
Manipulation detection with AFICK
Checker
AFICK (another file integrity checker) detects changes to the system and sounds an alert. The tool first creates a unique fingerprint of selected files in the form of a checksum. If a different checksum is computed during a later check, a malicious program, an attacker, or a defect is likely to have modified the files under investigation. In this way, AFICK not only detects manipulation attempts, but also acts as a small intrusion detection system.
The tool is licensed under the liberal GNU GPLv3 license, which also allows free use in the enterprise. AFICK only requires Perl v5.10 or newer. Developer Eric Gerbier has tested his tool under all Windows versions from XP upward, various Unix systems (e.g., HPUX and AIX), and numerous Linux distributions (e.g., SUSE, Red Hat, Debian, and Ubuntu). Windows users can easily install Perl with the ActivePerl [1] package.
Most Unix and Linux systems come with Perl by default or support simple installation from the package manager. In addition to the Perl package, you will also want the Digest::MD5, Digest::SHA1, and Perl/Tk modules. The latter two are optional; Perl/Tk is only required for the graphical user interface.
Installation
To install AFICK, first download the latest version from SourceForge [2]. Windows users need the EXE file – at the editorial deadline this was afick-setup-3.6.1.exe. All you have to do is start this program and leave the installation to the wizard, which downloads a few additional Perl modules, so you must have Internet access.
Linux users, on the other hand, have the choice between several packages. Only the packages that start with afick and are immediately followed by the version number (e.g., afick_3.6.1-1_all.deb) are of importance. If you have an Ubuntu-based distribution, you should grab the package with the ubuntu_all.deb extension, and Debian users will want to go for the package with the shorter _all.deb file extension. In both cases, you import the package by typing:
dpkg -i <package name>
On SUSE, openSUSE, Red Hat, and CentOS, you should use the file with the .noarch.rpm extension and install it with:
rpm -Uvh <package name>
On all other distributions and Unix systems, make sure you have the make tool on your computer before downloading and unpacking the .tgz archive. From the newly created directory, call the commands:
perl Makefile.pl sudo make all
The first of these commands prepares the installation process and provides an overview of all the required Perl modules. The second command installs AFICK in the /opt/afick directory. Because of the manual installation, you will always have to update the tool manually in the future by simply installing the new version over the old one.
Creating Checksums
A configuration file informs the tool which files and directories you want AFICK to monitor. Windows users can find it in the C:\Programs (x86)\afick folder. On Linux, you will usually find the afick.conf file under /etc/ or /opt/afick/etc/. If you used the tar.gz archive, you can also use the included linux.conf file as a starting point. For an initial test run, leave the settings in the configuration file as they are.
Before AFICK can report changes, the tool needs to create checksums and store them in its database with the
afick.pl -c <configfile> -i
command. On Linux you have to introduce the command with sudo for root privileges (Figure 1). To run it under Windows, open a command prompt with administrator rights, switch to the AFICK folder, and call the above-mentioned command preceded with perl -w (which will be necessary for the rest of the AFICK commands in Windows):
cd C:\Program Files (x86)\afick perl -w afick.pl -c <configfile> -i
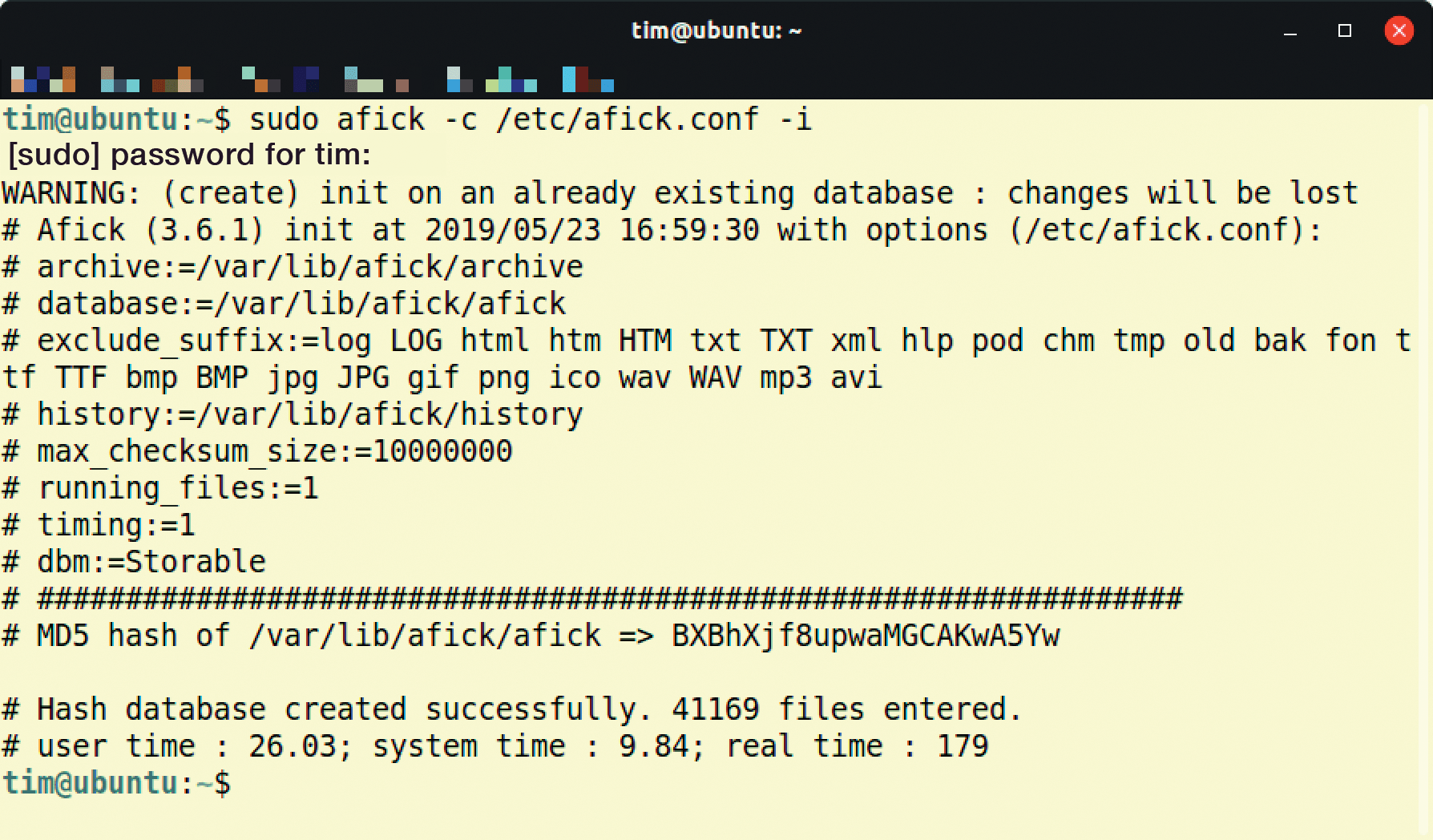
Throughout, replace <configfile> with the name of your configuration file (e.g., /etc/afick.conf or, on Windows, windows.conf). Administrator rights are needed because the configuration file always applies globally for the entire system. With corresponding settings in the configuration file, normal users can also run AFICK against their home or user directories.
Depending on your system, creating checksums can take several minutes. On Ubuntu 18.10, AFICK took about three minutes with the sample configuration on a test system that was no longer up to date. If you use the supplied configuration file, AFICK uses the MD5 checksums, which are no longer considered totally secure but can be generated more quickly. In the configuration file, however, you can switch to SHA1 or SHA256 (more on this later). In the end, AFICK outputs the message MD5 hash of and the storage location of the database. The code after the => is your MD5 checksum, which you can use at any time to check whether the file with the database has been manipulated.
Detecting Tampering
After the database is filled with checksums, use the following command to test your system for changes:
afick.pl -c <configfile> -k
Here, too, Linux users have to use sudo. The result is a list with all changed files and some statistics (Figure 2). Among other things, the statistics provide information about how many files AFICK has examined and how many new files have been added. Some system files and their checksums change, especially after system updates have been imported. In such situations, the command
afick.pl -c <configfile> -u
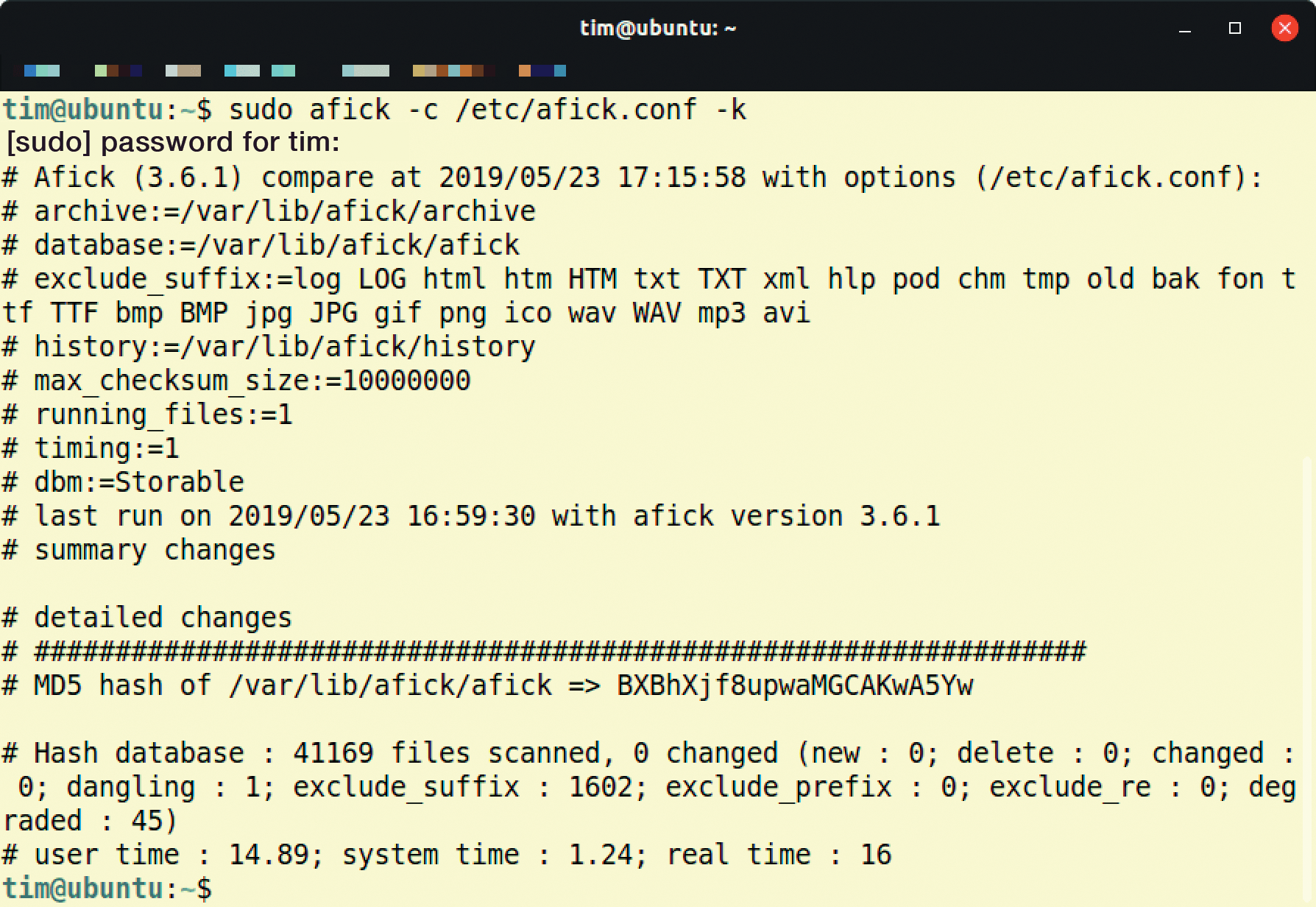
updates the AFICK database.
Regular Call
In the future, all you will need are the commands listed above, which you can also use to find out which files a system update or the installation of a new program has changed. To get a list of all files that change during an update or installation, first update the database, install the updates or the application, and then trigger:
afick.pl -c <configfile> -k
To track down unwanted changes, you will want to run the test regularly. Windows users should use the afick_planning.pl script included with the distribution. You do not have to register this script in the task scheduler; instead, leave this job to the afick_set_planning.pl script, which you run with:
perl -w afick_set_planning.pl
You will be prompted to select the start time in the user interface.
On Linux, you can use a cron job to call AFICK with the help of the afick_cron script. If you installed the application from a DEB or RPM package, your package manager has most likely already set up a suitable cron job. On Ubuntu, for example, afick_cron runs once a day. If you used the TGZ archive, you have to edit the settings in the cron file first:
-
AFICK=requires the complete path to theafick.plprogram. -
CONFFILE=expects the path to the configuration file. -
LOGDIR=defines the path where AFICK stores itsafick.logfile. All the output from the tool always end up there. -
ACTION=instructs the program to update its database (with-u) or perform a check (with-k).
Finally, you can check for duplicate files with the --duplicates option (Figure 3).
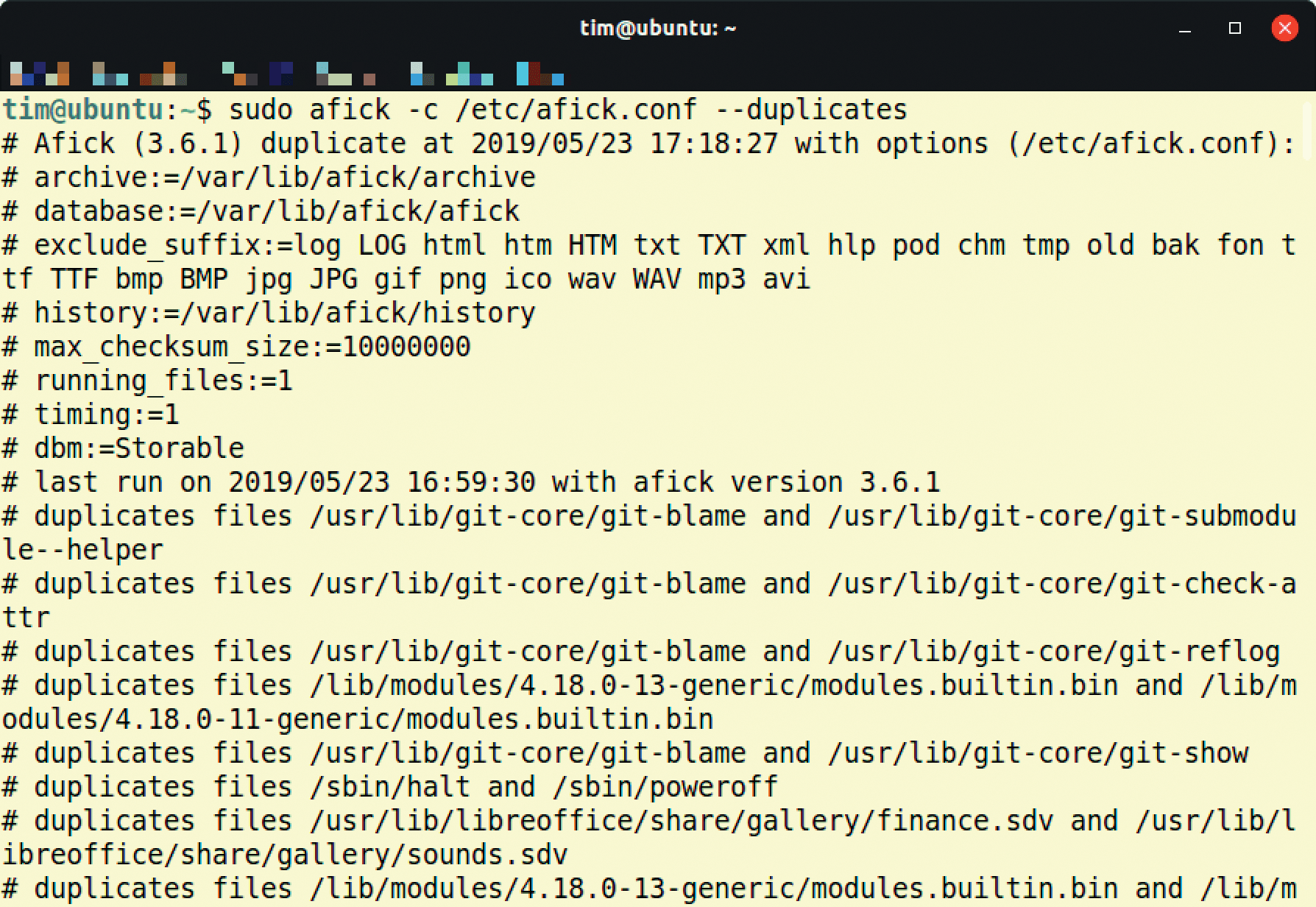
--duplicates option, the tool provides a list of all duplicate files on the hard drive.Refining the Basic Settings
The configuration file itself seems confusing at first glance. However, it follows a simple structure: Each line contains a setting with a keyword and the desired setting separated by a colon and equals sign (Figure 4). AFICK ignores all lines that start with a hash (#) sign, so you should remove the # prefix if you want AFICK to acknowledge the directive.
afick-gui user interface controls the afick.pl command-line tool in the background.A "directives" section at the very beginning of the configuration file defines a few basic settings, including the complete path to the location in which AFICK stores the contents of the database. AFICK also remembers the summaries of all the actions you have performed in a history; detailed reports of the actions end up in an archive.
You can usually leave the other settings in the top section as they are. For Linux users, however, the settings for symbolic links are still interesting: If you set warn_dead_symlinks:=true, AFICK informs you about all symbolic links that point to nothing; follow_symlinks:=no tells AFICK to follow the symbolic link and create a checksum for the file name of the file it finds. If you replace the no with yes, the tool generates a checksum for the file content.
Defining Exclusions
In the directives section, you'll also find several entries that begin exclude_suffix that instruct AFICK to ignore all files with the listed extensions. By default, these are files that change when you work with the system, such as text files or photos (e.g., txt, jpg). As in the .config file, you can create some order in your own exclusions by entering several exclude_suffix lines (e.g., to list all file extensions for text documents in one line and for photos in another). File extensions are simply separated by spaces. Because AFICK is case sensitive, you should always store your file extensions with different spellings (e.g., TXT txt for text files).
Similarly, AFICK can ignore files with names that begin with a specific abbreviation or term in a space-delimited list after exclude_prefix:=. Finally, you can also specify a regular expression, and AFICK then ignores all files that match the expression.
File Attributes
A file has metadata other than its size (e.g., the date of the last modification). In the configuration file, you specify which metadata you want AFICK to monitor for changes. However, it would be quite tedious to specify for each file which information is of interest. AFICK therefore saves you some work with the help of aliases. The tool assigns a letter to each file attribute. An explanation of the letter codes appear at the start of the alias section in the configuration file (Listing 1).
Listing 1: AFICK Aliases
############### # alias section ############### # action : a list of items to check # md5 : md5 checksum # sha1 : sha-1 checksum # sha256 : sha-256 checksum # sha512 : sha-512 checksum # d : device # i : inode # p : permissions # n : number of links # u : user # g : group # s : size # b : number of blocks # m : mtime # c : ctime # a : atime ** #all : p+d+i+n+u+g+s+b+m+c+md5 #R : p+d+i+n+u+g+s+m+c+md5 #L : p+d+i+n+u+g #P : p+n+u+g+s+md5 #E : '' (empty) ** # action alias may be configured with # your_alias = another_alias|item[+item][-item] # all is a pre-defined alias for all items except "a" DIR = p+i+n+u+g ETC = p+d+u+g+s+md5 Logs = p+n+u+g MyRule = p+d+n+u+g+s+b+md5 ##############
For example, if in a letters directory you have several files for which you want AFICK to monitor the file size and owner, you would first type the attribute abbreviations separated by plus signs and then tell AFICK which method to use to generate the checksums, again referring to the abbreviations at the beginning of the alias section. For example, md5 would apply the MD5 procedure, and sha1 would apply the SHA-1 procedure. Next, assign a name to this complete structure:
simple = s+u+md5
You don't have to specify a checksum; likewise, you don't have to apply AFICK to other file attributes like file size. However, the more features you include, the more likely the program is to detect tampering. From now on in the configuration file, you can simply tag all files from the letters directory with simple. AFICK then knows that it has to use the MD5 checksum for these files, paying attention to the file size and the user. You can tell the application what these files are in the file section that follows the alias section.
Directory-Wide Inspection
In principle, you can use the file section to specify in each line the path to a file that you want AFICK to check. After the file, note the appropriate alias. In this example, it might be:
/documents/letters/taxoffice.txt simple
In this case, AFICK would inspect the taxoffice.txt file under the conditions set by the simple alias. If you want this to happen for all letters in the letters directory, you would simply enter:
/documents/letters simple
On Windows, use the standard Windows notation with backslashes. If you want AFICK to ignore a file in the letters folder, write its file name in a new line and prefix its name with an exclamation mark. In the following example, the tool would consider all files from the folder letters, but not the files draft.txt and ideas.txt:
/documents/letters simple ! /documents/letters/draft.txt ! /documents/letters/ideas.txt
If you specify a directory, AFICK automatically digs down into the subdirectories. If you want to prevent this, add an equals sign to the corresponding line followed by a space:
= /documents/letters simple
Further examples can be found in the configuration file that comes with the AFICK bundle. Choosing the right settings requires some experience. Therefore, you will want to start with the settings in the sample configuration file and then adjust them to suit your needs. Always check the changes to the configuration file for errors with the command:
afick.pl -c <configfile> --check_config
The complete documentation of the configuration file is available online [3]. The meaning of the individual lines is also explained by the many comments within the file.
User Interface
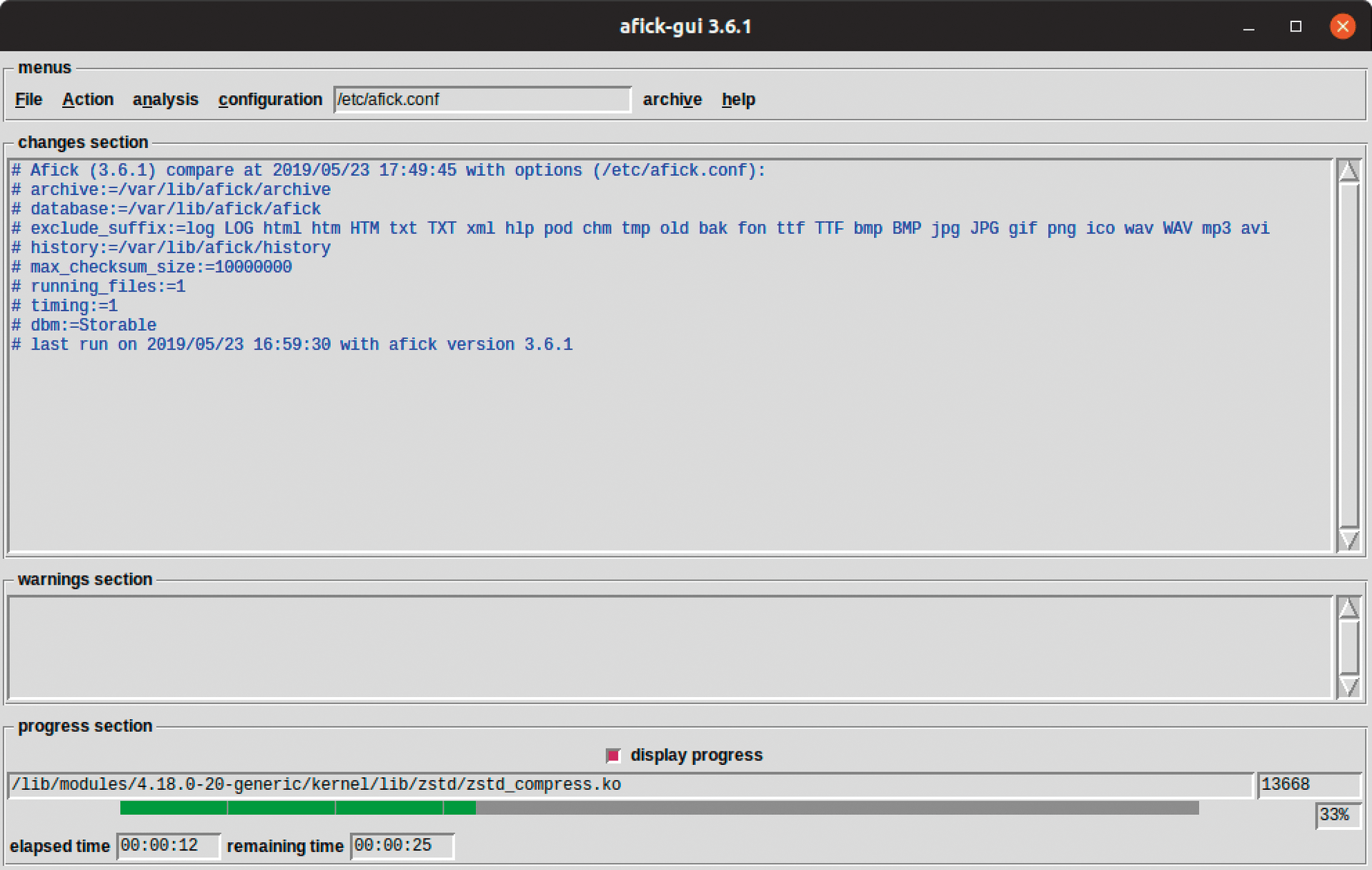
AFICK includes a graphical user interface for Linux that uses the Tk toolkit. If you used the RPM or DEB package, you will need to install the front end. From the AFICK download page, get the DEB or RPM package that starts with afick-gui, and install it as you did the AFICK package. The afick-tk.pl script starts the front end. On Windows, try the corresponding entry in the start menu. Depending on the configuration, you might also have to open the user interface with administrator rights.
If necessary, first load your configuration file with Configuration | Select. The file name now appears in the input field on the right. Action | Init recreates the database with the checksums. If you see an error message telling you that the database is already locked, it is very likely that appropriate access rights are missing. In this case, run afick-tk.pl as administrator.
Action | Update updates the database, and Action | Compare triggers a check. The pane called changes section at the top always groups the output from AFICK, and the warnings section at the bottom has all the error messages. You can follow the progress and the time AFICK needs to complete the action at the bottom of the page.
If AFICK finds a large number of changed files, the output becomes quite confusing. Calling up a tree view under the Analysis menu displays all the files in question in a more comprehensible way. Clicking on a file in the tree unfolds further information to the right. From the Analysis menu you can also call up various statistics and information. For example, Analysis | Duplicates returns all files stored multiple times on the hard disk. To view the history, select File | History. Clicking on an entry restores all its messages in the main window.
Conclusions
AFICK is not only quick to install, it is reasonably fast. A short command or a couple of clicks in the user interface are all it takes to check the system – assuming you have a workable configuration file, which takes more than just a few minutes to put together. Additionally, AFICK requires Perl and normally runs on the system it is supposed to monitor. With these limitations, AFICK cannot claim to be a full-fledged intrusion detection system, but it is nevertheless a useful component in a holistic security strategy.
