
Securing and managing Microsoft IIS
The Right Tools
In this article, I look into the options Microsoft provides for effective management of Internet Information Services (IIS). You can easily manage web servers on Windows Server 2019 with multiple tools in parallel (e.g., the IISAdministration module in PowerShell). The command line on Windows servers also offers a way to manage the web server with the appcmd and iisreset tools, not only for servers with graphical user interfaces, but also for core servers and containers. In this article, I assume you have IIS configured on Windows Server 2019 (Figure 1), but most settings also apply to Windows Server 2012 R2 and 2016.
Managing the Web Server and Sites
Once IIS is up and running, it can be managed with the IIS Manager. The fastest way to launch this tool is to enter inetmgr.exe. If you do need to restart the IIS system service, you can use
net stop w3svc net start w3svc
or you can work with Stop-Service, Start-Service, or Restart-Service in PowerShell. In Windows Admin Center, you can use the Services area. The system services themselves can be accessed by typing services.msc.
To restart the web server, run either of the following commands at the command line:
iisreset iisreset /noforce
In addition to starting and stopping the entire server, you can also temporarily disable individual websites. All other websites on the server are unaffected; open the IIS Manager and click on the website you want to restart or stop. In the Actions area of the console, the Manage Website section displays the commands for restarting and stopping.
At the command prompt, you can use the appcmd tool to restart or quit. Type the commands
appcmd stop site /site.name:contoso appcmd start site /site.name:contoso
to stop and restart the Contoso website. However, the tool is not directly in the path for the command prompt, so it cannot be called directly. First you need change directory to \Windows\System32\inetsrv. You can get detailed help by typing appcmd /?. Because help is context sensitive, you can also get appropriate support for individual commands, such as appcmd site /?.
Viewing Requests and Creating Backups
The appcmd command displays the current requests to a web server and backs up its data. Current requests can be retrieved and the settings of a server backed up by typing:
appcmd list request appcmd add backup <name>
Creating a backup is a good idea before you start making system changes. The existing backups can be viewed and restored with:
appcmd list backups appcmd restore backup <name>
However, if you back up the server before changing to a distributed configuration and restore this backup, you will have a local configuration again after the restore.
Of course, you should run this backup as a regular task on Windows and save the IIS configuration to a file:
%WinDir%\system32\inetsrv\appcmd.exe add backup "<name of backup>"
Then, you can delete existing backups with the
appcmd.exe delete backup "<name of backup>"
command.
Developer Tools in Internet Explorer and Edge
The developer tools in Internet Explorer and Edge are interesting for administrators and developers alike. To access them, press F12. The tools display the source code for a page and help with error analysis (e.g., if a page takes a long time to load). The Network tab lets you check the loading times of pages to determine which areas of a website delay loading. To analyze a page later, just save the output.
Managing IIS in Windows Admin Center
Microsoft provides an extension to Windows Admin Center for servers on which IIS is installed. This extension already has almost all of the same functions as the IIS Manager. The advantage of Windows Admin Center for central administration of IIS is that central administration is far easier than with the IIS Manager (Figure 2).
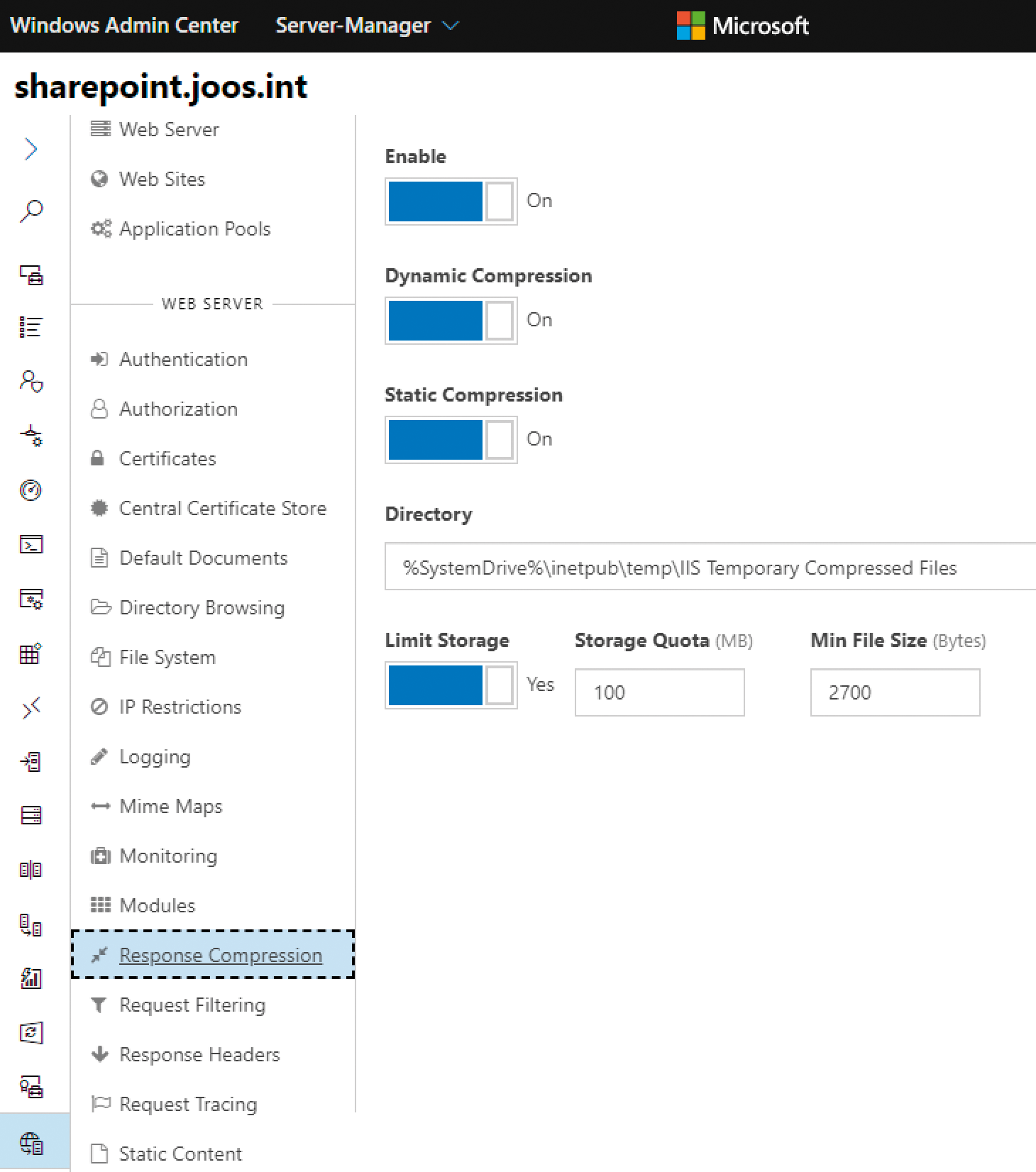
To use the extension, add it in the Windows Admin Center settings from Extensions. The Admin Center will then automatically show the appropriate options if IIS is installed on a server. The options are located in the Extensions section of the navigation sidebar from IIS. Microsoft is expected to integrate IIS management permanently into the menu structure of Windows Admin Center. Also in the Admin Center, install the extension for managing IIS over the network on the corresponding server, if necessary. Microsoft also provides the necessary extension on GitHub [1].
After the IIS extension connects to the appropriate server in Windows Admin Center, select the website whose settings you want to change. If the server settings are not displayed, your monitor's resolution is not high enough. In this case, it might be useful to hide the Windows Admin Center menubar with the arrow in the upper left corner. Afterward, Windows Admin Center displays the commands for managing IIS in a separate menu area. The settings are then accessible. The Settings, Bindings, Limits, and Application Pool tabs are used to manage the settings for the site. The Monitoring tab also provides a separate area for monitoring the performance of a web server.
Adjusting the Security Settings
You can use the tools mentioned above to configure the security settings of the web server. In most cases, IIS Manager is still used. Important settings primarily relate to the firewall on the server, for which you can use the standard firewall console (wf.msc; Figure 3) or Windows Admin Center. PowerShell also lets you set rules for the Windows firewall on web servers and comes with the advantage of scripting and automating the configuration work. To create a new firewall rule, for example, use:
New-NetFirewallRule -DisplayName "ICMP block" -Direction Inbound -Protocol icmp4 -Action Block
As you can see, you need to specify the name of the protocol, define the protocol, and control the respective action. Instead of creating a new firewall rule with New-NetFirewallRule, it is often easier to copy existing firewall rules with the Copy-NetFirewallRule command. If you work with IPsec, you can also copy the rules with the Copy-NetIPsecRule cmdlet. Of course, after you copy a rule, you can rename it with Rename-NetFirewallRule, although you can assign a new name as soon as you copy it:
Copy-NetFirewallRule -DisplayName "Require Outbound Authentication" -NewName "Alternate Require Outbound Authentication"
Firewall rules in PowerShell can also be deleted with Remove-NetFirewallRule.
Securing Access
The IP Address and Domain Restrictions feature lets you create access rules to block access to predefined IP ranges and domains. To begin, enable the Edit Feature Settings option. You must install the IP and Domain Restrictions role service.
HTTP redirection means that all access to a specific URL is automatically redirected to another URL. For example, you can redirect your site if you are currently editing parts of it. You could have, say, all requests to http://www.contoso.com/marketing/default.aspx redirected to the http://www.contoso.com/sales/default.aspx site. Redirections can be configured at the server or website level by the HTTP Redirection feature. However, you must first install this feature as a role service.
In addition to redirection, you can also define the behavior of the configuration at this point. If you check the Redirect all requests to the exact destination (instead of relative to destination) box, requests are always redirected to exactly the address you specified in the redirection. This also applies when requests are sent to subfolders. If you select the Only redirect requests to content in this directory (not subdirectories) checkbox, the server will redirect requests that are directed to subfolders of the redirected folder directly to the redirection target.
You can set the SSL bindings for web pages in IIS Manager or you can use Windows Admin Center and the IIS extension. Unencrypted access to IIS on SSL pages also can be redirect automatically, for which Microsoft provides the free URL Rewrite [2] extension. In the IIS Manager, first install the extension and then call URL Rewrite. Add Rule lets you create new rules (Figure 4).
You can also redirect manually in two ways. For the first method, you can define the corresponding settings in the configuration of the HTTP 403 error message by calling the IIS Manager on the server and clicking on the server name and the website. The Error Pages option is found here, as well. Now double-click on the error pages in the IIS section on the start page and open the 403 error item. Now activate the Respond with a 302 redirect option, enter the HTTPS URL that the users should access, and press OK to confirm.
This type of redirection does not always work. In this case, use the second option for redirection. Start IIS Manager and click on the page for which you want to configure HTTP redirection. Click Bindings and change the binding port from 80 to another free port (e.g., 8001). Now right-click Sites and create a new site with the Add command. As the site name, in the Add Site Binding dialog, assign to the new website the name that users will use to access the server over HTTP (e.g., powerpivot.contoso.int). Now create a physical path. The folder remains empty; you only need it for IIS, not for the configuration. Leave the binding set to port 80. Because you have already changed the binding of the default page, this port is available. As the hostname, enter the name to which you want the server to respond (e.g., powerpivot.contoso.int).
After you confirm that you want to create the website, you will then receive a message that port 80 is already in use because port 80 is still assigned to the default website in IIS, even if you changed the port of the site from 80 to another port. However, this page is closed during the install, so it has no significance to the server. Next, click on the newly created page and then double-click HTTP Redirect in the IIS section.
Check the Redirect requests to this destination box and enter the HTTPS address to which you want the server to redirect the requests. Check the Redirect all requests to exact destination box and then press Apply. If users now enter the URL for which you have configured redirection, IIS will detect this access and automatically redirect the request.
Activating and Configuring Logging
In addition to tracking failed requests, you can also log normal IIS operations through the Logging item on the IIS Manager home page. Logging can be enabled for individual pages and applications separately in the Actions area of the console. By default, logging is enabled for the server itself and for websites.
Logfiles can be saved in any folder. By default, the files end up in the \inetpub\logs\LogFiles folder. In the first selection field, you need to specify in the listbox whether you want to create a logfile for each web page or a file for the entire server. Various logfile formats are available; however, you should leave logfile encoding set to UTF 8. Logfile formats include:
- W3C (default): These logfiles are stored as text; the Select Fields button lets you specify what should be logged in the file. The individual fields are separated by spaces.
- IIS: This selection also saves the logfiles in text format; however, the comma-separated individual fields are fixed and therefore cannot be adjusted.
- NCSA (National Center for Supercomputing Applications): Here, too, the fields are fixed, and less information is logged than with the other protocol methods.
In this window, you also specify when new logfiles should be created – according to a certain schedule (hourly, daily, weekly, or monthly), according to a certain size, or not at all. The selection depends on, among other things, the number of visitors to the server. If you do not check the Use local time for file naming and rollover option, UTC (world time) is used by default.
Optimizing Server Performance
Compression can improve server response times and save bandwidth when transmitting web pages. You can manage compression with the feature of the same name in IIS Manager. Some settings are only available at the server level. However, many settings can also be made at the website and application levels, so each application uses its own settings for compression. Enabling compression will increase the load on the server hardware.
Parts of the websites can be made available in the web server's cache, so retrieving these parts does not expose the server to load. You can use the Output Caching feature in IIS Manager to manage this feature. The cache is enabled by default, and you can set limits in the settings; however, the cache is only useful in production after you have defined rules to determine which data you want the server to cache.
Remote IIS Management
In PowerShell and Windows Admin Center, you can access a server running IIS over the network. Although this is also possible with IIS Manager, it is far more complicated to configure and use. For example, to open a connection, use:
Enter-PSSession -ComputerName <Servername>
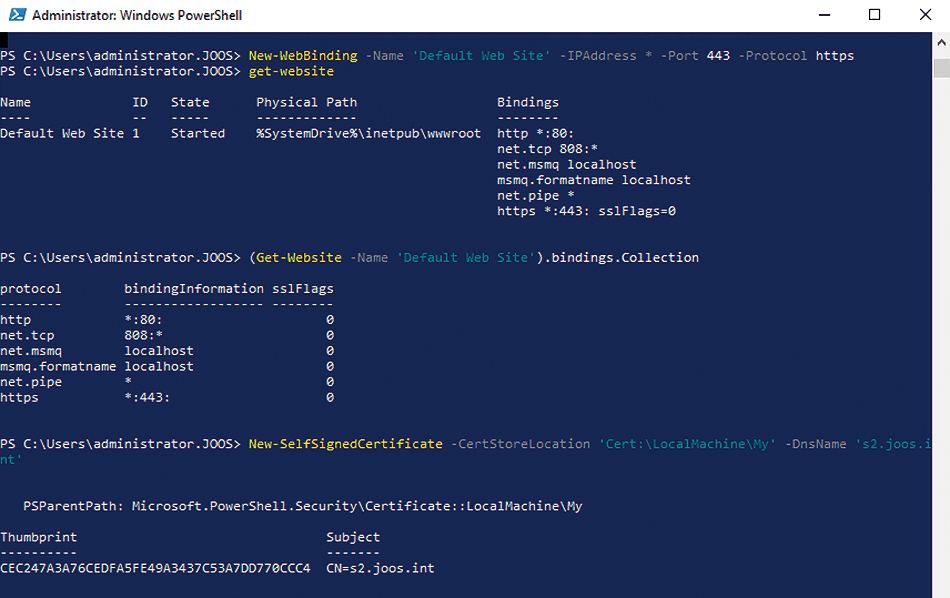
Get-Website displays the websites on the server, including the bindings and all settings. You can see the individual bindings by typing Get-WebBinding, which lets you check which websites are available on a server and which bindings are in use. From this information, you can also add bindings to websites (e.g., for the use of SSL). To create a new binding, for example, to enable SSL for a site, enter:
New-WebBinding -Name '<Site name>' -IPAddress * -Port 443 -Protocol https
The two Get- commands mentioned earlier then show the successful binding (Figure 5). In PowerShell, you can also output the bindings specifically for a website,
(Get-Website -Name '<Default Website>').bindings.Collection
as shown in Figure 5.
Self-Signed Certificates
For connection security, IIS also supports self-signed certificates with the New-SelfSignedCertificate cmdlet. To create a self-signed certificate for a web page (Figure 5), type:
New-SelfSignedCertificate -CertStoreLocation '<Cert:\LocalMachine\My>' -DnsName '<s2.joos.int>'
The certificate is then connected to the website and requires the fingerprint of the certificate, which is displayed during the create process:
$certPath = 'Cert:<\LocalMachine\My\> CEC247<...>CCC4' $providerPath = 'IIS:\SSLBindings\0.0.0.0!443' Get-Item $certPath | New-Item $providerPath
You can also check the bindings in IIS Manager or with Windows Admin Center. To do so, call up the settings of the website and check to see whether the certificate has been accepted and the settings have been set. In Windows Admin Center, you will find the options under Bindings.
IIS in Windows Server 2016 and 2019 also supports HTTP/2, and you can use wildcards for the host header:
New-WebBinding -Name "Default Web Site" -IPAddress "*" -Port 80 -HostHeader "*.contoso.com"
If you want to prevent the web server from advertising itself externally as an IIS 10 server, enter
Set-WebConfigurationProperty -pspath 'MACHINE/WEBROOT/APPHOST' -filter "system.webServer/security/requestFiltering" -name "removeServerHeader" -value "True"
to remove the server header.
Conclusions
IIS can be configured in several ways. Not surprisingly, PowerShell is one of them, which allows you to save actions as scripts and execute them repeatedly and, if necessary, automatically. The second common approach is from Windows Admin Center. IIS Manager, on the other hand, is no longer the tool of choice. Regardless of which tool you choose, the motto has to be: security first!
