
Reducing the Windows 10 attack surface
Digging In
Microsoft has been providing tools to administrators to prevent attacks against Windows systems for several years now. The Attack Surface Analyzer introduced in Windows Vista was replaced by Attack Surface Reduction in Windows 10. In this article, we highlight the available protection mechanisms and show you how to use them effectively.
An attacker's goal is to exploit application and computer vulnerabilities (especially their operating systems) alike. In the process, not only servers and workstations attract the attention of attackers, but network devices such as routers, switches, and access points have become targets, especially in recent years. Security researchers are increasingly detecting malware on peripheral devices [1]. If you issue smartphones to your employees with access to the internal network, these devices are also potential gateways for attackers.
Several hundred different attack vectors are known in the literature. Of these, some are well researched and well known to both attackers and system owners, which makes it easy to provide protection against exploits. Brute force attacks on SSH servers, the lack of encryption in communications, and distributed denial of service (DDoS), for example, can be well managed by tools such as Fail2Ban, a public key infrastructure, and load balancing service providers such as Cloudflare. Although CEO fraud has been very successful in recent years, it can often be averted through awareness campaigns. Zero-day exploits targeting unpublished vulnerabilities in hardware or software have virtually no effective countermeasures.
Ransomware, Phishing, and Insiders
Three different attack vectors have been the subject of recent public discussion. Blackmail trojans, or ransomware, often enter organizational networks through forged email or manipulated email attachments. If the recipient opens the supposedly harmless office file in the attachment and enables the macros it contains, the malware can embed itself in the system. Once in place, the malicious programs first wait and analyze access patterns, working hours, shares on the local network, or existing backup systems. Once they have collected enough information, the race against time begins.
The malware encrypts as much data as possible without attracting attention, preferably also the backups if they are not access protected. By the time the data owner notices the damage, it is often already too late. Important files are encrypted and a message is sent with an option to receive the code to unlock and decrypt the data by paying a ransom. Often, the programs even offer to decrypt individual files on a test basis. This function is specifically offered by the criminals to strengthen the users' trust in the functionality. The victims are then often much more willing to pay the demanded ransom.
Stolen identity data is another attack vector that has caused more and more damage in recent years. Account hijacking is a problem that should not be underestimated, especially in the area of online stores. In particular, criminals take advantage of the fact that many users use the same passwords to access different services. However, the identity data are not always captured from the service providers themselves. Although many large online services have had to admit to illegal access to customer data because of a vulnerability in their systems, criminals are unfortunately still very successfully sending very realistic looking phishing email to users. In this way, they can usually rely on obtaining valid access credentials for online accounts directly from the hands of the users themselves.
Often enough, insiders are part of successful attack vectors. Although many companies restrict remote access through firewalls, VPN, and special access rights to the local network, the same is not true for physical access to resources on site. Therefore technicians, cleaning staff, or other employees with extensive access to offices and printer and server rooms can also access systems directly. Unlocked user sessions, the ability to boot systems with USB devices, or installed hardware keyloggers that tap user passwords pose a major risk to the integrity of workstations, servers, and printers.
Reducing the Attack Surface
Simple methods can help you reduce the attack surface of a system. The example in this article is a database system. In the standard use case, the database system opens a network socket and listens for incoming connections on all IP addresses used by the operating system – including connections from the Internet, of course. However, if you only use local database access, you will want to select the network interface for the server process or configure the local IP address to rule out access from the Internet.
Incidentally, a firewall installed at the perimeter has a similar effect, at least as far as access from the Internet is concerned. However, if an attacker is already on your network, this firewall can no longer protect your company, but you can restrict local attackers. Many distributions offer passwordless access to the database administrator account for locally logged-in users. You need to restrict this account, too. With just a simple few steps, you have now reduced your database server's attack surface.
Protection with Windows Defender
Introduced in Windows 10 version 1709, Microsoft Windows Defender Exploit Guard comprises four components: attack surface reduction (ASR), network protection, controlled folder access, and exploit protection. (The abbreviation ASR is used in other ways by Microsoft; for example, it can also mean Azure Site Recovery.) ASR uses various measures to provide protection against malware looking to attack your system through installed Office programs, scripts, or email. Network protection protects your system by expanding the scope of Defender SmartScreen, adding further rules that prevent outgoing HTTP traffic to destinations whose domain names or hostnames are untrustworthy.
Controlled folder access protects your data in certain folders from access by less trusted programs on your system. You can configure this feature in the Windows Defender Security Center. When a program from an untrusted source accesses one of your protected folders, the user sees an Access Denied message from Windows Defender. Exploit protection is the logical successor to the Enhanced Mitigation Experience Toolkit (EMET) and offers additional features such as Code Integrity Guard, blocking Win32k system calls, or the ability to check the integrity of the heap memory area. You can try out all the security features of Windows Defender Exploit Guard after enabling it on Microsoft's specially set up demo website [2].
Setting Up ASR
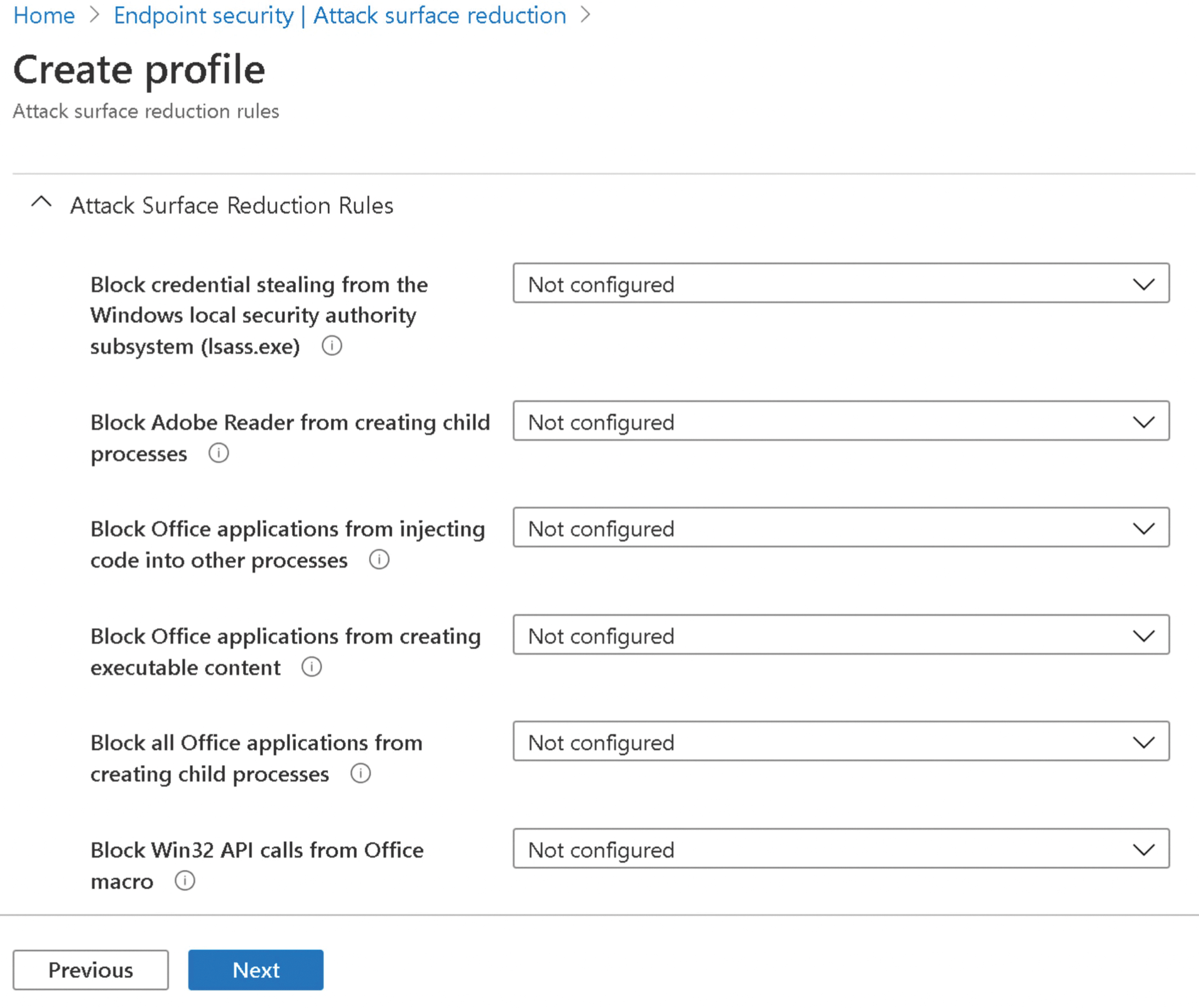
The full scope of ASR is only available with a license for Windows 10 Enterprise. However, some of the ASR rules can also be used in other versions. You have different options for enabling and configuring rules on your systems: Microsoft Intune, Mobile Device Management (MDM), Microsoft Endpoint Configuration Manager, Group Policy, and PowerShell. Depending on which tool you typically use to configure your machines, the convenience of activating the rules varies.
Figure 1 shows ASR rules in the Endpoint Configuration Manager. You will find more information about the effects of the different rules there. Even if it seems to make sense at first glance to activate all rules, you will want to define different rulesets depending on the activity of your employees on the affected system. You can choose different actions for each rule. To check the effects of different rules, select audit mode. You can then first check the effects of the individual rules in the event log.
PowerShell for Quick Tests
If you want to try out ASR rules on individual systems without the available device management tools, PowerShell is a quick alternative for testing. Unlike the graphical interfaces, you need the GUID assigned to each rule when selecting rules in PowerShell. You will already be familiar with the PowerShell Get-, Set-, and Add-MpPreference cmdlets from Windows Defender, which you can use to define, for example, exceptions in monitoring for individual folders or processes.
With the introduction of attack surface reduction, you can also use it to change the actions for ASR rules. The AttackSurfaceReductionRules_Ids parameter lets you specify one or more of the GUIDs for which you want to change the status, and you pass in the new status with the AttackSurfaceReductionRules_Actions parameter. Given three different rules, you could then configure the actions as follows if you want to disable the first rule, enable the second rule, and disable checking for the third rule:
Set-MpPreference -AttackSurfaceReductionRules_Ids <GUID1>, <GUID2>, <GUID3> -AttackSurfaceReductionRules_Actions Disabled, Enabled, AuditMode
Keep in mind that you need to specify the action for each rule separated by a comma, even if you want to apply the same action for all rules.
Defining Exceptions
If you want to disable protection with ASR rules for individual objects, you can specify them with the AttackSurfaceReductionOnlyExclusions parameter. As the argument, specify the absolute path to a directory or a program. Note the difference between the calls to Set-MpPreference and Add-MpPreference. The first call completely deletes the existing list of exceptions and creates a new exception list with the values you pass in. However, if you want to add individual objects as exceptions to an existing list, choose the second cmdlet.
15 ASR Rules
In total, Microsoft defines 15 ASR rules for the execution of content from received email or from Office and script files. The following sections look at the GUID and the effect of applying each rule.
The rule with GUID BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550 prevents the execution of programs and scripts, JavaScript, and Visual Basic or PowerShell if they are saved from Outlook or Outlook.com. Microsoft promises that email attachments from other webmail providers are also protected but supply no overview of supported providers in the documentation. Outlook itself can be restricted significantly by applying rule 26190899-1602-49E8-8B27-EB1D0A1CE869 when creating child processes.
Different rules protect your system from misbehavior from within Office applications. Enabling the GUID D4F940AB-401B-4EFC-AADC-AD5F3C50688A lets you prevent Office applications from starting additional child processes. This rule contains macros that retroactively load and run files from the Internet and sometimes restricts the ability of legitimate programs and macros that you use as an extension of your Office package to work correctly. However, as described before, exceptions can be defined for this purpose; you should use them carefully, of course.
Keeping Malware Out
To prevent malware from being stored on your system's hard drive from within Office (e.g., for manual execution by one of your employees later on), you need to enable the rule with GUID 3B576869-A4EC-4529-8536-B80A7769E899. Doing so automatically prevents a very common method of permanently embedding malware on a system. You can block calls to the Win32 API from within Office applications with rule 92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B, which prevents the direct execution of malware, without it having been written to the hard drive first.
You can prevent access to working memory areas used by third-party processes and thus the ability of malware to infiltrate other active processes from within Microsoft Office by activating GUID rule 75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84. For the most part, you can use this rule safely. Virtually no legitimate enterprise software implements this kind of functionality.
To prevent scripts that are used to download and then install malware on a system, activate two rules: GUID D3E037E1-3EB8-44C8-A917-57927947596D blocks JavaScript such that no content downloaded from the Internet or another internal system can be executed, and GUID 5BEB7EFE-FD9A-4556-801D-275E5FFC04CC prevents scripts from executing if source code obfuscation methods are detected in them.
Blocking Unknown Software
To prevent the execution of unknown or previously unused software on your systems, use GUID rule 01443614-CD74-433A-B99E-2ECDC07BFC25. However, this is only enabled if you also enable Microsoft Defender cloud delivery protection at the same time with:
Set-MpPreference -MAPSReporting Advanced Set-MpPreference -SubmitSamplesConsent SendAllSamples
You also need cloud delivery protection enabled for the next rule, GUID C1DB55AB-C21A-4637-BB3F-A12568109D35, which prevents executable files that Microsoft classifies as potential ransomware from entering your system. When it comes to execution prevention rules, you must always keep in mind that the list of exceptions, which you may have already expanded in one of the previous rules, will apply to all rules when they are checked.
The use of analysis tools such as Mimikatz [3] to grab valid login or session data through the Local Security Authority Subsystem Service (LSASS) are restricted with the rule 9E6C4E1F-7D60-472F-BA1A-A39EF669E4B2. Microsoft mentions in the documentation for this rule that it can generate many false positives under certain circumstances, because the legitimate use of the LSASS interface (e.g., when creating a child process) is also restricted when you apply the rule.
Restricting Software Execution
As an administrator, you know the benefits of remote execution with tools like PsExec or Windows Management Instrumentation (WMI). Because these techniques are also used regularly by malware authors, you can restrict remote execution with the ASR rule D1E49AAC-8F56-4280-B9BA-993A6D77406C. The same applies to the execution of programs launched from external storage media such as a USB stick. The rule with GUID B2B3F03D-6A65-4F7B-A9C7-1C7EF74A9BA4 restricts the execution rights of programs or scripts stored on external devices.
To prevent the permanent installation of malware with WMI event notifications – or appropriately configured trigger functions for specific events – use rule E6DB77E5-3DF2-4CF1-B95A-636979351E5B. However, this rule is currently only available if you use Group Policy or PowerShell, because the graphical tools do not yet have a name, and thus no access, to the configuration of this rule. Officially, it is therefore listed as unsupported in the Microsoft documentation.
As the only non-Microsoft program, you can also restrict the functionality of Adobe Reader with rule 7674BA52-37EB-4A4F-A9A1-F0F9A1619A2C. Particularly in the case of targeted social engineering attacks by email, but also in the case of classic spam, the malware is often hidden in PDF files that can find their way to users in compressed archives and thus get past the central firewall. Therefore, it may well make sense for you to restrict the ability to launch child processes for Adobe Reader.
If entering the GUIDs for calling the cmdlet is too complicated, you will find useful open source tools on GitLab that can help you select and enable rules [4]. You can download and execute the executable file or the PowerShell script from the repository if you have not already prevented the execution of downloaded content with ASR.
Practice Without Risk
To check the effectiveness of the available ASR rules, you should visit the web page with examples [2] provided by Microsoft, as mentioned earlier. As a registered user, for each ASR rule, you can pick up test files that you should not be able to open or start on your system with the ASR ruleset in place. In this way, you will also get to know the entries in the Event Viewer and the warnings output by Microsoft Defender.
For use on production systems, you should first configure all rules in audit mode. You can then quickly determine which of your employees' activities conflict with the selected ASR rules, customize the rulesets for distribution with your device management, and distribute the rulesets to the systems that need them.
Conclusions
Over the past few years, Microsoft has repeatedly developed new malware protection approaches. Not all of them have been successful at the end of the day. Basically, you will also want to keep an eye on the attack surface of the entire corporate network beyond your Windows systems. The attack surface reduction of Windows Defender Exploit Guard investigated here covers only a small area of potential points of attack, although they are very common methods used by attackers. Additionally, ASR offers an easy way to get started and, when deployed, can take meaningful steps to protect your entire IT infrastructure.
