
Guarding against social engineering attacks
Persuasion
A piece of news piqued my interest the other day. The security suite BackBox Linux had become available on Amazon Web Services (AWS) as a Amazon machine image (AMI). One link led to another, and on my expedition, I became entangled with one of its many excellent security tools. Specifically, one that focuses on "human hacking," otherwise known as social engineering. Some claim [1] that social engineering is the biggest threat to business, so staff training is of paramount importance.
Before delving into social engineering, however, I'll look a little more closely at BackBox Linux [2]. As you'd expect from the name, it's open source and describes itself as being "more than an operating system, it is a Free Open Source Community Project with the aim of promoting the culture of security."
Bundled with lots of penetration testing and security assessment tools and built on an Ubuntu core, BackBox Linux offers the ability to investigate a wide range of cybersecurity issues, ranging "from web application analysis to network analysis, stress tests, sniffing, vulnerability assessment, computer forensic analysis, automotive and exploitation."
In this article, I look at BackBox Linux and what is necessary to run it as an AMI on AWS Marketplace. After a quick look over some of its tools, I'll dig deeper into the Social-Engineer Toolkit that BackBox carries in its arsenal.
Get Back
As you might guess, BackBox Linux simply contains too many tools to examine at any great level of detail. Certainly, it's a mature security toolkit that first appeared as a September 2010 release candidate. At the time of writing, the current version was 5.3, so you might see options or menus different from those I discuss here if you work on a different version.
BackBox Linux includes the familiar and slick Xfce desktop manager [3], which makes accessing all of your preferred tools easy. BackBox also promises a number of performance tweaks to boost its boot time and a sprinkling of configurations that help maintain its minimal footprint. If you're interested in contributing, the developers will accept custom packages in the form of a Personal Package Archive (PPA) [4] to be offered on Launchpad. To get started, download BackBox Linux [5] (i386 or amd64) and install it locally.
To access the AWS version of BackBox Linux, the team asks you to pre-register as a member for a very reasonable membership fee or submit a request for the service [6]. The idea is that professional penetration testers are the most likely people to want AWS access to a cloud installation. At the time of writing, a one-year membership was EUR10 and EUR5 per year thereafter.
Alongside many options (e.g., news feeds and the latest exploits), you'll find a comprehensive website [7] with a forum, blog, and Telegram group. You should check out the BackBox website to increase your knowledge of the penetration testing space.
Getting Your Hands Dirty
I decided to try BackBox Linux on VirtualBox, so on the download page, I selected ISO and chose a mirror (Figure 1). Although it's important to donate to projects like BackBox Linux, if you can't then entering a 0 in the donation field will still allow you to download the ISO. Once downloaded, your disk space will be 2.2GB lighter.
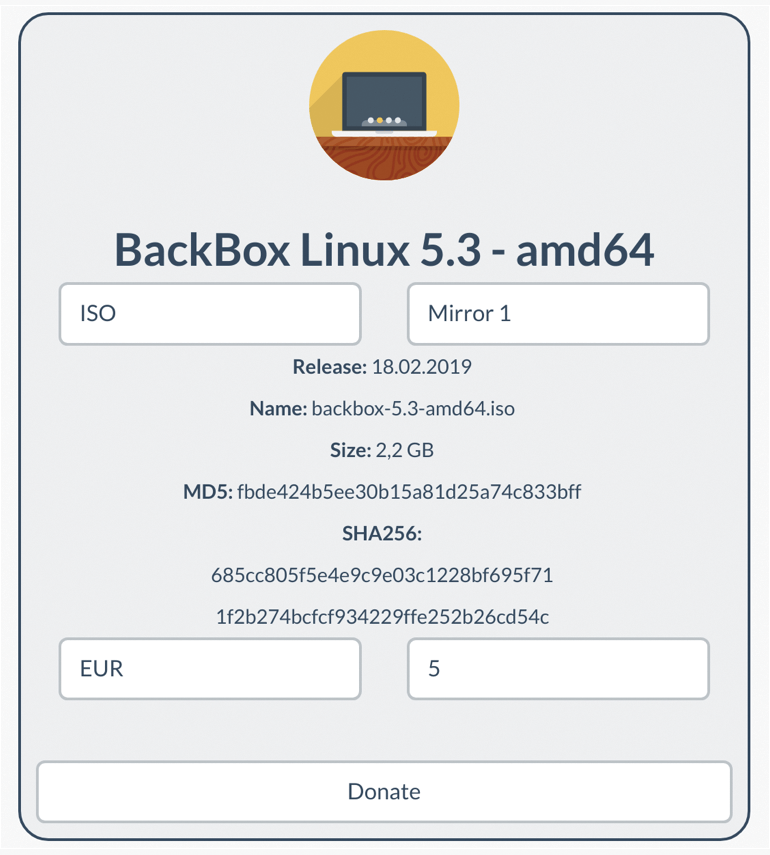
Be sure to check the hash reported by your SHA256 checksum tool with the listed checksum to verify that you have indeed downloaded the correct file and it has not been tampered with en route:
$ sha256sum backbox-5.3-amd64.iso 685cc805f5e4e9c9e03c1228bf695f711f2b274bcfcf934229ffe252b26cd54cbackbox-5.3-amd64.iso
The checksum in Figure 1 matches my download, so all is well.
UEFI Secure Boot
Because I chose to use VirtualBox on a laptop (Linux Mint Ubuntu 16.04 derivative) with UEFI, I had to install a new Machine Owner Key (MOK) after a reboot. To do this, I set a password for the VirtualBox package at installation and then choose the install a key from disk or similar option at boot.
If you're unfamiliar with this process in VirtualBox, or something does go horribly wrong (your machine will still boot happily if this bit messes up), a blog post by ÿyvind Stegard should help you get on track [8]. Thankfully I hadn't forgotten the UEFI password, and the software behaved perfectly. It installed the MOK without any issues and booted up fine.
If, like me, you're installing VirtualBox on a Debian derivative, I installed the following packages:
libgsoap-2.8.60libvncserver1virtualboxvirtualbox-dkmslibqt5opengl5libqt5printsupport5virtualbox-qt
To prevent system bloat, I generally keep note of any packages I install, so I can clean up after myself when I'm finished with a project.
Not the Sharpest Tool
Other than the usual suspects in the topmost Favorites menu item (e.g., web browser, shell, text editor, GUI file manager), BackBox Linux includes a handful of security tools, such as Ettercap (for man-in-the-middle network attacks, among other things), the msfconsole interface to the all-powerful Metasploit Framework (for pen testing), Wireshark (for sniffing network connections), the venerable ZAP (automated security testing) [9], and Zenmap (a graphical front end to the prodigious and unmatched Nmap security tool).
A click on the Auditing link in the right-hand menu presents a carefully compiled list of security areas on which you might focus (Figure 2). Choosing any topic reveals their many associated submenus.
![The Auditing option offers a number of interesting areas to explore. Source: BackBox Linux [2]. The Auditing option offers a number of interesting areas to explore. Source: BackBox Linux [2].](images/F02.png)
My Privacy Is Private
The Anonymous menu option presents a group of three that addresses privacy: anonymous start, anonymous status, and anonymous stop. Clicking anonymous start presents a pop-up terminal informing you that a simple script will attempt to stop common information leaks from your system. It also advises where to configure the relevant values (the config file is located at /etc/default/backbox-anonymous). As you might guess, it offers a friendly warning that what you do with your computer determines how much information is ultimately leaked to the outside world.
The simple anonymity script uses Tor to protect your privacy, including which DNS ports you'd like to use, the local IP address ranges you'd like to prevent being routed out via Tor, and processes that might reveal information you don't want shared that you'd like to have stopped dead in their tracks. BackBox can even instruct BleachBit precisely what to tidy up after you've stopped running the anonymity script (e.g., system cruft and file history).
Antisocial Behavior
As I mentioned in the introduction, one of the most successful types of attacks that has been present since time immemorial – way before computers were around – is simply tricking people to reveal something they probably shouldn't.
I'm referring to social engineering, which is considered one of the biggest threats to security in modern times. The premise of social engineering is simple and yet still massively successful: persuade or trick individuals into revealing information that attackers can use to their advantage.
That information might be a password but could be all sorts of other types of information, like the time of day for shift changes or the type of tool used to perform a certain task. In fact, the possibilities are so broad that the venerable Social Engineering Framework (SEF) website [10], which provides the Security Engineer Toolkit (SET) that I'll look at shortly, calls such activities a "blend of science, psychology, and art." I think that sums up cybersecurity as a discipline pretty well, too! If you're interested in this area, a friend directed me to a fascinating article online [11] for more insight.
The SEF website further defines social engineering as "any act that influences a person to take an action that may or may not be in their best interests." Figure 3, from the SEF website, lists the different attacks more succinctly. Another categorization [12] lists six principles used to take advantage of someone's good nature and their perfectly normal desire to return a favor.
![Categories of social engineering. Source: SEF website [13]. Categories of social engineering. Source: SEF website [13].](images/F03.png)
For social engineering attacks in this article, I focus on the SET toolbox previously mentioned earlier. According to the SEF website, SET was created by David Kennedy (ReL1K), with input from the open source community. The SEF website describes SET as a toolkit specifically focused on performing advanced attacks against the "human element" during a penetration test.
Under the menus on BackBox Linux, you can run setoolkit from the Auditing | Social Engineering option. You're presented with a gentle reminder that you should be giving the author a hug, or a bourbon, or indeed a beer for his sterling efforts. Another nice reminder encourages you to improve the industry for all involved by helping out where possible.
Finally, a warning reminds you to do good and not evil. Consider yourself suitably warned that all BackBox Linux tools, including SET, should be used on systems, people, or networks on which you have permission to run them.
After agreeing with the terms, you are offered a nice, clean ASCII menu within a terminal window that lets you know the latest version of SET available and the one you're currently running (Figure 4). It also points you at the GitHub page [14] for more information.
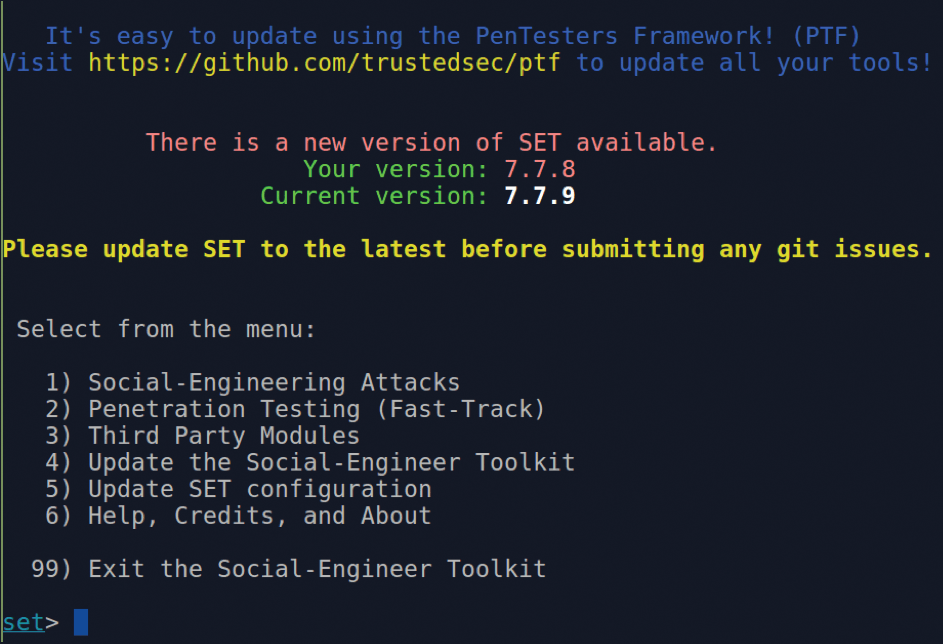
The GitHub page is also very helpful if you're not using BackBox Linux to run SET, offering the various dependencies required for different operating system (OS) flavors (e.g., Debian derivatives like Ubuntu and Mint, etc.). To install the dependencies yourself, you would enter:
$ apt install -y git apache2 python-requests libapache2-mod-php python-pymssql build-essential python-pexpect python-pefile python-crypto python-openssl
The GitHub README file has a link to a PDF that acts as a nicely written and relatively easy-to-follow tutorial and manual.
Man, Well
In the user manual, the author talks about the rationale behind not using command-line options but instead presenting the user with a menu-driven set of options: "The decision not to make it command line was made because of how social-engineer attacks occur; it requires multiple scenarios, options, and customizations. If the tool had been command-line based it would have really limited the effectiveness of the attacks and the inability to fully customize it based on your target."
The manual I downloaded refers to an earlier version, but it's easy to grasp any subtle menu differences in the menu options. After you've moved around the menu and submenus for a while, you'll see a heap of clever ASCII art. The menu in Figure 5 was presented on my current version when I chose the Social-Engineering Attacks option.
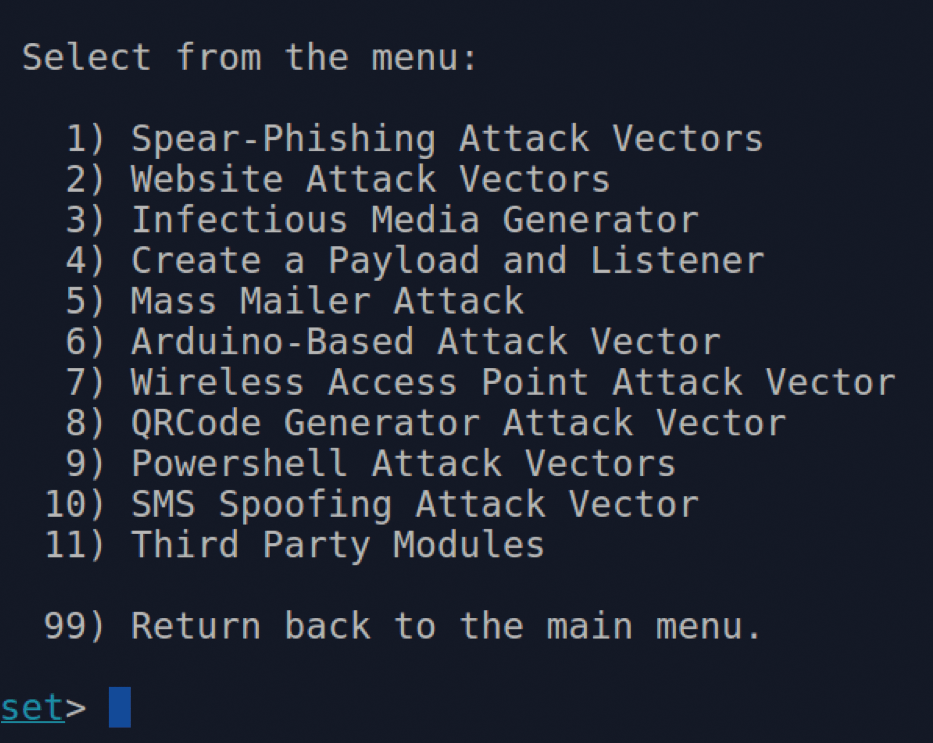
At the risk of not doing SET the justice it deserves, I'll quickly look at what some of the options might do in the hope that you'll explore the others yourself in the future.
Teach a Man to Fish
From option 1 on the menu shown in Figure 5, you enter the Spear-Phishing Attack Vectors submenu. The prompt then changes from set> to set:phishing>, offering just enough information to know where you are and what you are doing. Figure 6 shows the spear phishing choices.
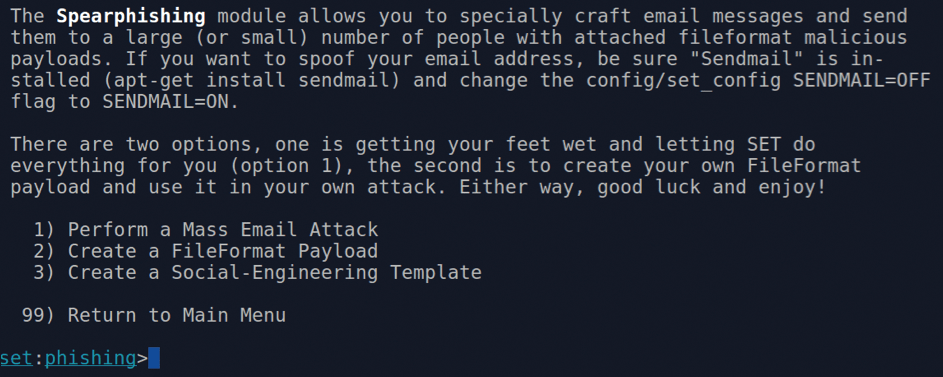
If you follow option 1 and let SET do all the heavy lifting, you're presented with the payload options shown in Figure 7. As you can see, you have a great deal of choice across a number of formats.
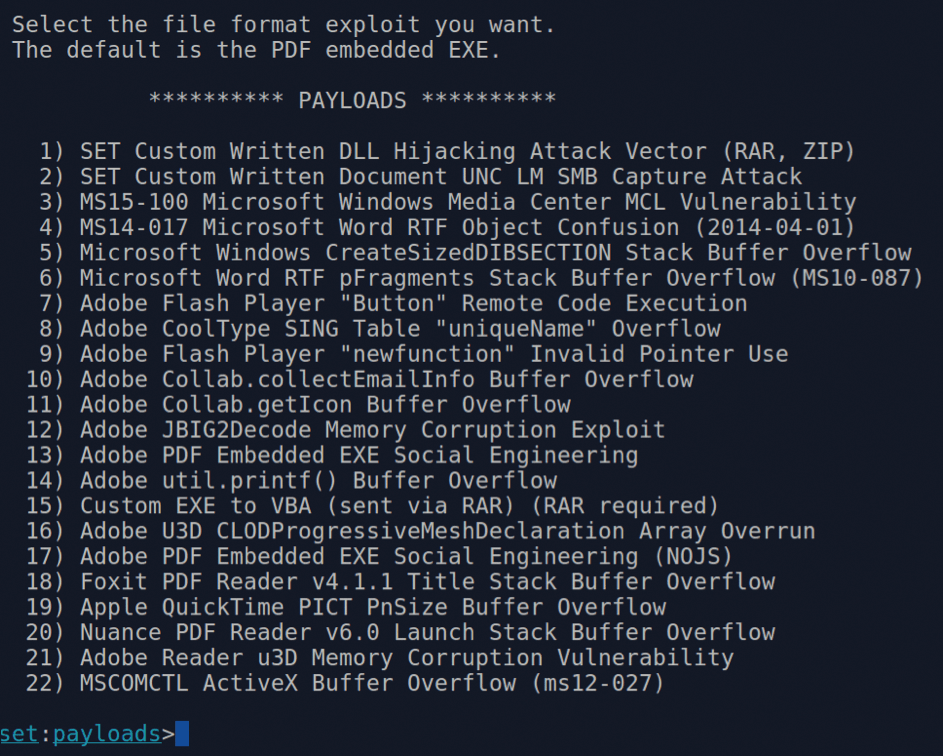
In an effort to encourage you to try SET yourself, I leave it to you to drill further down into the other options – for testing purposes only, of course.
More, More, More
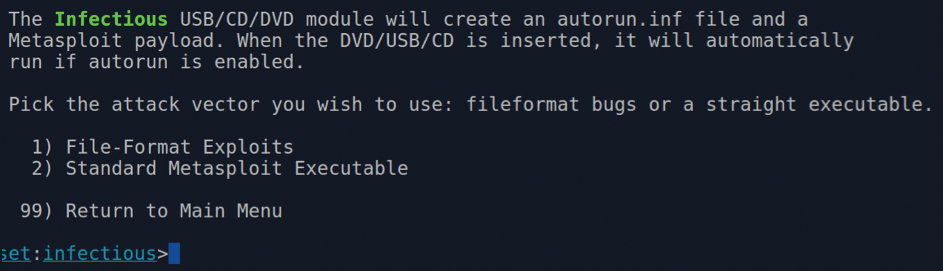
The Infectious Media Generator social engineering attack immediately presents some useful information (Figure 8). As you can see, all types of popular media (USB sticks/drives, CDs, and DVDs) are the targets in question. An autorun.inf file is used for this particular attack, in which a payload is created on request in one of two formats. Note that the prompt has dropped into the informative set:infectious> mode.
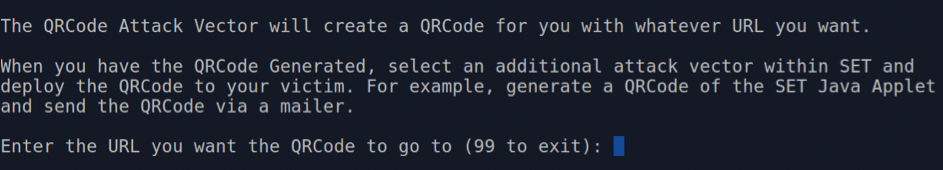
Option 8 of Figure 5 presents a QRCode generator (Figure 9) that lets you craft a URL to embed into a QRCode, which could be something as nefarious as a Java applet that's then sent out by email.
From the uppermost level of Figure 4, I'll move on to Penetration Testing (Fast-Track). Those of you familiar with penetration testing will have heard of Fast-Track, which I was sad to see didn't seem to have a live website any longer. As you can see in Figure 10, the options it brings to the table to complement SET are comprehensive and useful for security auditing.
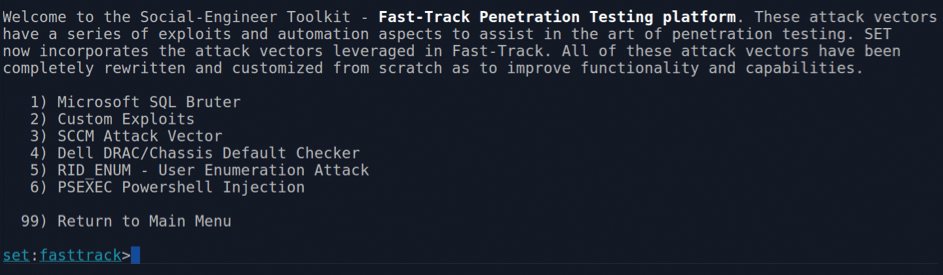
From customized exploits through SQL brute-forcing, you'll find a number of interesting options worth exploring.
By now you should be able to tell I'm a big fan of SET. Hunting through some of the more obscure options, I even found an attack on Google Analytics, seemingly with a fully fledged user manual included. In Figure 11, you can see what's available from this submenu option (hidden under the Third Party Modules option).
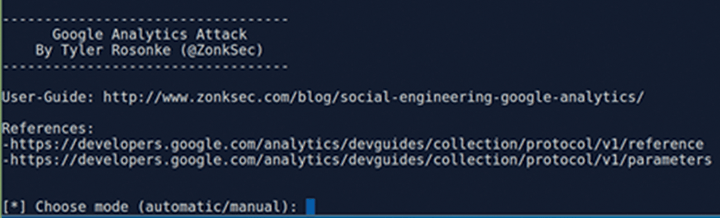
It Ends Here
The Social-Engineer Toolkit has simply too many facets to cover here. If you keep rummaging, you'll find WiFi tools for wireless monitoring, testing, cracking, and attacking, and I haven't even mentioned the menu options provided to update the SET software directly.
The long list of included tools and options is impressive and varied in both BackBox Linux and SET, so I'd fully encourage you to investigate both for yourself.
For SET, in particular, especially if you're new to social engineering, I would recommend reading through some of the comprehensive website content provided by SEF, which includes podcasts, a blog, book recommendations, and notifications about events, among other guidance. A list of example attacks [15] got me thinking about the effectiveness of social engineering.
Consider for a moment a real-life occurrence of one of the examples [16] listed on that page: "A phishing attack in January 2016 gave hackers illegal access to the Department of Interior network through remote logins on at least eight Gmail accounts, according to a report released May 24 by the Office of the Investigator General at DOI."
Undoubtedly, tools like SET and toolkits like BackBox Linux are invaluable to protect innocent users against such potentially devastating attacks, and I hope you'll enjoy learning more about them as much as I have.
