
Seven free blocking filters for ads
Ads Subtracted
Some websites overdo advertisements, piling on pop-ups, video snippets, and product placements in your browser. If the editorial content only appears as an afterthought, it's time to filter out the ads.
An ad filter can be applied to each individual device or make the ad invisible for all clients on a network at a central location. In this article, I compare ad blockers that run on the router or on a device on the network, in which case, the terminal devices do not require any additional software.
Requirements
The ideal setup would have an ad blocker running on low-cost hardware or directly on the existing router, and I would like to be able to make changes to the blacklists if the software filters out too much (or too little).
The ad filter must function in the local language. Even the best software is useless if it does not recognize regional advertising. Finally, I want the ad blocker to prevent access to websites with dubious content or adult entertainment, where applicable.
Candidates
The test candidates come in the form of add-ons for an existing (router) operating system or as additional hardware. Pi-hole, the best-known candidate, has to face the challenger AdGuard Home and the outsider eBlocker. pfBlockerNG, Unbound-Plus, and Adblock join the fray for networks with pfSense, OPNsense, and OpenWrt, respectively. The NxFilter DNS appliance rounds out the list.
All candidates in Table 1 are free of charge and use free blacklists. If no suitable hardware is available on the local network, costs are incurred for a small-board computer (SBC) such as a Raspberry Pi.
Tabelle 1: Ad Filters
|
Software |
Adblock |
AdGuard Home |
eBlocker |
NxFilter |
pfBlockerNG |
Pi-hole |
Unbound-Plus |
|---|---|---|---|---|---|---|---|
|
Examined Version |
3.8.15-1 |
0.102.0 |
02.04.05 |
04.03.06 |
2.1.4_21 |
5.0 |
0.5 |
|
Origin |
Germany |
Russia |
Germany |
Korea |
USA/Canada |
USA |
Austria/Czech Republic |
|
Popularity |
+ |
++ |
+ |
+ |
+++ |
+++++ |
+ |
|
Language |
Ash |
Go |
Java, Ruby |
Java |
Shell |
Bash, PHP, C |
Python |
|
Platform |
OpenWrt |
Linux, FreeBSD, macOS |
Rasp Pi 2/3/4 |
Linux, macOS, Windows |
pfSense |
Linux |
OPNsense |
|
Available Since |
2015 |
2018 |
2016 |
2013 |
2015 |
2016 |
2019 |
|
Mode of Operation |
DNS sinkhole |
DNS sinkhole |
DNS sinkhole or firewall |
DNS sinkhole |
Firewall rule |
DNS sinkhole |
DNS sinkhole |
|
Multilanguage Blocking Lists |
+ |
+(1) |
+ |
+(1) |
+(1) |
+ |
+(1) |
|
Additional Blacklists |
+ |
+ |
+ |
+ |
+ |
+ |
+ |
|
License |
GPLv3 |
GPLv3 |
EUPL |
EUPL free for up to 25 users |
Apache v2 |
EUPL v1.2 |
BSD 2-clause "Simplified" |
|
DHCP Server |
+(1) |
+ |
– |
– |
+ |
+ |
+ |
|
Hardware Costs (approx.) |
$45 |
$50 |
$50 |
$50 |
$150 |
$50 |
$150 |
|
Admin Interface |
+ |
+ |
+ |
+ |
+ |
+ |
+ |
|
Graphical Evaluation |
– |
+ |
– |
+ |
– |
+ |
– |
|
Protection of Minors |
– |
+ |
+ |
+ |
+(2) |
– |
– |
|
Safe Search |
– |
+ |
– |
+ |
+(2) |
– |
– |
|
DNS over HTTPS |
– |
+ |
– |
+ |
+ |
+(3) |
+ |
|
Clients Individually Configurable |
– |
+ |
+ |
+ |
+(2) |
+ |
– |
|
(1) Upgradable. (2) With pfSense methods (complex in part). (3) Manual adaptation at the command line. |
|||||||
Black Holes
Most ad filters work on the same principle: They integrate into the network as DNS servers and respond to queries from the clients. The terminal devices ask the new DNS server for name resolution and receive a stored IP address.
Unlike a conventional DNS server, however, the ad blocker answers those DNS queries that are on its blacklist with a shrug of the shoulders (i.e., a DNS sinkhole). From the client's point of view, this website does not exist, and the browser cannot load the advertisement.
How does the advertising filter know that a DNS query leads to an advertising domain? The software uses publicly available lists that collect web addresses and domains for advertising. These blacklists work like spam lists for email servers.
Pi-hole
Probably the best known representative of the free advertising blockers is Pi-hole [1]. The installation wizard is straightforward and can be used by Linux newcomers. After a short question and answer session, the installer leaves a preconfigured ad filter and links to the local website for administration and evaluation. Finished now at the command line, the user does the rest from a web page. With the use of preset blacklists, Pi-hole automatically loads almost 125,000 entries into its DNS service and starts working.
Pi-hole was designed for the Raspberry Pi, but it also runs on other SBCs or as a virtual machine. Even in large environments, the service cuts a fine figure. In a field test, it ran on a corporate network with about 1,200 clients without any performance losses or downtime.
Pi-hole's evaluation feature provides statistics in real time. The graphs in Figure 1 show the DNS load of all clients within a 24-hour period and the top 10 allowed and blocked websites.
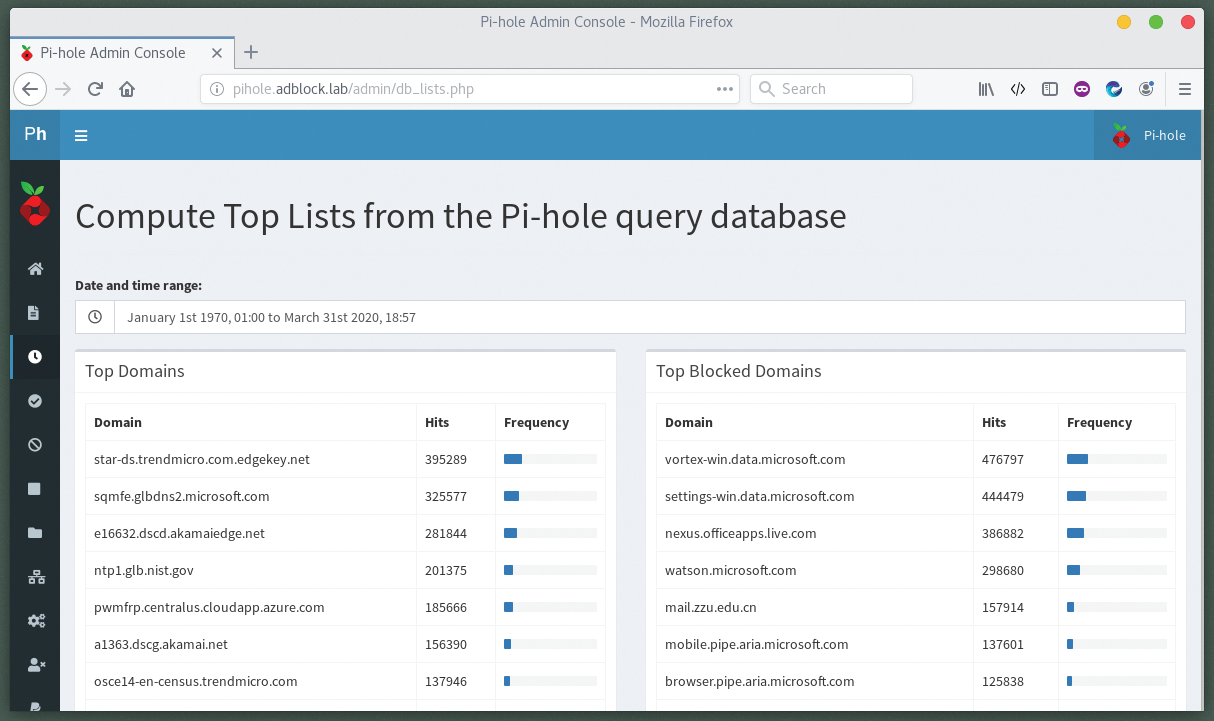
Synopsis
The well-documented Pi-hole is easy to install, and it works immediately. With only a few possible tweaks, it is therefore suitable for newcomers. As of recently, it can handle different clients differently and provide individual end devices (e.g., smartphones for minors) special protection.
AdGuard Home
AdGuard Software Limited began developing ad blockers for web browsers [2] and then expanded its concept with AdGuard Home [3] to include network-based blockers. The software does not prefer any particular hardware and is suitable for all SBCs that come with Linux or BSD. Additionally, the ad blocker can run piggyback on an existing firewall.
When AdGuard Home is started in the console for the first time, the command output points to a local web address. The web interface guides the user through further configuration. After the last step, AdGuard is ready for use and runs as a DNS server with an active blacklist. Up to this point, AdGuard is hardly different from Pi-hole. However, the preset blacklists prove to be a little bit gappy for non-English markets. Language add-ons in the form of EasyList [4] are recommended.
AdGuard Home does not treat all clients equally and can handle certain end devices separately to exclude individual clients or IP ranges from adult content or to force safe search (Figure 2). Additionally, AdGuard Home blocks services such as Steam, Netflix, and Skype – either per client or for all clients.
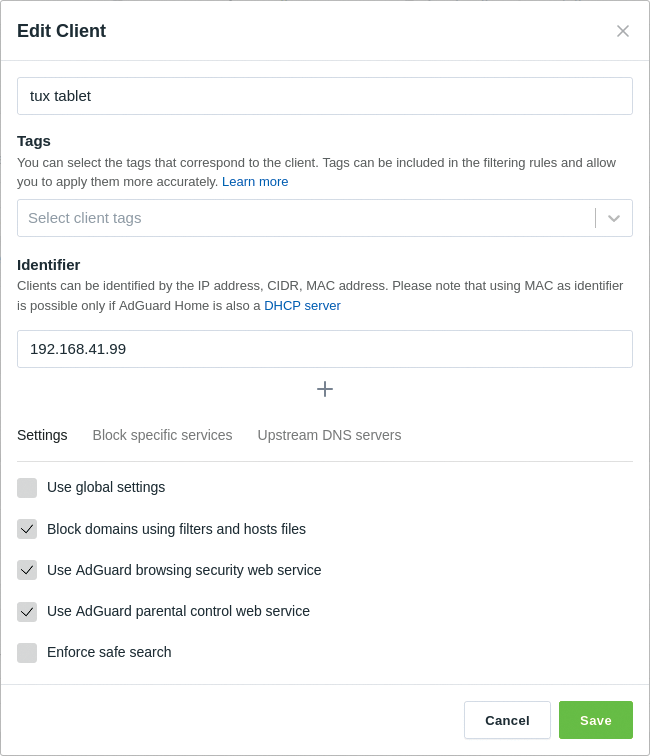
Synopsis
AdGuard Home is optimally suited for environments with different protection requirements. Individual clients can be restricted with parental control, Internet security, or safe search. Additional blacklists compensate for weak support for non-English markets.
NxFilter
The full-fledged NxFilter DNS appliance [5] can filter by categories and policies. Advertising is just one of many categories that the software hides in DNS responses.
NxFilter is based on Java and therefore runs on Linux, Windows, and macOS. It is licensed under a commercial Linux license, which remains free of charge for up to 25 clients. By default, it runs as a regular DNS server without filtering.
From the NxFilter web interface, you can create policies that filter out certain categories or keywords. The policies created apply to individual clients or to specific users in an Active Directory domain. The possibility of integration with Active Directory, OpenLDAP, or RADIUS makes it clear that NxFilter works best on corporate networks. However, the category filter is also attractive for home use; for example, websites about alcohol, tobacco, and gambling can be inaccessible to the smartphones of underage children.
Out of the box, NxFilter does not use blacklists; rather, it compares the accessed domain with predefined patterns and finds the stored category. These search patterns can be flexibly adapted and represent a unique selling point of NxFilter.
Synopsis
NxFilter can define in a very granular way what clients are allowed access by web page or category. For home networks, this granularity seems almost over the top. Despite the potential complexity, NxFilter can be quickly installed and set up with a simple policy.
pfBlockerNG
If you have a pfSense firewall protecting your network, the pfBlockerNG plugin [6] can give you an ad blocker on top. The installation can be completed quickly with the integrated package manager. The setup is more complex, because pfBlockerNG comes with additional filters for GeoIP and reputation.
After embedding the plugin in the firewall, a variety of options are available in the web-based menu. Under the DNSBL tab, you will find the advertising filter (disabled by default) together with the EasyList blacklists (Figure 3).
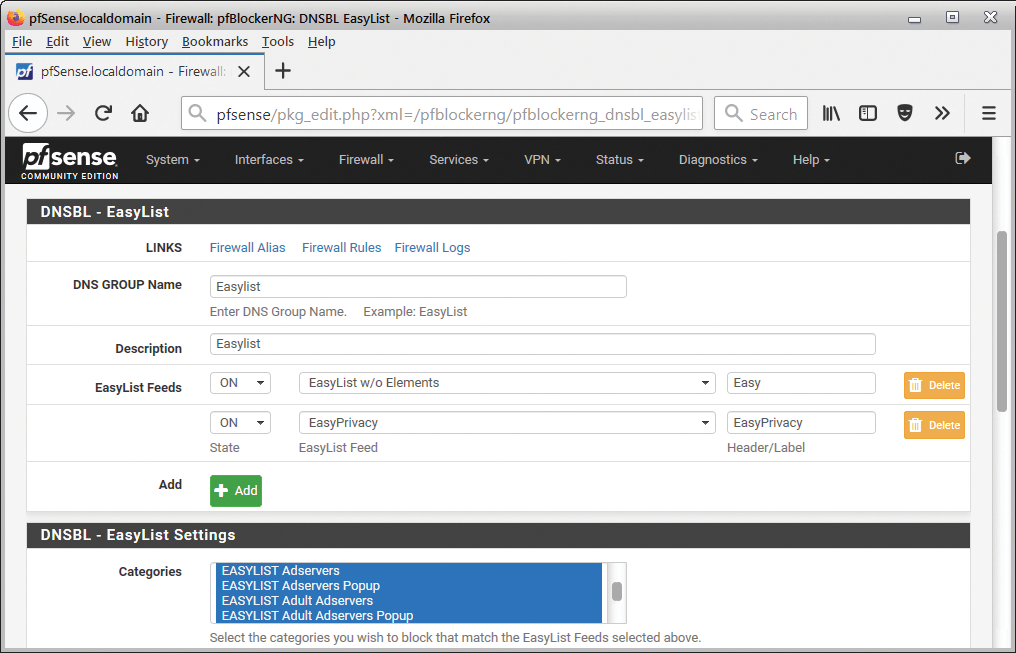
pfBlockerNG can provide more than one DNS server with blacklists on the network. The plugin integrates into the pfSense web interface and can create complex policies. The firewall rules constructed by the plugin can filter (or allow) traffic according to the credibility or geographic origin of a server IP address. Besides these nice features, pfBlockerNG also has the basics: additional blacklists, your own exceptions, and logging.
pfBlockerNG keeps its clients firmly in hand, because the data traffic runs through the firewall and not past it, as with Pi-hole and AdGuard. Because of its central position, the advertising filter cannot be bypassed. The firewall policy applies to the connected devices, whether they like it or not, which makes pfBlockerNG suitable for environments in which users perceive the filter as a restriction rather than a protector.
Synopsis
pfBlockerNG is intended exclusively for owners of a pfSense firewall. With its ad blocker and GeoIP filter, the plugin makes the firewall more versatile, but also makes its configuration more complex. Once successfully set up, clients are no longer able to slip past the policy. In addition to pfBlockerNG, AdGuard Home also runs on pfSense and can be a useful addition to the firewall.
Adblock
Adblock [7], the in-house advertising filter from the OpenWrt free router project, can be installed as a package and integrates seamlessly into the configuration interface. Before launching, it offers a variety of blacklists, subdivided by topic, provider, and country.
Adblock works like other ad blockers: load blacklists, fill the DNS service with the lists, and collect statistics. Adblock is the only candidate that can send email if the ad blocker encounters errors. Further feedback is provided in the form of the DNS request report, which counts the corresponding requests and divides them into blocked and allowed domains.
The combination of Adblock and OpenWrt requires very little memory, which makes this ad blocker ideal for use on low-powered routers. If memory is still scarce, OpenWrt also offers a memory-optimized variant named Simple Adblock in its repository.
Synopsis
Adblock is a full-featured, unadorned advertising filter for an OpenWrt router. The installation and setup are problem-free; most of the checkboxes on the configuration page are already set. The remarkably wide selection of blacklists also takes non-English websites into account. Logging and reporting are limited to the bare essentials, which is an advantage for the target group of embedded systems.
Unbound-Plus
Unbound-Plus is an add-on for OPNsense firewalls. The software fetches various blacklists from the Internet and fills the local Unbound DNS server, resulting in a simple advertising filter. However, Unbound-Plus is still in the development stage, which occasionally causes issues.
Unbound-Plus integrates with the OPNsense website. During the configuration, you can select from 24 default blacklists and add your own (Figure 4). The decision applies to all clients on the network; specific terminal devices cannot be excluded. Statistics on the advertising filter and the ability to create an exception if the filter classifies a website inappropriately are missing.
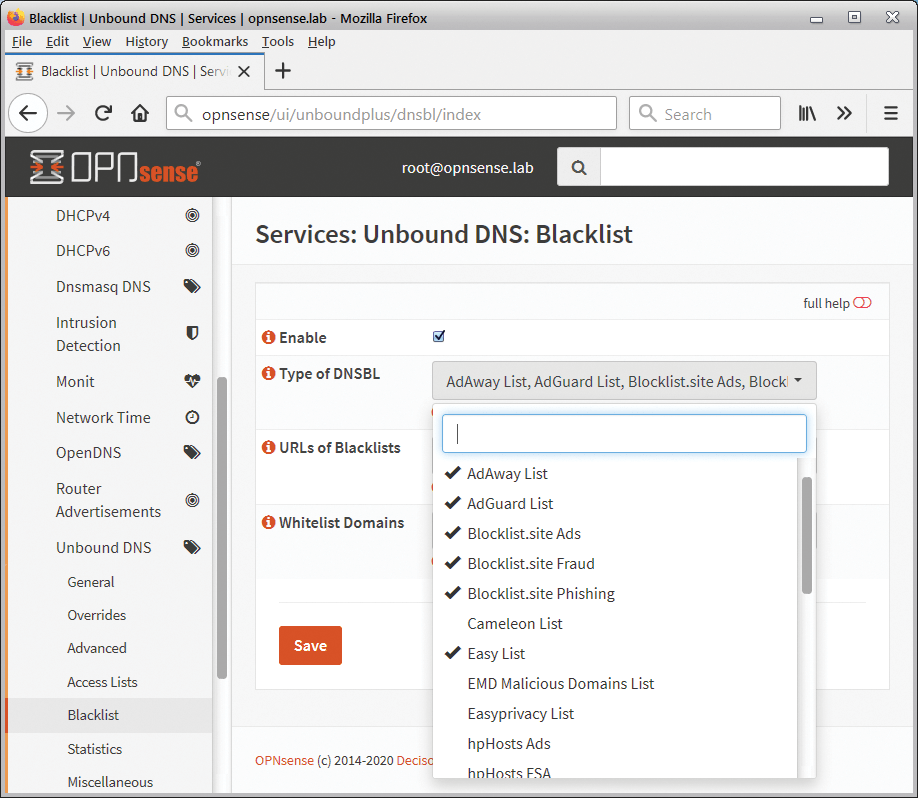
Synopsis
Unbound-Plus gives an existing OPNsense firewall a simple ad blocker. Other than the blacklists, the plugin does not offer many features, perhaps because of its unfinished state of development. If the focus is on stability, AdGuard Home can also run on the OPNsense firewall and protect the network.
eBlocker
eBlocker [8] started as a commercial company, but in 2020 it became a free, open source project. The strength of eBlocker lies not only in ad filtering – the software also allows anonymous surfing and the protection of minors. Although it comes as a ready-to-install image for the Raspberry Pi or the Banana Pi, other platforms are not available.
The developers claim eBlocker is a plug-and-play solution for home networks. According to the marketing, the software protects all users on the local network as soon as they connect. The eBlocker website shows protected devices, filter lists, and categories.
Of all tested advertising filters, eBlocker most seriously intervenes with on-going communications. The new device acts as a standard gateway for other clients and thus (willingly) hijacks all Internet requests from the other participants.
As a classic man in the middle (MITM), eBlocker can check the data packets that flow through for advertising and malware. eBlocker reacts to encrypted connections with TLS inspection, thanks to which, it can even sniff HTTPS connections. However, this feature is not automatically active and requires a certificate on each end device that authorizes eBlocker for deep packet inspection. For anonymization purposes, eBlocker can route traffic through a VPN provider or through the Tor network.
On the downside, eBlocker gains deep insights into data communications and thus also sees passwords, bank transfers, and confidential information. Because the service is already in the communication path, the web browser will not output a certificate warning if an MITM attack actually occurs.
Furthermore, the eBlocker only protects clients it has found on the local Ethernet segment. Clients on other networks (WiFi, guest network) remain unaffected and surf the Internet without protection. Finally, not all home routers cooperate with eBlocker, and depending on the model and manufacturer, plug-and-play can become a manual setup operation.
Synopsis
eBlocker uses blatant tools to hijack client communication. As an intentional MITM, it uses a collection of ARP spoofing, SSL bumping, and DNS blocking to protect its clients from malware, advertising, and data collectors, thus proving to be an ideal supplement if the DSL router is the only line of defense on the network. eBlocker also consistently enforces the Internet rules negotiated by parents and children.
Making It Work
For the ad blockers presented here to work, the clients must use the new DNS server for name resolution or as their default gateway. If the end devices get their IP addresses by DHCP, the DHCP server now has to include the new ad blocker as a DNS server or gateway in its offerings. For static addresses, manual changes are required in the IP settings of the respective devices.
In small environments, the DSL router takes over the role of the DHCP and DNS server in most cases. If the DSL router always asserts itself as the DNS server, the clients cannot use the new DNS server. In this case, the DSL router has to give up its DHCP task. Fortunately, the ad blockers can help out. All examined systems offer a DHCP server or can at least be upgraded accordingly.
eBlocker takes a different approach, making itself the default gateway. It not only controls the DNS queries, but also has access to the complete data stream. If desired, the sniffer box will peek into HTTPS traffic, although this option is disabled out of the box.
DIY
If none of the presented software projects is suitable, you can build an ad filter yourself with manageable overhead. You don't have to reinvent the wheel, because the candidates presented reveal the concept: Download and fill the DNS server with blacklists.
One possible setup consists of a Raspberry Pi, which you connect directly to the rest of the network by cable, and the dnsmasq DNS server (Listing 1, line 1). A blacklist turns the DNS service into an advertising filter. To keep the conversion work low, I recommend using a blacklist that is already available in the appropriate format for dnsmasq (line 2).
Listing 1: Homemade Ad Blocker
01 $ sudo apt install dnsmasq 02 $ curl https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts >/tmp/blocklist.txt 03 $ cat <<EOF > /etc/dnsmasq.d/adblock 04 addn-hosts=/tmp/blocklist.txt 05 EOF 06 $ sudo systemctl restart dnsmasq 07 $ sudo pkill -USR1 dnsmasq
Dnsmasq learns the content of the blacklist from an entry in its configuration (lines 3-5). The service then restarts (line 6) and begins its new role as an advertising filter.
A quick test in your browser can show whether the do-it-yourself design really filters ads from websites. Because dnsmasq on the Raspberry Pi can be reached over the network, a test client can enter the IP address of the Rasp Pi in its DNS settings. After that, the personally known websites should contain less advertising.
For regular updates of the blacklist, just turn to the usual suspect: cron. Dnsmasq writes a usage report to the journal as soon as the process receives the USR1 signal (line 7).
Optimized
The presented ad filters achieve a common goal, but each offering has its individual strengths and fits the bill for different target groups.
Pi-hole is suitable for large environments of clients with similar protection needs. AdGuard Home, on the other hand, ideally operates on networks with different protection requirements (e.g., on a home network) by providing children with a safe search feature and youth protection, guests with an advertising filter, and your own PCs with tracking protection.
NxFilter fits if you have complex policies and extensive category filters with a connection to a directory server. However, costs are incurred for this service from 25 users upward. pfBlockerNG is suitable if a pfSense firewall is already in use: In this case, reputation and GeoIP are added to the ad blocker, and no one can cheat their way past.
Adblock scores points if the available (router) hardware has too little memory for a "big" ad filter. On small networks with high protection requirements and a focus on anonymization, tracking, and youth protection, eBlocker plays to its strengths.
Limits
Website operators prefer to place their advertising in such a way that ad blockers do not recognize it, and the brand message gets through to the user. Regular advertising can still be hidden with up-to-date blacklists.
Stubborn advertisements that are in the encrypted data stream remain undetected (except by eBlocker). In this case, the ad filter would have to intervene in the data stream with TLS inspection and examine the content: Although possible, this operation is complex and not entirely harmless [9]. Advertising during YouTube videos thus remains an annoying five-second evil.
An experienced user can easily bypass the DNS-based ad blocker by specifying a different DNS server in their IP settings. In these cases, advertising filters on a firewall score points by preventing access to other DNS servers or redirecting attempts to the desired advertising filter. In simple environments with residential gateway devices (e.g., FRITZ!Box) and Pi-hole, this workaround will not work.
The situation becomes tricky when the web browser tries to use a DNS server on the Internet for name resolution and encrypts its requests with DNS over HTTPS (DoH). In this case, the firewall cannot detect whether the client is surfing a web page or resolving a hostname.
The popular browsers recently started to support DoH, although the option is disabled by default. If you want the ad blocker to protect clients in the future, then make sure they do not use DoH. Ironically, many ad blockers support DoH, but only between the filter box and the DNS server, not between the filter box and the devices on the home network.
The logfile on the DNS server collects the domains called by network participants, as well as the IP addresses of the clients (i.e., personal data). This should set off privacy alarms, because storing and processing this data is subject to data protection laws. In addition to the option of disabling logging completely, Pi-hole can omit the domain, the client, or both in its logs [10]. AdGuard Home anonymizes at least the IP address, if so desired.
Detecting Ad Blockers
An advertising filter reduces the financial income of a website. Some websites ask their customers to turn off advertising blockers and hope for some understanding. On the other hand, some websites refuse to make headlines if the viewer removes the advertising.
Ad blockers can be detected because the website sends a piece of JavaScript to the browser to load an advertisement. If this operation does not succeed, some kind of advertising filter is obviously involved. The web developer can react to this information and restrict the content or activate a paywall.
Analytics services for advertising evaluate how many users were able to block the advertising and which website content was visible. Like Google Analytics, but for advertisements.
Outlook
An advertising filter does not have to sit next to your router as an SBC, but it can protect computers as a cloud service. An Ad Blocker-as-a-Service offers a great alternative if no local hardware is desired or possible. Large providers like OpenDNS [11] or Alternate DNS [12] work just like domestic ad blockers, although the cloud providers do not let you see what they are doing (i.e., the blacklists are proprietary).
You can also take an approach without the cloud or additional hardware. Routers often support filter lists and can thus restrict access to (advertising) pages. However, lists often are not updated automatically. This "Ad Blocker Light" therefore requires occasional manual refueling of the filter lists.
Conclusions
Advertising is a legitimate way to finance a website. However, many providers overdo it, and the desired content drowns in a flood of intrusive pop-ups. For this kind of website, it makes sense to use an ad blocker to make the annoying insertions disappear.
Most ad killers also protect you against data collection, block malware, and filter out content harmful to minors, if necessary, so an ad blocker is part of a basic networking toolkit.
By the way, in our lab, some websites slipped through the grid that should have been taken out by the category filter. A smart teenager or break-out-oriented employee will probably try alternative websites and possibly outwit features for the protection of minors.
