11 Tricks for Windows servers
Knowledge
Fine-tuning Windows servers doesn't have to be a complex process. Easily manageable commands and settings can have a great effect. In this article, I look at 11 practical tips for Windows servers.
1. Remote Desktop Settings
In many organizations, employees use the Remote Desktop tool, usually activated in the server's graphical user interface or from the Server Core text-based menu. On servers with a graphical user interface, the quickest way to find the settings is to call sysdm.cpl. However, you can also enable the remote desktop from the registry with the settings found in the HKLM | SYSTEM | CurrentControlSet | Control | Terminal Server key. With this approach, you can activate Remote Desktop by importing registry entries. The most important entry is fDenyTSConnection. A value of 0 activates Remote Desktop, and a value of 1 disables it. To see which users are connected to a server (Figure 1), run the command:
qwinsta /server:<server name>
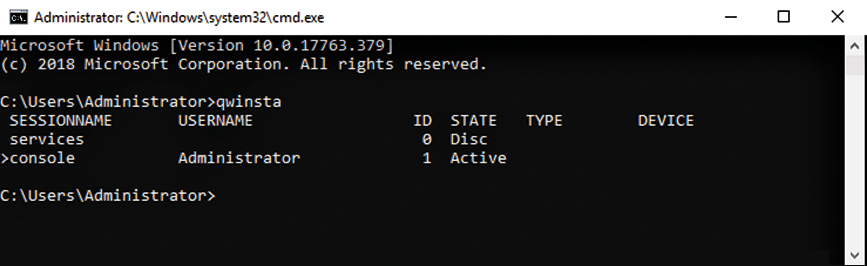
qwinsta command.To deny access to certain users, use group policies. To block access to the Remote Desktop Services (e.g., for local administrators), you should manage the authorizations centrally. The path to the settings is Computer Configuration | Windows Settings | Security Settings | Local Policies | User Rights Assignment. The following two settings are important:
- Deny log on through Remote Desktop Services
- Deny log on locally
Here, you configure which users are allowed to log on to the server locally (i.e., directly at the console) and which users can connect to the server by Remote Desktop. Remote Desktop connections can also be used in the web browser if you use Windows Admin Center. The Remote Desktop menu item waits for connections and allows you to open a session.
2. Uninstalling Media Player
By default, Windows Media Player is installed on Windows Server 2019. Because this tool is not needed on production servers, it is an unnecessary function and therefore a potential vulnerability. To uninstall Media Player, run the command:
dism /online /Disable-Feature /FeatureName:WindowsMediaPlayer /norestart
The command is also useful for deployment scripts or tools that distribute automatic settings to servers. Besides the Windows Admin Center and Server Manager, Media Player can also be uninstalled with the PowerShell command:
Disable-WindowsOptionalFeature -Online -FeatureName WindowsMediaPlayer
3. Configuring LDAP Priorities and Weighting
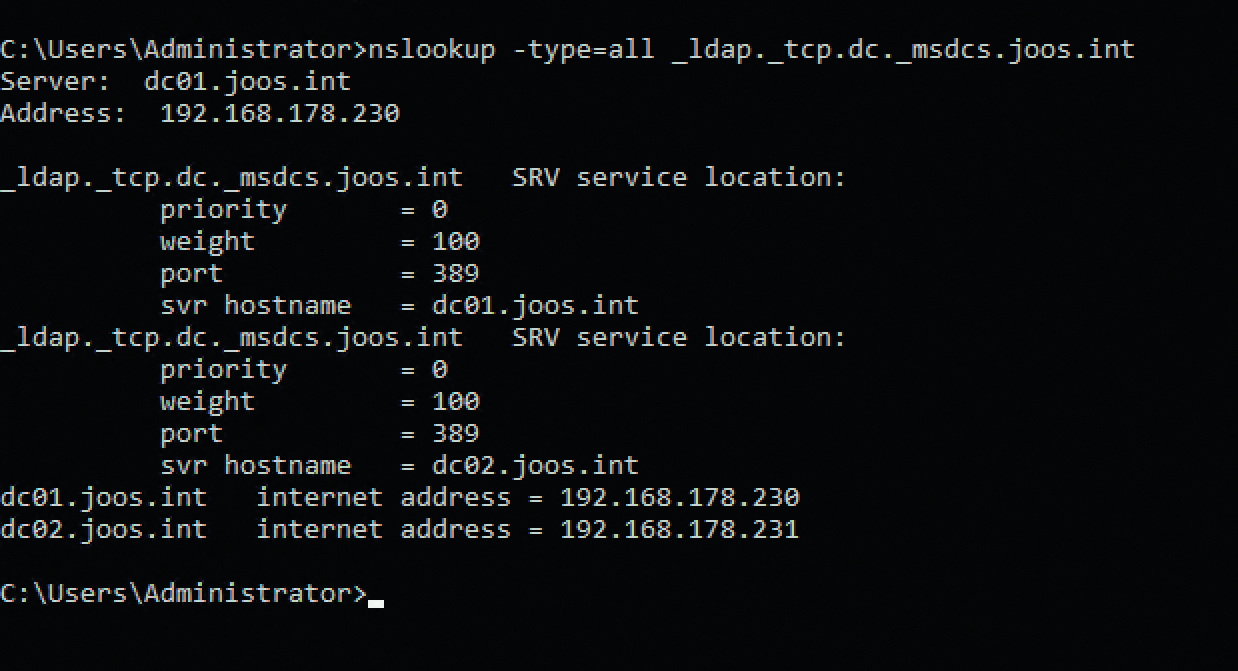
Checking that the LDAP SRV entries are correct in the domain name system (DNS) can help you detect Active Directory (AD) issues. Correct accessibility of domain controllers (DCs) in the SRV entries is an important basis for many server-based services. You can launch the check with the fully qualified domain name (FQDN; e.g., joos.int in this example):
nslookup -type=all _ldap._tcp.dc._msdcs.joos.int
Domain controllers register multiple SRV records (Figure 2), which in turn tell clients to which DCs they should connect. If you set the priority to a high value (e.g., 1), these DCs are only addressed if no other DCs with a priority of 0 exist. The weighting distinguishes DCs with the same priority. A DC with a weighting of 10 is addressed more often than a DC with a weighting of 5. In other words, you can relieve the load on individual DCs by adjusting the weighting. This procedure is also useful if you want to replace a DC and reduce the number of requests on the server.
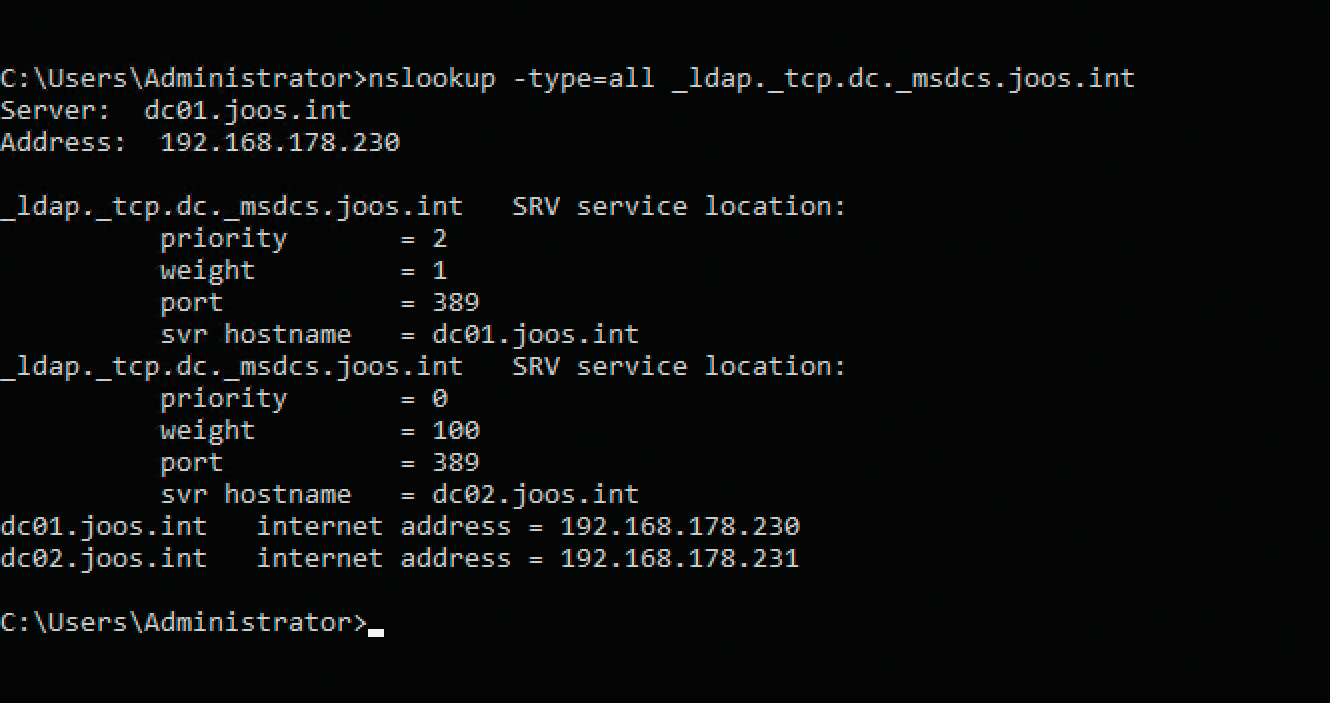
The settings for weighting can be seen in the properties of the DNS record. The priority and the weighting are defined by registry entries, which can be found in the DC registry key at HKEY_LOCAL_MACHINE | SYSTEM | CurrentControlSet | Services | Netlogon | Parameters, where you enter the weighting and priority:
- "LdapSrvWeight"=dword:00000001
- "LdapSrvPriority"=dword:00000002
In most cases, you will have to create the two DWORD values again, which are enabled either after restarting the DC or after restarting the login service:
net stop NETLOGON && net start NETLOGON
To display the current values, again run the command:
nslookup -type=all _ldap._tcp.dc._msdcs.joos.int
The entries are displayed in the DNS record properties in the priority and weight fields (Figure 3).
4. Blocking DNS Queries
In Windows Server 2016 and 2019, DNS policies can be defined to block queries from clients. Configuration is made with PowerShell, and the settings are implemented on the individual DNS servers. (For information about the configuration cmdlets, see the Microsoft docs [1]). For example, if you want to block the resolution of the erp01.joos.int server on the 255.255.255.0/24 subnet, you first need to define the appropriate subnet then create a policy that blocks resolving an FQDN from that subnet:
Add-DnsServerClientSubnet -Name "UnsecureSubnet" -IPv4Subnet 255.255.255.0/24 -PassThru Add-DnsServerQueryResolutionPolicy -Name "Block_ERP01" -Action IGNORE -ClientSubnet "EQ,DWPSubnet"-FQDN "EQ,erp01.joos.int" -PassThru
The policies are available in PowerShell; enter
Get-DnsServerQueryResolutionPolicy
to see the policies, or enter
Remove-DnsServerQueryResolutionPolicy -Name "Block_ERP01" -PassThru
to delete the policies.
5. Changing Windows Server Editions
Windows Server 2016 and 2019 let you change the edition on the fly, without reinstalling Windows. For example, if you installed Windows Server 2019 Standard, you can switch to the Datacenter edition. The command to upgrade from Standard to Datacenter is:
Dism /Online /Set-Edition:ServerDatacenter /AcceptEula /ProductKey: <xxxxx-xxxxx-xxxxx-xxxxx-xxxxx>
After the update, restart the server. You can also switch from the trial version of Windows Server 2019 to a full version. The following commands let you see whether you are running a trial version, tell you to which edition you can upgrade, and display your current edition:
slmgr.vbs /dlv dism /online /Get-TargetEditions dism/ online /Get-CurrentEdition
To update the trial version, use the same command as for the upgrade from Standard to Datacenter; that is, you can switch from the Windows Server 2019 Datacenter trial version to the licensed version. The server has to be restarted at least twice, so you can unlock new features like Storage Replica or Storage Spaces Direct. Of course, you will need a valid product key for the change.
6. Starting Safe Mode in Automatic Repair
Interrupting the Windows startup process two or three times starts Windows Automatic Repair. If the server is not working properly, you can start the Windows server in different modes. To switch to Safe Mode, first go to the Repair menu and select See advanced repair options, then Troubleshoot | Advanced options | Windows startup settings. When you click Restart, a system menu appears in which you can Enable Safe Mode.
7. Accessing BPA with PowerShell
The Best Practices Analyzer (BPA) lets Windows Server 2019 check its own health and the installed server roles to look for incorrect configurations. The fastest way to start the BPA is to launch it from PowerShell:
Get-BPAModel | Invoke-BpaModel
If you want to start a scan process for a certain role only, first discover the ID of the corresponding model; then, start the test(s):
Invoke-BPAmodel -modelId Microsoft/Windows/DNServer,Microsoft/Windows/FileServices
You always need to specify the ID as a complete path, which you discover with Get-BPAModel. Hyper-V, for example, has the ID Microsoft/Windows/Hyper-V. You can also use a single command to discover the BPA model and start the scan process immediately:
Get-BPAmodel <ID> | Invoke-BPAmodel
If you do not specify an ID, all roles are scanned. To read the roles and search for the "Error" string, enter:
Get-BpaResult -ModelId Microsoft/Windows/DirectoryServices | Where-Object Severity -eq "Error" | Format-List Title
To display all results from specific server roles (BPA models), use:
Get-BPAResult Microsoft/Windows/DNS Server,Microsoft/Windows/FileServices
You can export the BPA results (e.g., to an HTML file) from PowerShell:
Get-BPAResult <model ID> | convertTo-Html | Set-Content <path>
By way of example, write the information of the file services to an HTML file:
Get-BPAResult Microsoft/Windows/FileServices | convertTo-Html | Set-ContentC:\BPAResults\FileServices.htm
Finally, the command:
Get-BPAResult Microsoft/Windows/FileServices | Export-CSVC:\BPAResults\FileServices.txt
exports the results to a comma-separated values file.
8. Changing the Data Medium Format
You can only convert an MBR disk to a GPT disk and vice versa if the disk is empty. To do this, right-click on the disk in the Windows Disk Manager and select the corresponding command. You can also perform the conversion at the command line. Start a command prompt and type:
diskpart list disk select disk <disk no. to convert>
Now use:
clean convert gpt
The reverse approach uses:
convert mbr
In the Disk Manager (diskmgmt.msc), you can discover the partition style by right-clicking a volume and choosing Properties. In PowerShell, you can display the partition style with
Get-Disk | select FriendlyName, PartitionStyle
To set the partition style to GPT, use the command:
Initialize-Disk <Number> -PartitionStyle GPT
Another example is
Get-Disk 1 | Clear-Disk -RemoveData New-Partition -DiskNumber 1 -UseMaximumSize -IsActive -DriveLetter Z | Format-Volume -FileSystem NTFS -NewFileSystemLabel Data
to create and format a disk.
9. BitLocker Without a TPM Chip
Hard disk encryption with BitLocker usually relies on a Trusted Platform Module (TPM) chip built into the computer. However, it can also be used if no TPM chip is installed. The associated settings are managed with group policies. In the navigation pane, go to Computer Configuration | Administrative Templates | Windows Components | BitLocker Drive Encryption | Operating System Drives. In the right pane, double-click on the Require additional authentication at startup policy and check the Enabled option in the dialog box (Figure 4).
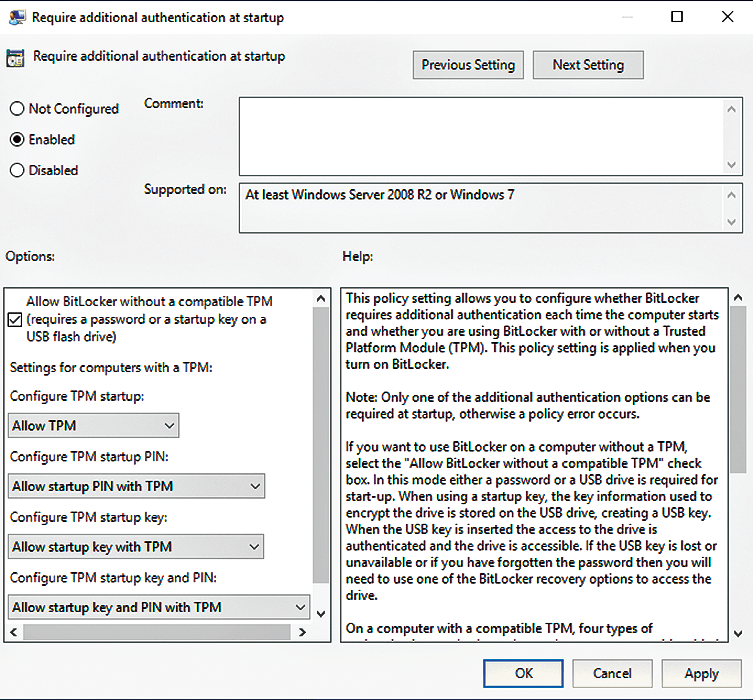
Make sure the Allow BitLocker without a compatible TPM checkbox is selected and click OK. The policy is then assigned the value Enabled in the Status column. After these tasks are complete, you can enable BitLocker.
10. Joining a Domain
To join a computer to a domain, call sysdm.cpl from the Start menu. Click the Change button in the Computer Name tab and enter the name of the computer to be joined to the domain in the Computer description field. Next, activate the Domain option in the Member of section and enter the DNS name of the domain that you want the client to join.
Finally, you need to authenticate against the domain. If the login credentials have been entered successfully, the server is added to the domain. As in previous versions of Windows, you need to reboot the computer after joining the domain. Afterward, you can log on to the domain with your username. You can also use PowerShell,
Rename-Computer -Name <Computername> Add-Computer -DomainName <DomainName> Restart-Computer
to assign names to servers, restart them, and join them to domains.
11. Optimizing DNS Settings for AD
The TCP/IP | Properties | Advanced | DNS IPv4 and IPv6 protocols lets you access additional settings to set up name resolution optimally on the network by DNS or WINS. The individual options play a significant role in name resolution in a DNS infrastructure:
- Append primary and connection specific DNS suffixes: The computer will always try to append the configured primary DNS suffix of its own computer name automatically when resolving computer names. For example, if you want to resolve the dc01 hostname, the computer will attempt a name resolution to dc01.contoso.int if the computer's primary DNS suffix is contoso.int.
- Append parent suffixes of the primary DNS suffix: The names of parent domains are used in name resolution, as well. For example, if you want to resolve a server named dc05 in a subordinate domain named muenchen.de.contoso.int, the computer will first try to resolve dc05.muenchen.de.contoso.int if this is the computer's primary DNS suffix. Afterward, the computer tries to resolve the names dc05.de.contoso.int and then dc05.contoso.int, because these domains are at higher levels compared with the first domain attempted.
- Append these DNS suffixes (in order): This option lets you configure DNS suffixes that resolve incomplete host names. Neither the primary DNS suffix of the server nor the DNS suffixes of this connection are used. Instead, the DNS suffixes are appended in the order configured in this field.
- DNS suffix for this connection: If the computer cannot find the entered name on its configured DNS server by using its own primary DNS suffix, it tries the DNS suffix entered in this field. If you want to resolve a server named dc06, the machine will first try resolving to dc06.contoso.int if that is its primary DNS suffix. However, if you also enter the suffix muenchen.de.microsoft.int, the computer also will try to resolve the name dc06.muenchen.de.microsoft.int.
- Register this connection's addresses in DNS: A DNS server can register entries dynamically. As soon as a computer logs on to the network, it tries to register its FQDN automatically with the configured DNS server.
- Use this connection's DNS suffix in DNS registration: If you enable this option, the server name is registered with its computer name and its primary DNS suffix (i.e., its FQDN).
Conclusions
Many options for tuning Windows servers are not always directly visible or accessible, although the operations involved are often quite simple. Some inside knowledge can make an admin's life far easier. This article reveals a few of the tricks, many of which rely on PowerShell, the Windows admin's best friend.
