
Six emergency CDs from antivirus manufacturers
Life Jacket
Because of its many security weaknesses, Microsoft Windows is considered particularly vulnerable to malware such as viruses, worms, and Trojans. However, because the operating system has more or less a monopoly on the desktop, administrators in the enterprise in particular are repeatedly confronted with malware damaging Windows workstations or even rendering them unusable.
In such cases, it usually makes sense to boot the damaged computers from a removable disk and then examine the mass storage devices with an external rescue system. For this purpose, many manufacturers of proprietary antivirus and anti-malware software provide free emergency CDs that use the manufacturer's own scanners to detect and remove malware on Windows systems. In many cases, they can also be used to repair damaged system files so that the Windows system can be used again.
The rescue CDs, available for download as ISO images on the websites of the respective manufacturers, are based on Linux derivatives and, in addition to the antivirus scanners, often contain free Linux tools for creating a backup of the target systems or managing mass storage devices.
Avira Rescue System
Avira [1], a company based in Tettnang on Lake Constance, Germany, has developed over the years into a global player in the field of system security, primarily for Windows computers. Avira offers various antivirus applications for products from Redmond but has continuously expanded its portfolio in recent years to include virtual private network (VPN) services, security solutions for mobile systems such as Android and iOS, and protection software for dealing with email.
The company also offers a freely available rescue system based on Linux called Avira Rescue System [2]. The system, offered as an ISO image, focuses on damaged Windows computers. It scans target computers for malware, can repair the operating system, and supports editing the registry file that acts as the central configuration database on Windows computers. The tool does not let you repair boot sectors or modify partitions.
Additionally, Avira Rescue System also scans Linux systems for malware, which it also can remove. The hybrid image, which weighs in at around 1.2GB, can be booted both from an optical data carrier or from a USB memory stick.
Start
The system, based on Ubuntu 20.04.1 and equipped with a fairly up to date 5.8 kernel, first boots into a graphical GRUB screen that offers various startup options and settings. You can also test the RAM or check the mass storage available on the system from the corresponding menu entries. The system then boots into a modified Unity desktop, which has just a few applications in the vertical panel on the left (Figure 1). For an overview of all the installed applications, click the tile icon at the bottom of the vertical panel. The start buttons of the existing applications now appear on the desktop.

Features
The panel bar hosts a very fast web browser borrowed from the Gnome treasure trove, as well as the Déjà Dup backup program, also courtesy of Gnome, and the forensic Windows registry editor Fred. The central element of the distribution, however, is the Avira Rescue System, which you launch by pressing the umbrella icon in the top left corner of the desktop.
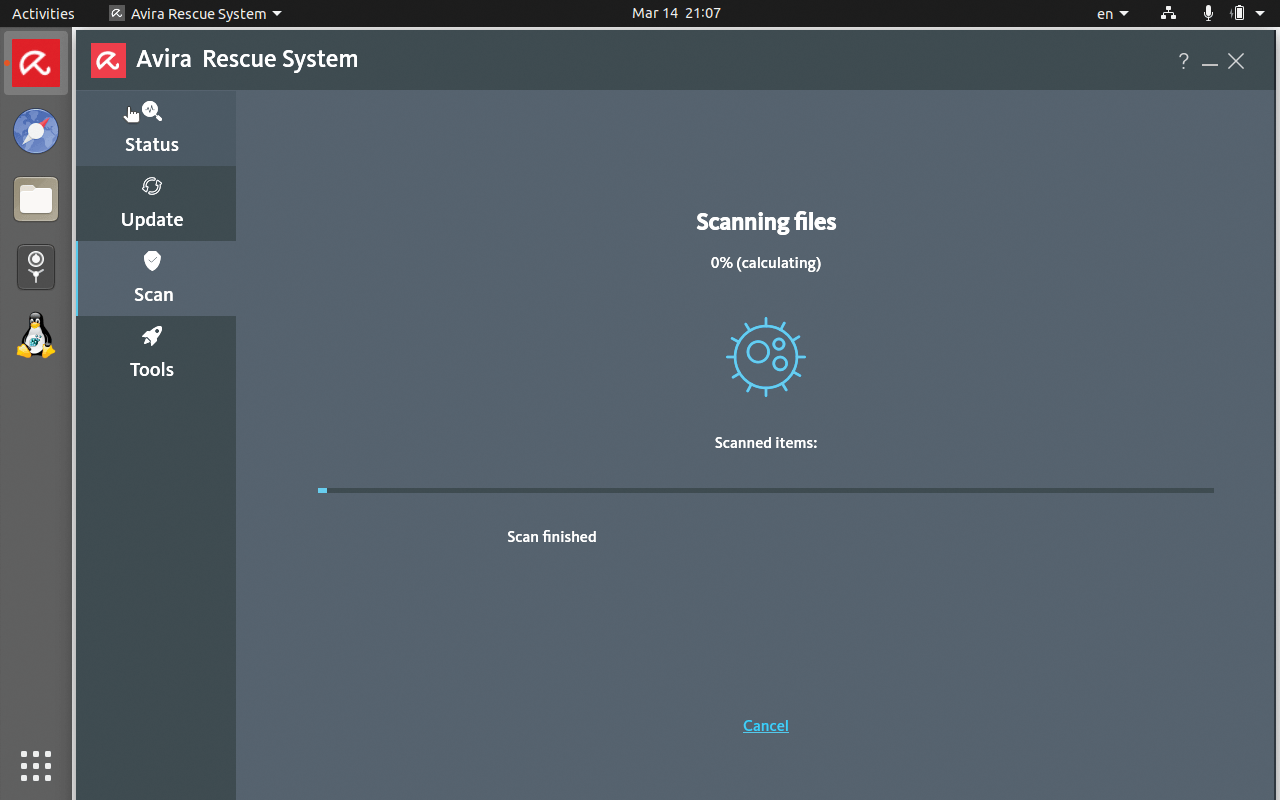
After confirming the license, the tool performs some basic configuration steps before you press the Quick scan button at bottom center to run a quick system scan. The strong focus on Windows is already noticeable in this dialog. If you launch the Avira DVD on a computer whose mass storage consists entirely of Linux partitions, the rescue system stops without any further activity in the system scan (Figure 2). With multiboot installations, the scan software fails to deliver satisfactory results. The Update dialog is also non-functional on Linux.
In the Tools dialog, in addition to the Déjà Dup backup tool, you will also find a button for calling the TeamViewer remote maintenance software. Both can also be used on Linux, although the individual versions of TeamViewer are not compatible. TeamViewer v15.15.3 included in the Avira package was the current version of the remote maintenance solution at press time.
Outside of Avira's own rescue tool, you will find the GParted graphical front end in the tile overview of the applications, which you can use to manage mass storage devices. This universal tool is useful for creating and editing partitions and drives. A terminal for executing Linux commands is also available.
On Windows
The Avira Rescue System also exhibits some minor weaknesses on Windows. After starting the tool, you must update the virus signature database. The software displays the message Detection database is outdated to let you know. After clicking Check update, it first checks whether Internet access is available. If so, a click on the Start update button updates the database and displays a message to that effect.
Next, press Start Scan to start the system scan and choose between a quick and a full scan of the Windows system. Even a quick scan of a current NVMe SSD was quite slow in the test. You will need to allow several hours for a scan, even with a freshly installed Windows on a larger partition. Afterward, any malware identified in the scan can be removed.
Comodo Rescue Disk
Comodo Rescue Disk is a rescue system for Windows computers that uses Linux tools developed in-house. The US manufacturer [3] uses the lean SliTaz Linux from Switzerland as its basis. The operating system in Comodo, developed independently from sources, comes with kernel 2.6.37 and uses the Openbox window manager. It will also run on 32-bit hardware and works frugally and quickly on all platforms. You can pick up the Comodo Rescue Disk system in the form of a hybrid ISO image [4] of only about 55MB, which then runs from a USB flash stick or CD-ROM.
Software
Comodo Rescue Disk only includes a small software inventory. The central element that stands out is Comodo Cleaning Essentials (CCE), a collection of GUI tools for removing malware from Windows systems. CCE loads automatically after booting the system and first updates the signatures; then, a wizard opens to scan the Windows system.
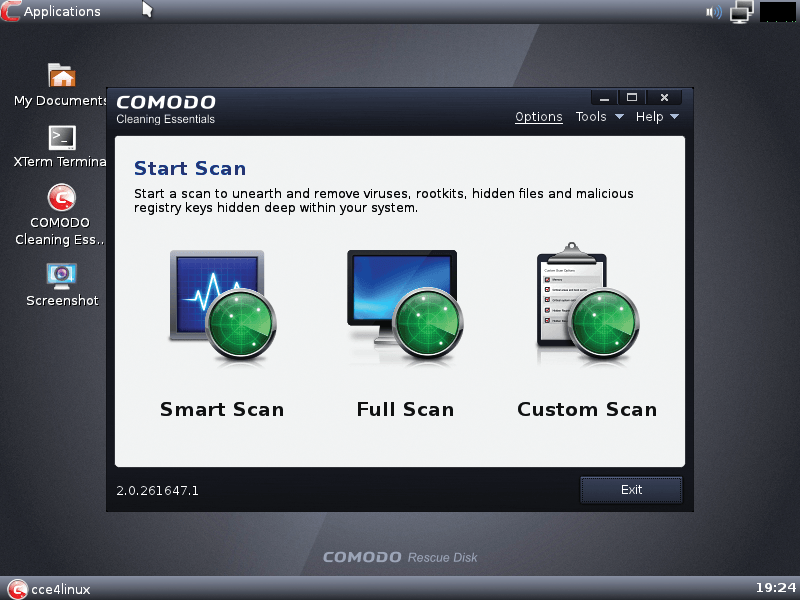
To begin, you define whether you want to perform a Smart Scan, a Full Scan, or a Custom Scan (Figure 3). For the Custom Scan, you specify in a separate dialog the directories to scan and whether CCE should also check the system's boot sector. The Full Scan and the Smart Scan have no further settings. CCE first updates the malware signature database and then starts the system scan (Figure 4). In the process, a progress bar, updated almost in real time, provides information about the problematic files found.

Before selecting a scan option, you should click the Options link at the top of the program window. Specify whether CCE should also check the disk's master boot record (MBR) for modifications and whether it should include file archives in the scan. Also, you can specify the maximum size of the content to be scanned; by default, the scan leaves out files larger than 40MB.
The Tools link, also at top right, lets you view the files removed to a quarantine directory after the scan has been completed and evaluate the logfiles generated by default for each run. You can save the plain text logfiles to an external data medium for later documentation.
Additional Tools
The Comodo Rescue Disk also has a small program menu in the upper panel where you will find the SliTaz Netbox Manager for configuring the LAN and WiFi interfaces, the lean Midori web browser, the PCManFM file manager, a small screenshot tool, and the Xterm terminal. Installing other applications on the system is not possible.
Text Mode
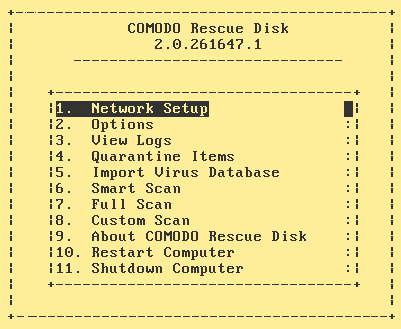
As a special feature, the Comodo Rescue Disk also features a text mode, which you enable in the GRUB boot menu from the Enter Text Mode option. In this mode, CCE starts as a text-only application that integrates some additional options that run separately in graphical mode (Figure 5), including, for example, a tool for configuring the network. Operation is entirely from the keyboard, and output is partly by means of semi-graphical elements, such as a progress bar when scanning the mass storage devices.
ESET SysRescue Live
For almost 30 years, Slovakia's ESET [5], based in Bratislava, has been developing various security solutions for Microsoft operating systems that can also be used with very old Windows installations. The free ESET SysRescue Live [6] distribution is available from the provider as an ISO image for optical media and as an IMG image for USB removable media. The USB IMG, at around 740MB, will also fit on smaller storage media.
Tools
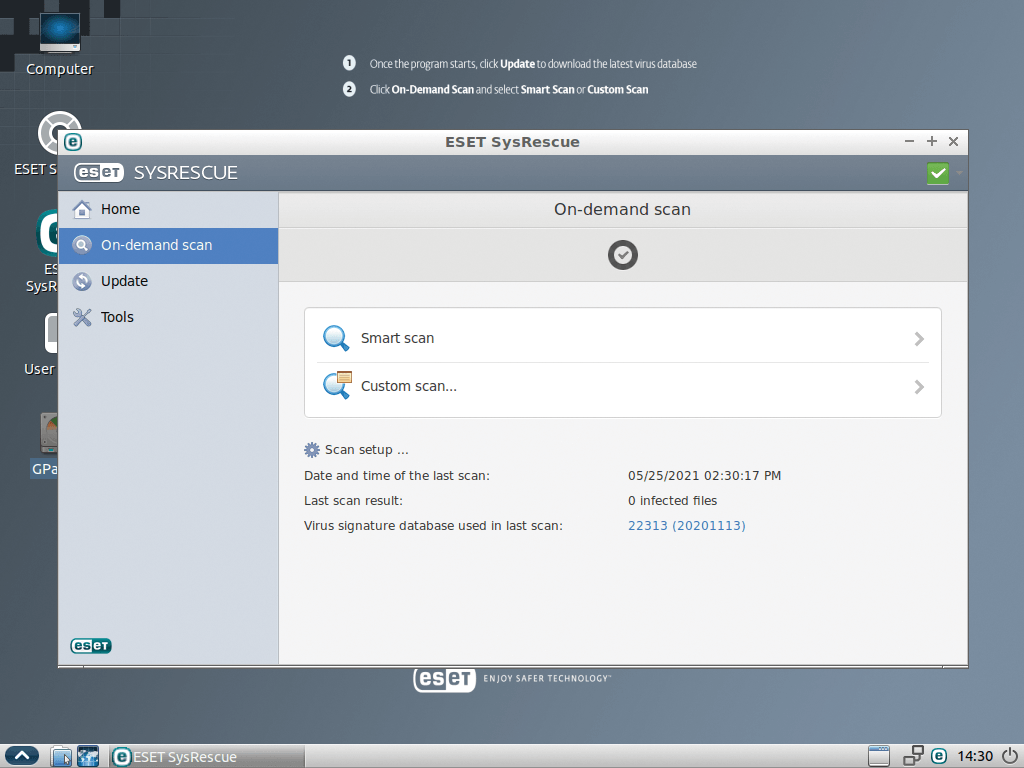
The central tool for repairing a compromised Windows system is the ESET SysRescue tool, which launches automatically after booting the Ubuntu-based Linux derivative. After confirming the license, the main SysRescue tool window opens (Figure 6). Start by updating the signatures for the virus databases by clicking Update in the left vertical bar.
Next, press On-demand scan to start scanning the Windows system (Figure 7). A settings dialog opens on the right of the window and you can decide whether you want to run a Smart Scan or a Custom Scan of the system. If you select the user-defined variant, you can then modify numerous settings in another window to influence the scope of the check.
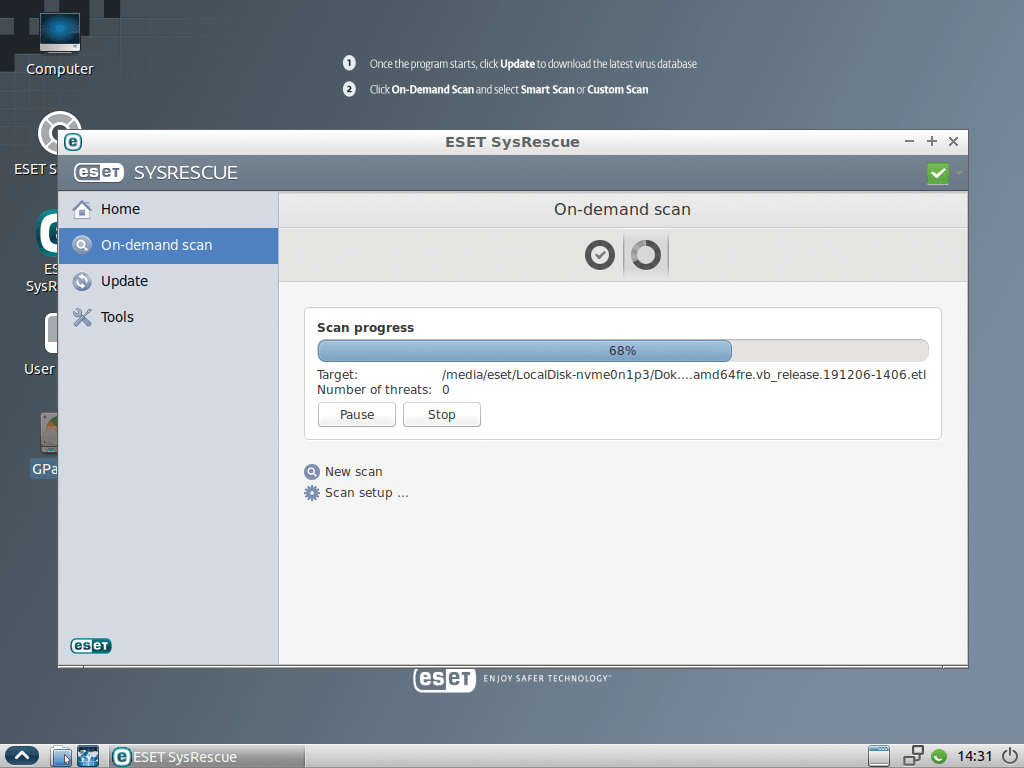
During the subsequent scan, the software continuously states the number of scanned objects and displays a progress bar. The scan window also tells you how many threats have been detected. The routine distinguishes between infected and cleaned objects after the scan is complete.
ThreatSense
ESET SysRescue Live uses what is referred to as ThreatSense parameterization to detect infected files and objects. You can set the parameters in several groups in the ThreatSense parameters section of the Advanced setup dialog.
The ThreatSense checking module bundles various threat detection methods. You define both the objects the tool includes in each scan and whether you want to detect potentially insecure or undesirable applications. You can then specify how the routine should deal with this content. Optionally, the software offers to repair infected objects (i.e., rid them of dangerous code or remove them from the system). You can use a slider to specify the sensitivity of the program.
In another dialog, you can specify the maximum size of individual objects. In the same dialog, you can also specify the nesting depth up to which the check scan archives, with 10 levels as the default. Once you have completed the settings, you can initiate another run by pressing the New scan link.
Additional Options
In the main window of the application, you are taken to additional options after selecting Tools on the left. The Log files option lets you view the logfiles created during the test run and filter them by various categories (e.g., information, errors, and warnings). The Quarantine option lets you restore objects from or move objects into quarantine. For this purpose, the software displays a corresponding file selection dialog. In Security report, you can trace the different threat scenarios on your computer system in a chart. The Submit sample for analysis option gives you the option of submitting a suspicious file to ESET for evaluation.
On Linux
The check routine in the ThreatSense module can also check Linux systems for various threats. Because the corresponding dialogs explicitly allow scanning email files for malware, the application is suitable for use on Linux-based mail servers. However, the malware hidden in mail files does not typically unleash its effect on the mail server itself, but on the mail clients running on Windows.
The GParted graphical partitioning tool is also available for use with Linux clients and can be used to fix mass storage problems. It supports a variety of filesystems and is thus also suitable for use in multiplatform environments. For efficient work with files and directories, the rescue distribution also has Midnight Commander and its graphical counterpart PCManFM on board.
Kaspersky Rescue Disk
The Rescue Disk [7] released by the Russian security specialist Kaspersky Lab [8] is available for download free of charge from the company's website. The hybrid ISO image with a size of around 610MB is based on Gentoo Linux. After downloading and transferring it to a bootable medium, the operating system first opens the GRUB graphical boot manager, where you can choose between the English and Russian localizations. After that, you will find various boot options in another dialog. Because of its lean design, the system boots very quickly to a visually unobtrusive Xfce 4.12.2 desktop.
The Kaspersky Rescue Disk feature set primarily focuses on repairing Windows systems, but it is much more broadly positioned than many other solutions: Linux systems can also be checked with the built-in Rescue Tool, and additional software such as Midnight Commander, htop, and a hardware detection tool support flexible use of the suite.
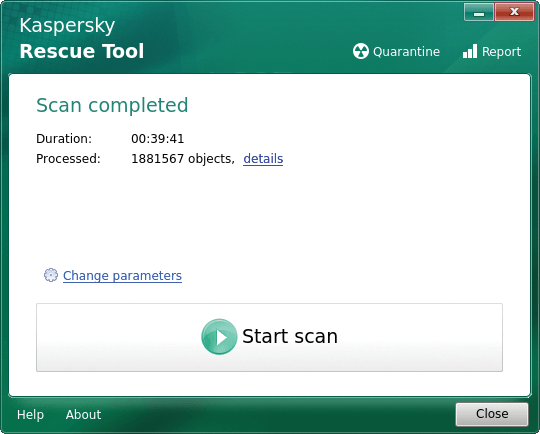
After booting, the Rescue Tool automatically comes up to perform a system scan. If you don't have a network connection, the system first pauses the initialization routine to give you the opportunity to configure WiFi access. Once the network connection is established, the software displays the dialog for scanning the system after initializing the scan engine. If necessary, you can include boot sectors and the EFI system partition in the scan. The Rescue Tool quarantines any malware it finds to render it harmless. For documentation purposes, you can also generate a report of the scan after it is complete (Figure 8).
On Windows
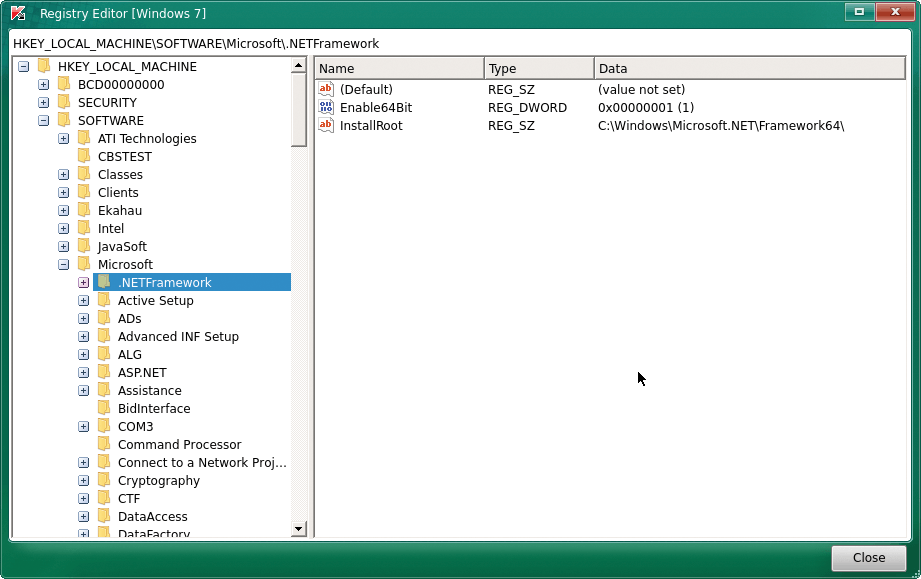
For Windows systems, the scan runs as for Linux systems, but the Rescue Tool only performs a quick scan by default. To scan the Windows system completely, you need to check the boxes for the drives in the dialog that comes up after choosing the Change parameters link. In the scan window, you will notice the Tools link that is not present when scanning Linux systems. Clicking on it opens a dialog window that offers a Registry Editor, a Windows Unlocker, and the USB Recover icons (Figure 9).
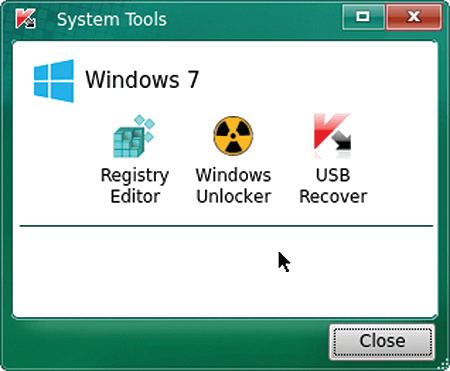
Whereas the Unlocker combats ransomware, the USB Recover tool restores the function of USB devices that were accidentally removed from Windows by mistake. For this purpose, it is also necessary to edit corresponding keys in the Windows registry (Figure 10).
Norton Bootable Recovery Tool
The Norton Bootable Recovery Tool (NBRT [9]) offered by US vendor Symantec is also a Linux-based Live system, which the manufacturer offers for download as a hybrid ISO image. At 850MB or so, the recovery distribution looks reasonably up to date after the first boot (Figure 11), but a look under the hood reveals plenty of antiquated components: NBRT is based on Red Hat Enterprise Linux 6, which was released at the end of 2010, although still supported. The 32-bit system therefore still uses kernel 2.6.32.
When booting, NBRT enables a wizard as the central element of the rescue system; the Start menu has been banished from the panel. The only other utilities available are the Opera web browser and a terminal, which can be launched directly from the panel. Opera is also anything but new: The 12.16 version integrated into NBRT was released on July 4, 2013.
Toolbox
The wizard, which launches automatically after booting the system from a removable disk, can only be used to repair Windows systems. After selecting the language (if needed) and confirming the license, NBRT updates all the malware definition files. This process can take a long time and is accompanied by the message Updating definitions.
If the software finds an installed Windows system, it automatically starts a scan of the entire mass storage, otherwise it aborts with an error message. NBRT cannot be used for safeguarding Linux systems. The tool lists problematic files found during the scan in a table, indicating a threat level in addition to the file name. You can then define in the Action column what to do with the respective file.
NBRT automatically enables a delete function for dangerous files; you might have to disable this function explicitly by unchecking the box to the left of the respective entry. If you do not make any changes to the entries in the table, the listed files are either deleted or repaired after clicking Fix top right in the window after a further prompt. This process may make a blocked Windows system workable again.
Data Backup
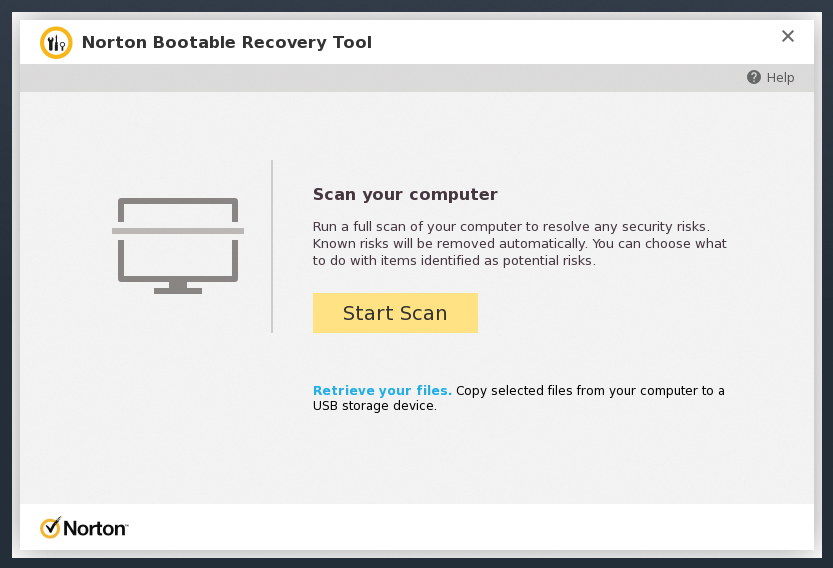
After updating the signature data, NBRT can save important files from the corrupted Windows installation, even before starting the system scan. For this purpose, NBRT has a special save dialog that you enable with Retrieve Files. A file manager opens with the system partitions from the mass storage (Figure 12), in which you select the desired files for backup by checking the boxes, before backing them up to a removable USB drive.
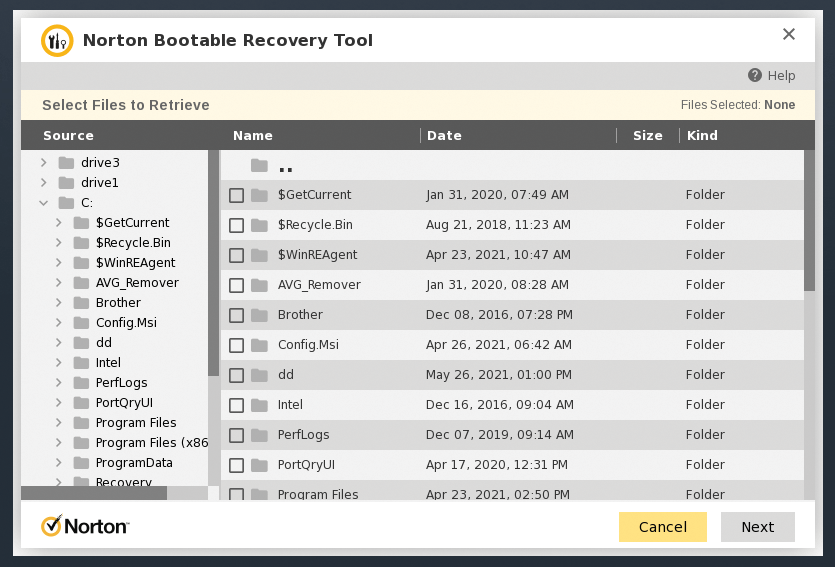
If your machine does not have a USB storage device attached to the system, the application points out this shortcoming with a corresponding error message and lets you connect a device to the Windows computer before backing up the files. If possible, you should not save any Windows system files, only personal files, to the removable medium because it is not possible to rule out the possibility of malware infecting system files.
REVE Rescue Disk
In 2014, REVE Group first launched REVE Antivirus [10]. The Singapore-based company is one of the few to offer an antivirus solution specifically for Linux. The software, which is also intended for desktop systems, is available in variants for 32- and 64-bit systems.
The vendor also provides the REVE Rescue Disk [11], which can be downloaded free of charge after registration. The approximately 240MB ISO is based on the lean Puppy Linux 5.2.8 and offers a graphical user interface as well as numerous graphical tools.
After starting the system, an illustrated quick start guide opens first. The Puppy configuration dialog then lets you localize the operating system and adjust the screen resolution. After restarting the X server, a fully-fledged Puppy Linux with a customized background comes up (Figure 13).

Concept
Unlike other manufacturers' rescue systems, REVE Rescue Disk does not focus on a proprietary tool for restoring a Windows system crippled by malware; instead, it puts data backup in the foreground. Puppy is excellent for this, because it allows the individual partitions to be mounted and opened at the push of a button by displaying the existing drives on the desktop. Folders and files can then be transferred by drag and drop between the active file manager instances (Figure 14).
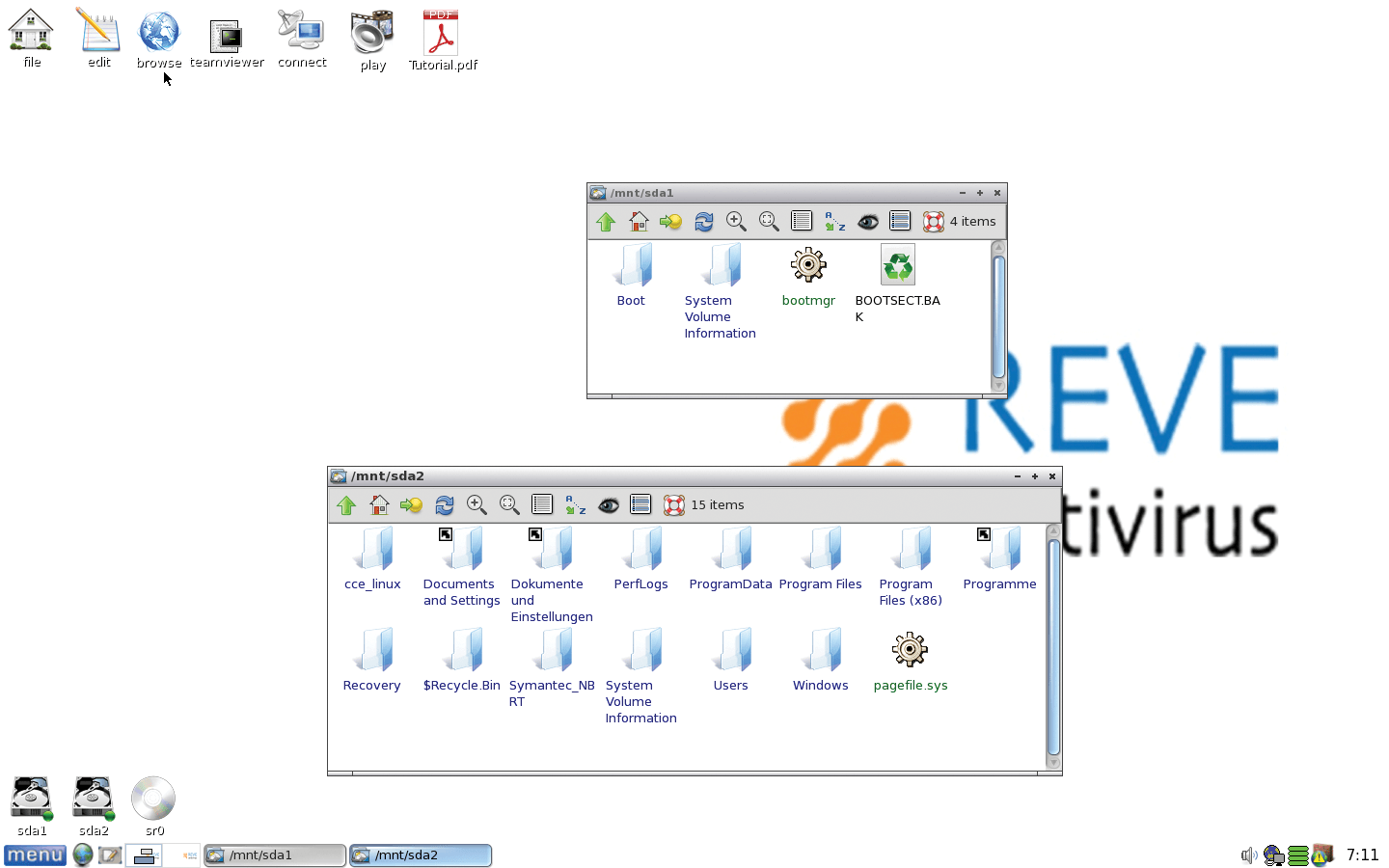
The REVE Rescue Disk stands out as a practically complete Puppy Linux system that includes all preinstalled system tools. You can install any software you like with the Puppy Package Manager, and you can even install on a mass storage device (although this doesn't normally make much sense). The REVE Rescue Disk is therefore also excellently suited for working with damaged Linux systems. To repair compromised Windows systems, on the other hand, you have to use the rescue disk to transfer the affected partitions to a removable drive and process them on another system with a commercial scanner solution from the REVE Group.
Only a few applications are pre-installed on the disk, including the remote maintenance solution TeamViewer, although in a fairly antiquated version 7 and with a complete Wine runtime environment. Besides this, Google's Chrome – again this is an outdated version 21.0 – and the lean Dillo web browsers are available. When you launch a web browser from the panel bar at the bottom of the screen, a selection dialog opens where you choose the one you want to use.
Because the REVE package completely takes over the hardware detection and system maintenance tools usually included in Puppy Linux, including the backup routines, it is also suitable for locating hardware problems. However, it remains incomprehensible why the developers have also left numerous multimedia applications and games in the distribution – this does not sit well with the idea of a cross-platform rescue system.
Conclusions
The various rescue systems impressively prove that Linux is brilliantly suited for rescuing and recovering third-party operating systems (Table 1). Most of the distributions discussed here use proprietary vendor tools to remove malware from a compromised Windows system.
Tabelle 1: Live Rescue Systems
|
Avira Rescue System |
Comodo Rescue Disk |
ESET SysRescue Live |
Kaspersky Rescue Disk |
Norton Bootable Recovery Tool |
REVE Rescue Disk |
|
|---|---|---|---|---|---|---|
|
System Linux |
Ubuntu |
SliTaz |
Ubuntu |
Gentoo |
RHEL 6 |
Puppy Linux |
|
Windows Rescue |
||||||
|
Own repair tool |
Yes |
Yes |
Yes |
Yes |
No |
– |
|
Registry editor |
Yes |
No |
Yes |
No |
No |
– |
|
Unlocker |
No |
No |
Yes |
No |
No |
– |
|
USB recovery |
No |
No |
Yes |
No |
No |
– |
|
Features |
||||||
|
Text mode |
No |
Yes |
No |
No |
No |
– |
|
Installation possible |
No |
No |
No |
No |
Yes |
Yes |
|
Linux Tools |
||||||
|
Terminal |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
Web browser |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
Graphical partitioning |
Yes |
No |
Yes |
No |
No |
Yes |
The tools that step slightly out of line are REVE Rescue Disk, which can genuinely back up data and even fix hardware problems on all operating systems with a slightly modified Puppy Linux, and Avira Rescue System and Norton Bootable Recovery Tool, whose repair tools only work with Windows systems.
ESET SysRescue Live scans email files for malware and is thus useful for scanning Linux mail servers. As a unique feature, the Comodo Rescue Disk offers a text mode in which the most important functions can be used without a graphical desktop.
For administrators of heterogeneous environments, this selection leaves virtually nothing to desire: Simply choose the rescue distribution that is the best fit for your requirements.
