monitoring your environment through its web portal. The service detects errors not only in the synchronization between your local network and the cloud, but also between the DCs (Figure 1). Azure AD Connect Health also can send email notifications as soon as problems arise. This keeps you up-to-date, even if you don't happen to be sitting in front of the monitoring tool.
After setting up Azure AD Connect Health, you can enable notifications via the Azure Portal in the cloud. If the local mail or Exchange server fails, the cloud portal can still deliver the email, thanks to Azure. You can specify the internal email addresses of your administrators or external addresses. Thanks to the option that all Azure administrators receive email by default, you will never forget to enable email notifications when creating new admin accounts.
Premium Subscription
To use this service, you need an Azure AD premium subscription [2]. If you want to see how the cloud service works first, you can get a trial version. The agent for Azure AD Connect Health [3] is installed on the servers in the infrastructure that you want to monitor. This process is quick and does not require complex configuration work. The agent collects the required data and sends it to the cloud. The connection is initially set up via the domain controllers on the network, which must be connected to the Internet. Because Microsoft Azure is the basis for the service, the server should already have Internet connectivity.
If you also want to monitor AD FS with Azure AD Connect Health, you need to connect your AD FS infrastructure with the agent [4]. To do so, install the AD FS proxy and web application proxy servers on AD FS; only then can you read all the AD FS data. Again, the setup is through the Azure AD Connect Health web portal. If you use AD FS and connect it to Azure AD Premium, Azure AD Connect Health offers further useful features. For example, you can read performance data and perform trend analysis and capacity planning.
Enabling Internet Communication
Because monitoring sends some data to the cloud, you need to pay attention when configuring security and communications. The following endpoints must be allowed on your enterprise firewalls, as well as in the Microsoft Azure firewall settings:
- https://management.azure.com
- *.blob.core.windows.net
- *.queue.core.windows.net
- *.servicebus.windows.net – port 5671
- https://*.adhybridhealth.azure.com/
- https://*.table.core.windows.net/
- https://policykeyservice.dc.ad.msft.net/
- https://login.windows.net
- https://login.microsoftonline.com
- https://secure.aadcdn.microsoftonline-p.com
Additionally, you need to enable the following ports in the firewalls on the servers:
- TCP/UDP 80
- TCP/UDP 443
- TCP/UDP 5671
Communication occurs between Microsoft Azure and the servers on the network on which the AD Connect Health Agent is installed. To allow this, the connections must already be working when you set up the agent. Because the configuration relies on Internet servers, advanced security for Internet Explorer is enabled. You need to allow the following URLs to be able to call the respective administration pages:
- https://login.microsoftonline.com
- https://secure.aadcdn.microsoftonline-p.com
- https://login.windows.net
- The federation server for your organization that Azure AD trusts (e.g., https://sts.contoso.com).
Setting up Azure AD Connect Health
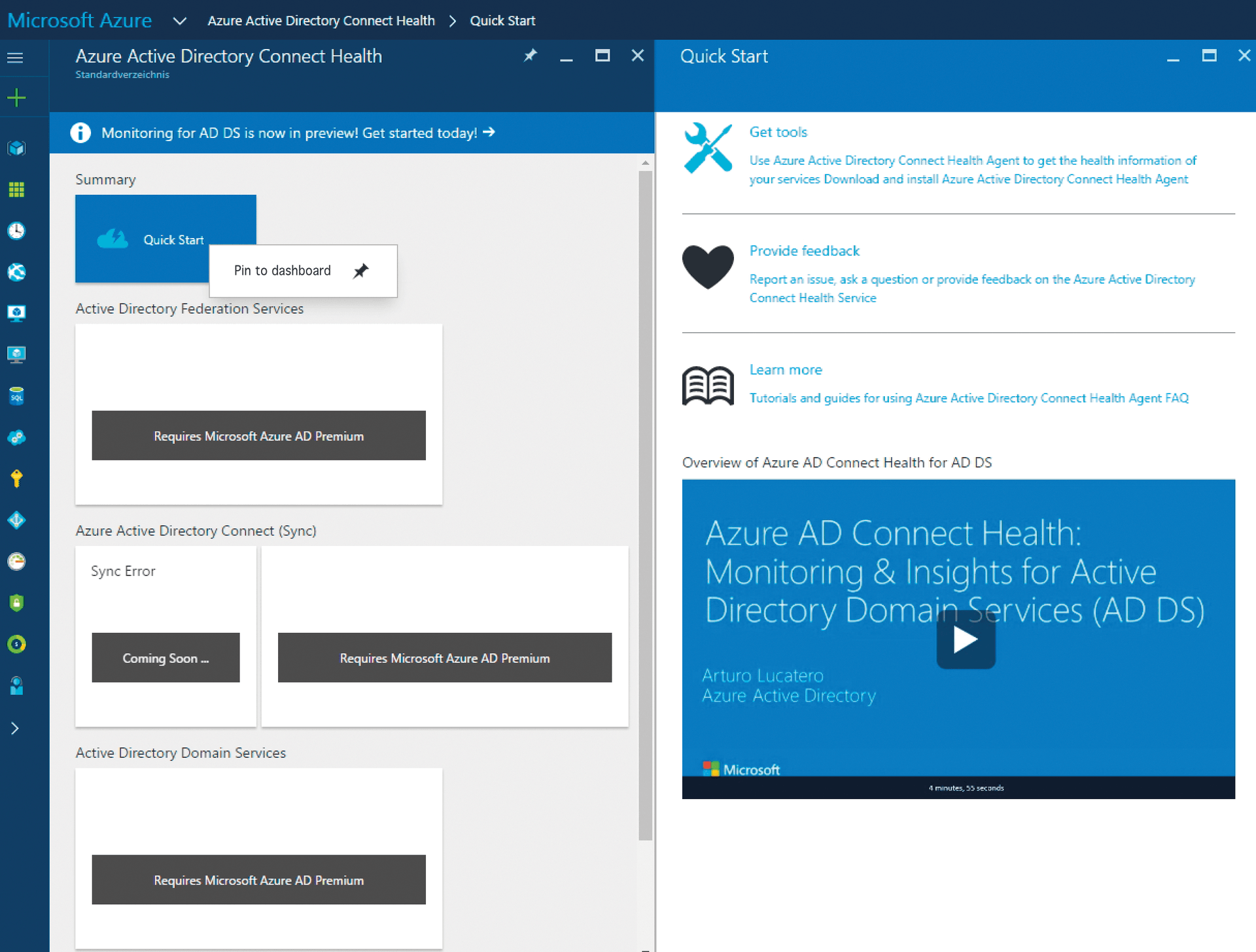
Once you have completed all the preparations, the setup of Azure AD Connect Health via the Azure web portal is next. Again, you can use a test subscription to gain insights into the service's capabilities. After pressing the plus sign to add a new resource and entering the Azure AD Connect Health search term, you will find the service in the portal. Now select the service. Detailed information about the monitoring environment will appear on the right side of the window. Click on Create to start the service setup in Azure. The Quick Start button displays the page for downloading the required tools for the connection to the local servers (Figure 2), which is also where you will find more information about configuring the service. Additionally, you can download the client directly [5].
The agent for monitoring the local domain controllers or AD FS servers must be installed (as mentioned previously) on the servers and DCs that you want to monitor with Azure AD Connect Health. During the installation of the binary files, the agent is not set up; the connection with Azure is set up later. Therefore, the best approach in a production environment is to install the agent on all your DCs and AD Connect servers that are connected to Azure and then rely on data synchronization.
As soon as the agent is installed on a server, you can call the Setup Wizard, which ensures the connection to Azure AD Connect Health. To set up the service, you thus need a connection to the Internet and Azure. The setup comprises two steps: (1) install the agent on the servers and (2) connect the agents with Microsoft Azure. The Configure Now button starts the configuration, which invokes a script in PowerShell that sets up the integration with Azure AD Connect Health.
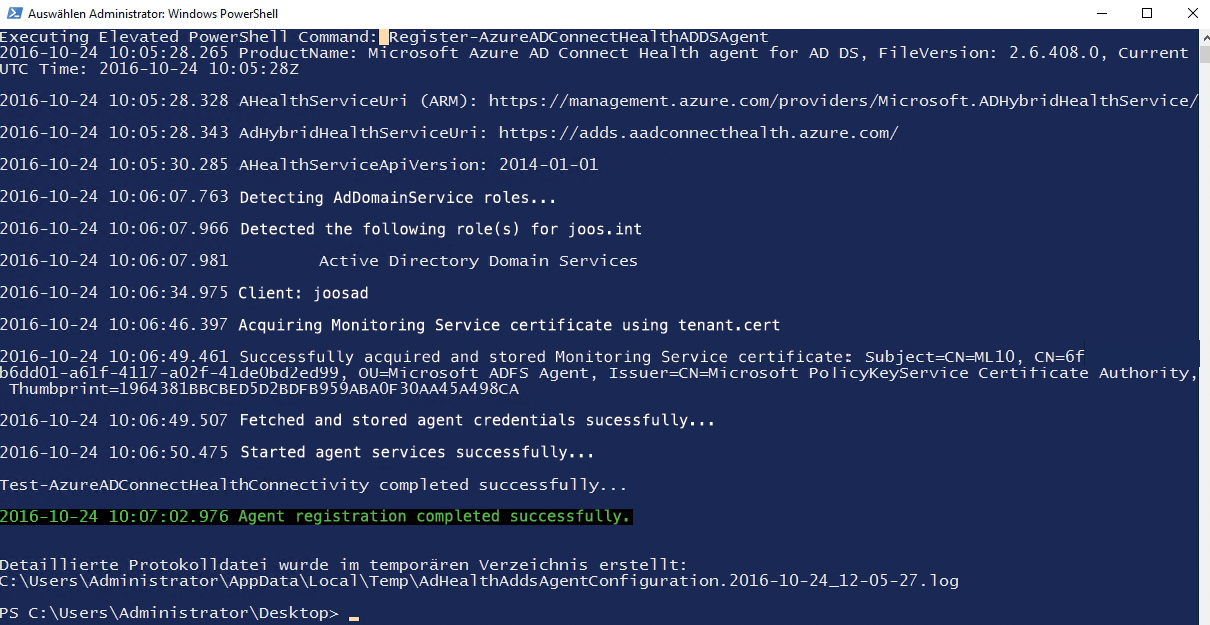
You can script the setup directly via PowerShell with the Register-AzureADConnectHealthADDSAgent cmdlet (Figure 3). For the integration, you need to log on to your Azure subscription. This can only be done with a business account or an account in Azure AD Premium. You cannot log in with a Microsoft account. The script also creates a logfile, in which you will find any errors that occurred during the setup. The script cannot be terminated during execution, but you can restart it at any time.
Troubleshooting Setup Errors
After successfully completing the setup and running the script, the integration is complete. If you receive any error messages, use the command
> Register-AzureADConnectHealthSyncAgent -AttributeFiltering $false -StagingMode $false
If you are setting up the connection to a core server, you cannot log in from a browser – only from PowerShell. In this case, the command is:
> Register-AzureADConnectHealthADDSAgent -Credential $cred
In the scope of the setup, the wizard creates three system services that must be started to transfer data to the cloud: Azure AD Connect Health AD FS Diagnostics Service, Azure AD Connect Health AD FS Insights Service, and Azure AD Connect Health AD FS Monitoring Service. If you want the agent to use a proxy server to access the Internet, the easiest way is to define the proxy settings in Internet Explorer and import them using PowerShell:
> Set-AzureAdConnectHealthProxySettings -ImportFromInternetSettings
You can also specify the proxy directly in PowerShell:
> Set-AzureAdConnectHealthProxySettings -HttpsProxyAddress <Server or IP Address>:<Port>
In PowerShell, you can test the successful integration with Azure AD Connect Health. To verify the connection to AD, use the command:
> Test-AzureADConnectHealthConnectivity -Role ADDS
The ADFS role would let you test the connection between AD FS and Azure AD Connect Health. Next, type
> Test-AzureADConnectHealthConnectivity -Role Sync -ShowResult
to test synchronization with Azure AD.
Delegating Permissions
The service is managed and used via the Azure AD Connect Health web portal. You can reach this fastest by signing in online [1]. To connect servers to Azure AD Connect Health, you must have global administrator privileges. No global administrator rights are necessary for future use of the AD Connect Health dashboard, but the rights can also be delegated. To do so, press the Access icon in the main Azure AD Connect Health window or select the Users tile. In the new Users window, you manage access roles, add new users, and assign roles to users. If you mouse over the role, you can view information on the permissions this role has in Azure AD Connect Health.
Monitoring and Alerts
Once the connections between Microsoft Azure, Azure AD Connect Health service, and the agents on the local servers have been established on the network, the servers and other functions appear in the Azure AD Connect Health dashboard. You will also see any alerts and problems. Other servers can be connected with the environment in the same way. When you click on an error in the monitoring window, you are shown more detailed information on the right. After connecting your infrastructure, you can see at a glance in the Azure AD Connect Health portal whether a monitored service is causing problems. Also, you learn when the last synchronization and export operations occurred.
The Settings button gives you more information and options for each connected server. After you select a DC, the Choose Columns section gives you a selection of additional columns to display in the monitoring window. Once a server is connected, it starts to transfer performance data; of course, it may take a while before this information is visualized.
In addition to errors, Azure AD Connect Health analyzes the user logins in Azure AD. Therefore, for those applications that users authenticate through Azure AD, you can see which are used the most. Various filters are available. You can analyze the last six hours, but also the last 24 hours or the last seven days. You can also filter for authentication methods and the servers used. Although the interface is simple, it is constantly being developed by Microsoft. Complex filtering and monitoring tasks are not possible, but you can quickly and easily see whether Azure AD is working, how the service is used, and by whom. Please do not forget your users' privacy, though.
In many cases, the service detects replication problems between DCs on the local network that could affect synchronization with Azure AD. To do this, Azure AD Connect Health also shows links to solutions for the identified problems. The dashboard shows all the connected DCs, the flexible single-master operation (FSMO) roles of the servers, including the global catalogs, and the configured AD location. You can also see the status of the server in the dashboard and display further information, such as the last server update or when the server last booted. The servers can also be grouped by Active Directory locations, which improves the overview, especially in large environments.
For each connected DC, the replication connections can be displayed, along with any replication errors with other DCs. The performance of the DCs can also be monitored using various performance indicators, which helps you identify vulnerabilities and performance issues. You can also see the time periods at which your DCs are busiest. To do so, click on Performance Monitor Collection. On the right side are various filters that can provide interesting information for metrics. This information is important both for DCs that synchronize with Azure AD and for replication between servers.
Special Features for AD FS
To help with comprehensive monitoring of AD FS with Azure AD Connect Health, the service needs access to the AD FS audit logs. Some configuration work is necessary on the AD FS servers to do so. The settings are more or less identical for Windows Server 2008 R2, 2012 (R2), and 2016:
1. Open Local Security Policy in the management program group on the server.
2. Navigate to Security Settings | Local Policies | User Rights Assignment and double-click on Generate security audits.
3. In the Local Security Setting tab, make sure that the AD FS 2.0 service account is included in the list.
4. Open a command prompt window and run the following command to enable auditing:
auditpol.exe /set /subcategory:"Application Generated" /failure:enable /success:enable
5. Open the AD FS management console and click Edit Federation Service Properties in the Actions pane.
6. Make sure that the options for Success audits and Failure audits are enabled.
Conclusions
In complex infrastructures with AD, Azure AD, Exchange, and Office 365, you can find and resolve problems more quickly, thanks to Azure AD Connect Health, than with other tools or without any meaningful type of monitoring. Companies that have linked their local AD infrastructure with Azure and work with Azure AD, should take a closer look at Azure AD Connect Health.
