
Protect Hyper-V with on-board resources
Counterintelligence
Hosts, and their operating systems in particular, play a central role in secure operations with Hyper-V. The individual virtual machines (VMs) and the operating systems on the VMs naturally need to be secured. The third security-relevant area is the configuration files for the individual VMs and Hyper-V itself – and don't forget the system services. If available, it makes sense to use a trusted platform module (TPM) chip on Hyper-V hosts to take advantage of technologies such as BitLocker and shielded VMs. As an administrator, you're adding security in a number of places, and much of it with the help of Microsoft recommendations and templates.
Securing the Host and Operating System
Minimizing the attack surface is an important security foundation, and it starts with installation. In general, it is recommended that you use the Core installation of Windows Server 2019 or newer for Hyper-V hosts, which will help you prevent attacks on the desktop and the programs installed on it. Bear in mind that a graphical user interface (GUI) can be installed retroactively on Core servers.
If you do install the GUI, you should remove programs and services that are not required. For example, Windows Media Player is active by default on Windows Server 2019, but definitely not needed on production servers. To uninstall Media Player, enter:
dism /online /Disable-Feature /FeatureName:WindowsMediaPlayer /norestart
Only absolutely essential services should be installed and started on the Hyper-V host. Any additional software just adds attack vectors. In general, it is almost always better to install additional software on another server rather than on a Hyper-V host on which numerous VMs are in use. Of course, this is also true when you consider performance.
Microsoft advises against deploying production VMs for server applications by way of Hyper-V on Windows 10. Especially on smaller networks, administrators are tempted to connect users to VMs by this route, but doing so poses a significant risk for security reasons. It's better to go for the free Hyper-V Server 2019. Windows 10, as a never genuinely completed operating system, is fine as a test environment for Hyper-V, but under no circumstances should you provide server-based services on networks with Windows 10.
Installing Updates and Closing the Gaps
The operating system on the Hyper-V host, the firmware, and the device drivers should always be up to date. Microsoft regularly closes critical gaps that also affect Hyper-V on its monthly patch day. In most cases, numerous VMs run on a Hyper-V host, so a security vulnerability does not just affect one server, but several. The patch status of your Hyper-V hosts therefore plays an important role.
For example, Microsoft closed a critical vulnerability in Hyper-V on patch day in October 2020. Attackers were able to execute malware on the VMs because of the vulnerability and gain access to the host. On Hyper-V servers, therefore, you will want to install at least this update [1] promptly, which is possible with Windows Server Update Services (WSUS) on the internal network or directly on the Windows update server.
Implement Safety Recommendations with Policies
As the vendor of Windows Server, Microsoft issues security recommendations that you will want to take note of as an administrator through the Microsoft Security Compliance Toolkit [2], which contains group policy templates with which you can secure Hyper-V hosts in line with Microsoft recommendations. The download comprises tools and ZIP files for various Windows versions with which you can create Group Policy Objects (GPOs) for improved security on Hyper-V hosts and VMs.
With the Policy Analyzer from the toolset, first check whether the security settings on the server make sense, so you can adjust the settings to comply with Microsoft's recommendations, if needed. For the analysis, the Policy Analyzer reads the backup files of the current GPOs along with their settings. The ZIP archives include files with the PolicyRules extension, which you can use to compare the existing settings with the recommendations from Microsoft. In this way, you can quickly identify vulnerabilities and missing settings.
Microsoft also provides an Excel table in the Documentation directory of the ZIP archive, listing all settings that can be implemented with group policy templates. Under the item Security Template, you can see which security settings are addressed by the group policies. The table shows the settings for member servers and domain controllers on the basis of Windows Server 2019. In the GP Reports directory, you will find a report as an HTML file for each policy. From this information, you can either create new policies or modify existing ones.
If you want to create group policies from the templates recommended by Microsoft, the easiest approach is first to create a new GPO in Group Policy Management and read in the templates. As long as the GPO is not yet linked to a container, the settings will not be implemented. Only when they are linked do the servers apply the settings. To integrate the policy settings into the new policy, select Import Settings from the context menu of the newly created policy. You can use a wizard to import the templates with Microsoft's recommendations (Figure 1). The files are located in the GPOs directory. View Settings lets you view the policy settings to be imported, although this report is basically what you can find in GP Reports.
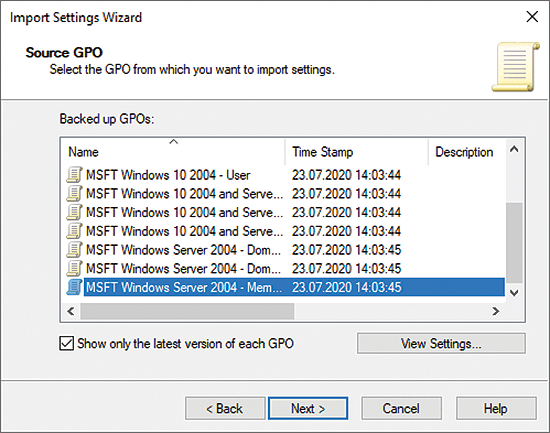
In addition to the baselines provided by Microsoft, third-party vendors also offer recommendations for secure operation of Windows on corporate networks. Well-known third-party providers are the Defense Information Systems Agency (DISA) [3] and the Center for Internet Security (CIS) [4]. In general, it is worthwhile to work through these recommendations carefully and to adapt them to your own requirements.
Separate Networks for Hyper-V
You should always operate Hyper-V hosts on separate networks. On the server, use dedicated network adapters to manage the Hyper-V host and connect the VMs. You will also want to use a hardened network to access the VM configurations and the virtual hard disk files. The same applies to live migration.
Generally, IPsec is the best choice for these networks. For communication with file shares, it is best to use SMB 3.0 with end-to-end encryption to prevent man-in-the-middle attacks. If you use different networks, you can secure individual areas more strongly and use the firewall settings to define various rules that restrict access to the respective network adapter.
Best Practices Analyzer
In Windows Server 2019, Microsoft enhanced automatic server role auditing by introducing the Best Practices Analyzer (BPA) built-in tool, which is also available in the Server Manager for checking server roles over the network. Almost all server roles can be tested and the results displayed centrally. The BPA is particularly interesting for Hyper-V, because it can be used to optimize both local and virtual servers. Virtual network switches can also be scanned with the BPA. To start a scan for Hyper-V, enter:
Invoke-BpaModel -ModelId Microsoft/Windows/Hyper-V
You can redirect the results of the scan to a specific path, but you have to create it first:
Invoke-BpaModel -ModelId Microsoft/Windows/Hyper-V -RepositoryPath C:\temp\BPA
If you want to start a scan for a server on the network, use the command:
Invoke-BpaModel -ComputerName dl20 -ModelId Microsoft/Windows/Hyper-V
The results files are stored in XML format in a path you specify, sorted into subdirectories by server role and server. The files can also be parsed in the browser or by other programs. The scan results are stored on the local server – even if you scan a Hyper-V host on the network. For example, if you want to display all scan results for Hyper-V in the PowerShell, use:
Get-BpaResult -ModelId Microsoft/Windows/Hyper-V
If you saved the results in a specific directory, the command
Get-BpaResult -ModelId Microsoft/Windows/Hyper-V -RepositoryPath C:\temp\BPA
will help. You can also export the results to an HTML file:
Get-BpaResult -ModelId Microsoft/Windows/Hyper-V | ConvertTo-Html | Out-File C:\temp\BPA\results.htm
Of course, the results are also available in the GUI. Once you have started the BPA check, you will see the results on the individual tiles in the Server Manager. You can open them by clicking on a tile. If you click on the results of the BPA check, the Server Manager displays the errors that were identified. You can also view all errors from all servers on the network.
From the context menu of a result, you can start a new check for the corresponding server, hide the result, or copy it to the clipboard (e.g., for an Internet search). The BPA results can also be found in the Local Server and All Servers views in the Best Practices Analyzer area of the Server Manager (Figure 2). When a BPA result is displayed for a server role on one of the servers, the tile color changes, which means you can immediately see where improvements for a server are possible. By excluding a result, you can disable individual messages, if required. From the view in the BPA, you can also filter the results by severity, server, and categories.
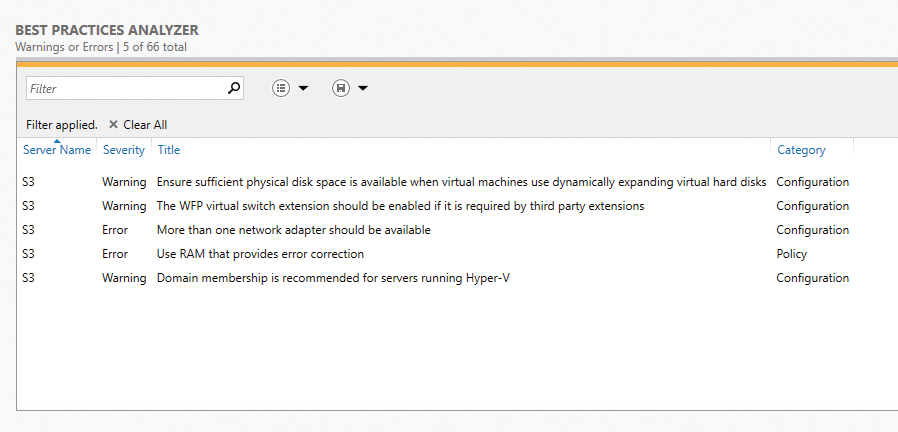
Defender Credential Guard and Shielded VMs
To further secure Hyper-V, Microsoft also recommends using advanced security technologies. On Hyper-V servers, you should consider running Windows Defender Credential Guard [5], which uses virtualization-based security to protect credentials. In this way, only defined system software can access credential data; NTLM authentication protocol password hashes, Kerberos tickets, and domain credentials are protected. The configuration is policy based.
You will also want to operate Hyper-V hosts as a guarded fabric, encrypt the VMs, and deploy them as shielded VMs, which provides significantly more security on the network, even if the configuration is more complex.
In Windows Server 2016, Microsoft introduced the Host Guardian Service (HGS) to improved the security of VMs. Virtual servers can be hardened in Hyper-V and isolated from other administrators, attackers, and unauthorized access. Locked-out administrators can still control certain VMs (i.e., shut them down or start them), but they no longer have access to the VM's data, which also applies to unauthorized users or malware. Networks that have been hijacked by attackers or on which other areas have been compromised no longer pose a threat to secured VMs.
The HGS ensures that VMs in Hyper-V are better isolated from each other. If an attacker or malware compromises a VM, this service prevents the attack and the spread to other VMs. Additionally, the service supports encryption, enabling VMs to be secured in a variety of ways. For example, the hard drives can be encrypted with BitLocker, access to the console can be restricted, and you can define the Hyper-V hosts on which a secured VM is allowed to start.
With HGS, you can protect Hyper-V servers running Windows Server 2016 and 2019 in the Datacenter edition. Older versions or Windows Server 2019 Standard edition cannot be secured with HGS. On the VMs, you again have the option of running 2012 and 2012 R2 in addition to Windows Server 2016 and 2019. Windows Server 2019 Datacenter and the free Hyper-V Server 2019 also support shielded VMs with Linux. On Windows Server 2016, these encrypted VMs can only be used with Windows Server 2016. In addition to this new feature, Microsoft has further improved the technology behind shielded VMs. Thanks to the offline mode, they now still start if the HGS cannot be contacted.
To use shielded VMs, you first need a server or cluster with the HGS. In addition to Hyper-V, you also have to install the Host Guardian Hyper-V Support server feature on the Hyper-V hosts to be protected. This extends the functions of Hyper-V to include options for operating shielded VMs.
You also need to install the Remote Server Administration Tools (RSAT) for shielded VMs when you install the Hyper-V host and connect to the Host Guardian Service. Known as Shielded VM Tools, they are not automatically installed on Hyper-V hosts but have to be set up manually.
When you create new shielded VMs, they are of the "generation 2" type. HGS uses a virtual TPM (vTPM) chip for protection. The Add-VMTPM PowerShell cmdlet is also useful for this purpose. The tools needed to connect Hyper-V to the Host Guardian Service can also be installed in PowerShell:
Install-WindowsFeature -Name HostGuardian Install-WindowsFeature -Name RSAT-Shielded-VM-Tools Install-WindowsFeature -Name FabricShieldedTools
You can handle the task of securing the Hyper-V hosts, for example, through membership in an Active Directory group if you do not rely on UEFI and TPM. Use the cmdlets:
Get-WindowsFeature HostGuardian Get-HgsClientConfiguration
to check whether a host is already connected to an HGS server.
Encryption Without Shielded VMs
If you want to encrypt your VM virtual hard drives, you do not necessarily have to rely on shielded VMs. Since Windows Server 2016, a virtual TPM can also be added to VMs from the Security menu item in the properties of the VMs. Activating the Trusted Platform Module function, makes a virtual TPM available on the VM; it can then be used for BitLocker encryption. VMs encrypted with a vTPM based on BitLocker can be integrated into a guarded fabric with shielded VMs at any time. Live migration is also possible. The important thing here is that you are working with a generation 2 VM. In addition to the Hyper-V Manager, the settings can also be made in PowerShell. For example, to activate and deactivate the technology, use:
Enable-VMTPM -VMname <name> Disable-VMTPM -VMName <name>
The TPM is displayed in the VM's device manager under Security devices. Selecting tpm.msc lets you initialize and set up the module.
Access Permissions and Authorizations
VM administrators do not need administrative access to the host operating system. For this reason, you will also want to adjust the authorizations for administrators on Hyper-V hosts. Admins who do not need to manage the host also do not need administrative access to the host operating system. Usually, it is sufficient for Hyper-V administrators to be members of the Hyper-V Administrators group on the server. Hyper-V hosts should also have antivirus protection installed. However, exclusions in malware scans are useful. When using Microsoft Defender, this is automatically the case. Many other scanners also support Hyper-V. To disable the exclusions, enter the command:
Set-MpPreference -DisableAutoExclusions $true
In general, however, you will want to make sure that the essential components of Hyper-V are monitored, but not unnecessary areas or services and directories that can cause performance problems. Windows Defender does not scan the following file types: VHD, VHDX, AVHD, AVHDX, VSV, ISO, RCT, VMCX, and VMRS. You can additionally exclude the following directories from scanning:
%ProgramData%\Microsoft\Windows\Hyper-V%ProgramFiles%\Hyper-V%SystemDrive%\ProgramData\Microsoft\Windows\Hyper-V\Snapshots%Public%\Documents\Hyper-V\Virtual Hard Disks
The following processes are particularly important:
%systemroot%\System32\Vmms.exe%systemroot%\System32\Vmwp.exe
For more information on exclusions, see recommended antivirus exclusions for Hyper-V hosts online [6].
Third-Party VHDs and Nested Virtualization
It should go without saying that you should never mount third-party virtual hard disks (VHDs) on Hyper-V hosts because of the risk of attacks at the filesystem level. You should also avoid deploying VMs with unknown VHDs. Perform extensive tests, preferably on test servers, before you implement third-party VHDs for a VM on a host to check for malware or suspicious activity.
Additionally, Microsoft generally recommends not using nested virtualization on Hyper-V hosts. Otherwise, administrators of VMs with activated virtualization could create VMs themselves, which in turn represent a danger for, and generate load on, the Hyper-V host. Nested virtualization should only be implemented for scenarios that you absolutely need – ideally in highly monitored environments.
For even greater security, Microsoft recommends generation 2 VMs for supported operating systems whenever possible. You will also want to enable Secure Boot on the VMs (Figure 3) to prevent unauthorized code from starting with the operating system without first being checked by a virus scanner. The feature is also available for Linux servers if the distribution supports generation 2 VMs in Hyper-V. The settings can be found in the properties of a VM under Security. You can enable secure start for generation 2 VMs here, select the template, and, if prompted to do so, enable TPM on the VM and shielding.
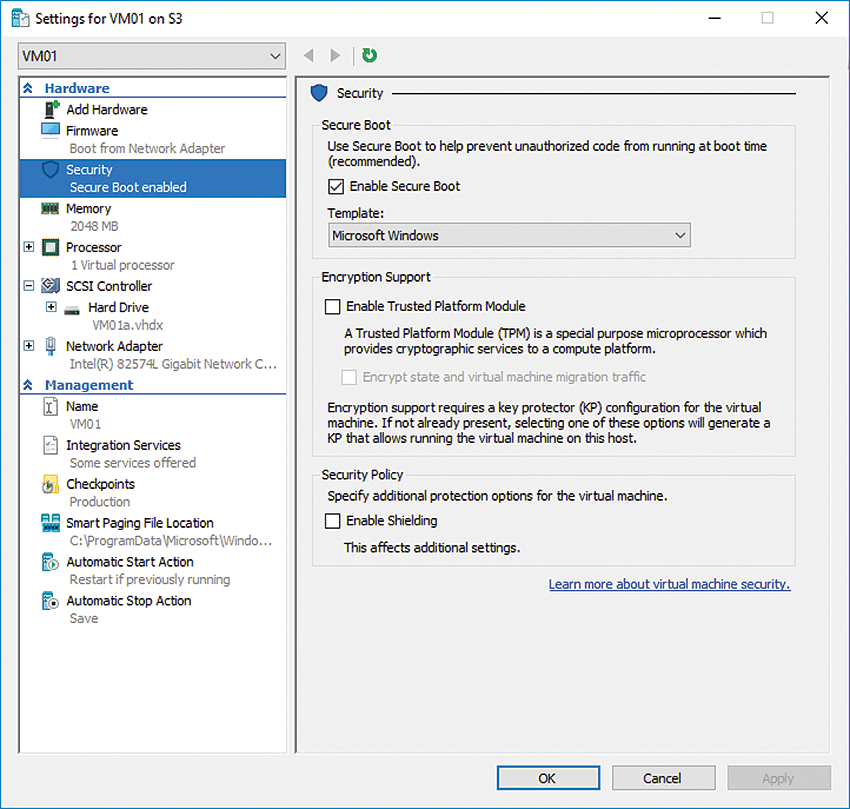
Microsoft explains the options for secure generation 2 VMs on GitHub [7]. As with the Hyper-V host, you should always keep the VMs as up to date as possible, especially for security updates. Install the integration services for the supported guest operating systems; Windows Update handles these updates.
High Availability with Windows Server 2019
Last but not least, service availability is also a security consideration. With Hyper-V Replica, virtual hard disks and entire servers can be replicated and synchronized asynchronously between different Hyper-V hosts on a network with Windows Server 2019. Replication is by way of the filesystem; a cluster is not necessary.
Replication can be performed manually, automatically, or on a schedule, and you can set it up in a Hyper-V Manager wizard. Live migration of virtual servers without clusters is also possible. For Hyper-V hosts to support replication, you first need to enable it. Replication to the free Hyper-V Server 2019 is also possible and can be managed in a wizard, which you start from the context menu of virtual servers in Hyper-V Manager.
Conclusions
Improving the security of Hyper-V hosts and VMs can be accomplished in a number of ways. Before you rely on commercial add-on tools and advanced security measures, why not first leverage the benefits of Windows Server's internal capabilities? Microsoft provides guidance to help you operate Hyper-V hosts in a fundamentally more secure manner. You can also use the Best Practices Analyzer to check whether Hyper-V has problems that can be fixed in just a few steps.
