
Monitoring IPv6 with Wireshark
New Dust with Old Brooms
Sys admins around the world use the free network protocol analyzer Wireshark to monitor traffic and troubleshoot problems on TCP/IP networks. If you're wondering whether you'll still be able to use Wireshark in the IPv6 era, the answer is yes, but you'll need to be aware of some important differences between the IPv4 and IPv6 protocols. This article begins with some background on IPv6 and shows you how to get started with using Wireshark to monitor IPv6 communications.
About IPv6
Like an IPv4 address, an IPv6 address consists of two parts: The left side represents the network identifier, and the right side represents the host ID. The default prefix is /64 and divides the IP address into two halves, the routing area and the interface address (64 bits each). An IPv6 address consists of 128 bits and is usually expressed as eights sets of four hexadecimal digits (known as nibbles, quibbles, or hextets) separated by colons. For example, an IPv6 address looks like this: 2001: 0db8: 1010: 61ab: f005: ba11: 00da: 11a5 / 64.
In Europe, providers obtain IPv6 addresses through the Réseaux IP Européens Network Coordination Centre (RIPE-NCC) and then pass them on to users. A user who receives an IPv6 address is not actually the owner of the address. Instead, the user enters into a user agreement. All allocations are subject to the allocation guidelines.
IPv6 Address Types
IPv6 distinguishes between unicast, multicast, and anycast addresses. A unicast address represents a single host; each interface of the host can have more than one unicast address. Hosts are usually assigned two types of IPv6 unicast addresses: link local and global unicast addresses.
A link local address is similar to the private address in the IPv4 world and is used for communication on the local network (for example, with other hosts or routers connected to the network). These addresses are not routable and each network interface has only one link local address. You can recognize these addresses by the network identifier FE80:: /10 (but the host identifier actually starts after the 64 bits). Once IPv6 is enabled on a network interface, it generates a link local address. The link local address can be defined in any of the following ways:
- Manual: The address is configured manually on the host.
- Modified IEEE EUI-64 format (according to RFC 4291): The host ID is derived from the MAC address of the network interface.
- Privacy Format (according to RFC 4941): The host ID is based on a random number.
After a network interface receives a link local address, it sends a multicast message to all hosts on the local network. Using Duplicate Address Detection (DAD), the interface ensures that no other host with the same address is active on the local network.
Communication via Neighbor Discovery Protocol
The Neighbor Discovery Protocol (NDP) is an additional protocol defined in RFC 4861 and is the equivalent of the Address Resolution Protocol (ARP) of IPv4. NDP enables the IPv6 interface to detect and communicate with neighboring computers and routers. NDP defines the following Internet Control Message Protocol (ICMP) messages:
- Neighbor Solicitation (NS): A host sends these messages via multicast when searching for a link local address or when confirming that the generated link local address has not been assigned to another host (DAD). NS messages show the ICMP value
135. - Neighbor Advertisement (NA): A host reacts to a NS message. This message is similar to the ARP response in IPv4. NA messages have an ICMP value of
136. - Router Solicitation (RS): A host sends this message via multicast to automatically detect the routers available in the local network. RS messages have the ICMP value
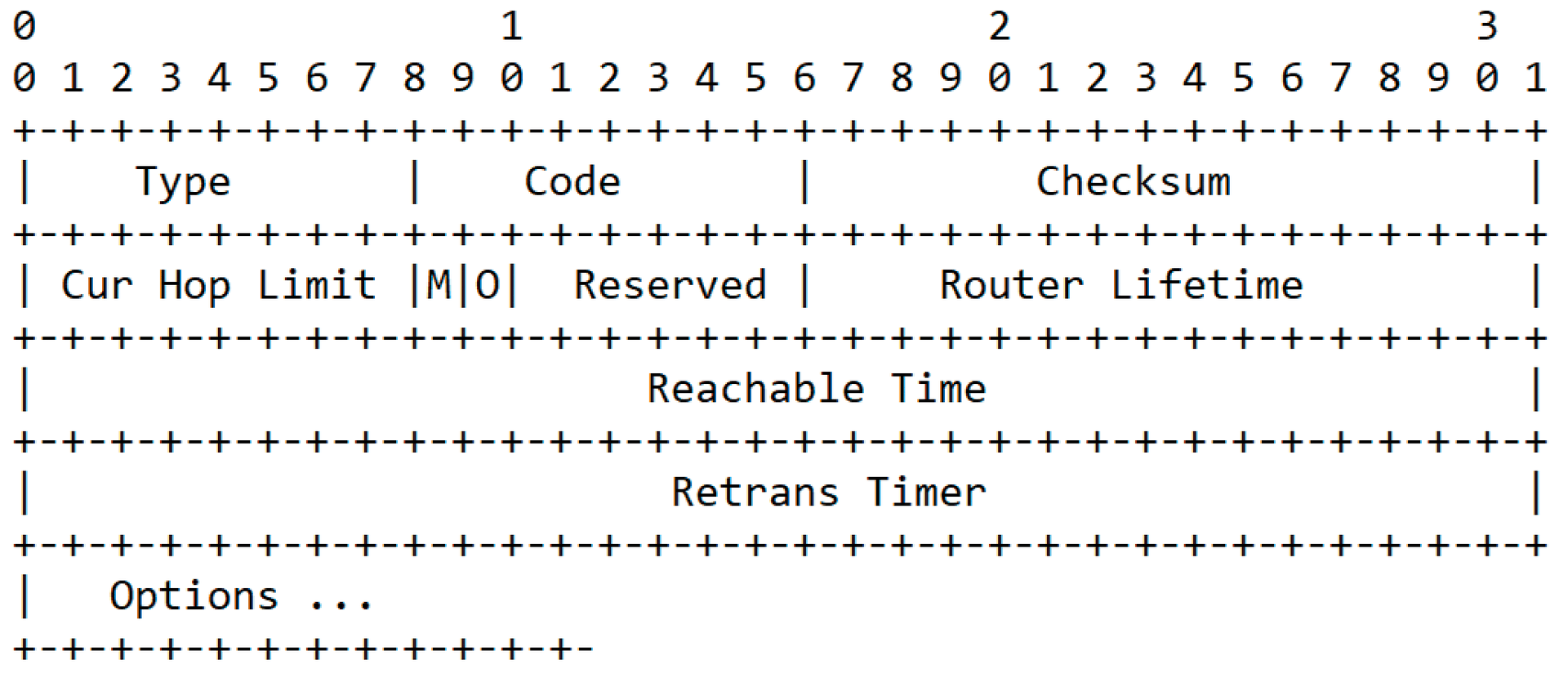
133. - Router Advertisement (RA): With the help of RA messages, a router identifies itself to all hosts in the network and simultaneously transmits the necessary network information to all hosts (Figure 1). RA messages have an ICMP value of
134.
For more on ICMP values, see the box entitled "ICMP in IPv6."
RA lets routers announce their presence on the network. Messages are sent either on request via RS or periodically (to avoid being forgotten). The hop limit is an 8-bit value that transmits the standard hop limits suggested by the router. The flags contained in the RA messages define the automatic address configuration method:
- A set M bit tells the node to use stateful autoconfiguration in addition to autoconfiguration for the IP address.
- A set O bit tells the node that it can use stateful autoconfiguration in addition to autoconfiguration for all non-IP address information.
- A set HA bit indicates whether a home agent is active for mobile accessibility.
- The Pref bit can be used to set the preferences for several routers on the network.
- Proxy bits indicate whether a proxy is being used.
The router lifetime is a 16-bit integer value that specifies how many seconds a router should remain in the default router list. The theoretical maximum is just over 18 hours (65,536 seconds), but RFC 4861 limits the maximum to 9,000 seconds (2.5 hours). A value of 0 means that the router is not a default router and should not be entered in the default router list.
The router lifetime is a 32-bit integer value that specifies how many milliseconds an entry in the Neighbor cache should still be considered reachable after receiving data. And the Reachable Time specifies the number of milliseconds after which a new NS message should be sent.
Communicating with the Rest of the World
A Global Unicast Address (GUA) corresponds to a public address in the IPv4 world. Such an address is routable, accessible from outside the local network, and rarely used for communication within a network. A host can have up to six different GUAs on the same network and an almost infinite number of GUAs on different networks. A GUA covers the address range from 2000:: /3 to 3FFE:: /3.
A GUA can be activated using one of the following address configuration methods:
- Manual: An IPv6 address is manually assigned on the host.
- Stateless Address Auto Configuration (SLAAC): The host takes the network prefix from the RA message and then creates two GUAs with two different host IDs.
- Stateless Dynamic Host Configuration Protocol (DHCPv6): Like SLAAC, but the host receives additional information (such as DNS and NTP) from a DHCPv6 server.
- Stateful DHCPv6: The RA message does not contain a corresponding prefix. For this reason, the host sends a request to detect a DHCPv6 server and prompts the recipients to submit appropriate GUA addresses and configurations.
- Combination: A host receives the GUA addresses using SLAAC and Stateful DHCPv6 methods. This can cause the host to receive too many IP addresses.
To achieve an IPv6 address mindset, IT managers need to free themselves from all IPv4 ballast and strictly follow the IPv6 rules.
Stateless Allocation of IPv6 Addresses
In contrast to the IPv4 protocol, where all address configurations are carried out manually or semi-automatically via DHCP, IPv6 attaches particular importance to automatic configuration of the networks. Automatic configuration can be either stateful or stateless.
Each node on the IPv6 network can discover the necessary configuration parameters of the network interfaces from a router installed on the same network. The routers send the RA messages to the network cyclically (normally every 600 seconds) or on request. RA messages carry the information required for independent computer (end node) configuration.
If a router sends an RA message to the network after an internal timer has expired, the multicast address FF02::1 (all nodes multicast address) is always used as the target address. This approach ensures that all network nodes automatically receive this information. When router discovery messages are transmitted, a value of 1 is entered in the hop limit field of the IP header. This prevents this message from being transmitted to other networks via routers.
The M bit (Managed Address Configuration Flag) indicates the type of address configuration. A value of 1 means that stateful address configuration (via DHCP) is used. A value of 0 in the M bit indicates stateless address configuration. If the O flag has a value of 1, the router is saying that, although the IP address can be automatically and statelessly created from the ICMP packet with the prefix, the terminal device must obtain additional information via DHCP. And by setting a 1 in the H bit, the router indicates that it can also act as a home agent for mobile IPv6 nodes.
The lifetime is the validity period of the information transmitted by the router and is specified in seconds. The 16-bit integer value thus enables a maximum validity of 18.2 hours. A default router is only a default router if it has a lifetime value. If the lifetime value is 0, the information from the packet can be used, but the router cannot act as a default router for other networks. If the validity period expires without a new ICMP packet being received from this router, the computer has to remove the router from its routing table.
The Reachable Time (in milliseconds) indicates how long a computer is considered reachable after an availability message has been received. This value is used by the Neighbor Unreachability Detection algorithm. The Retransmit Timer specifies how many milliseconds a computer should wait after a NS message before sending it again. This value is also required by the Neighbor Unreachability detection algorithm.
The packet can contain additional options, such as values for the MTU, the hardware address of the router, or possible prefixes for stateless autoconfiguration.
RS messages are sent by machines that configure a new interface and do not want to wait for automatic announcements. The computer then asks the router to immediately send a response packet. Explicit requests are always sent to the link local address of the requesting node. If a terminal device now wants to construct its own IP address from the information in the router messages, it must proceed as follows:
- If a device receives RA messages on one of the interfaces that contain a suitable prefix, the interface can form its IP address by combining the prefix with the local hardware address.
- Since the prefix supplied by the router is unique on the Internet and the local hardware address on the LAN is considered unique, the two parts always result in a unique IP address.
- Even if no router propagates a suitable prefix, a computer can always generate a unique IP address. In this case, the prefix FE80:: in conjunction with the hardware address describes a unique IPv6 address for the local network (link local).
One advantage of this method is that smaller networks can be put into operation without any previous planning overhead. However, activating DAD is a prerequisite for the correct function of stateless addressing. The task of this function is to detect or prevent duplicate addresses. DAD must therefore be performed by each device after selecting an address. During autoconfiguration, a device may only select addresses that have not yet been assigned.
For larger networks, however, there is still a lack of well-founded practical experience regarding the use of stateless IPv6 addresses. Also, nothing is currently known about the quality of the implementations of the address discovery and DAD functions. In addition, dynamic allocation of IPv6 addresses makes the task of documenting the networks, the computers connected to them, and their specific configurations considerably more difficult. This results in increased overhead for troubleshooting. And in the case of autoconfiguration of stateless addresses, the terminal devices assign themselves addresses for which no records are kept. Since autoconfiguration does not consider information relating to hosts, domain names, DNS, or NTP servers, it can or must be supplemented by the use of a DHCPv6 server.
Stateful Address Assignment and DHCPv6
The stateful autoconfiguration model is based on the fact that the computer downloads addresses and, if required, other configurations and parameters from a server set up on the network. The administrator stores and maintains the configuration data on this server. With the help of a stateful autoconfiguration protocol, the computer downloads its IP addresses and other configuration parameters via the network. This form of autoconfiguration is always used when the network operator needs an exact assignment of addresses to interfaces.
DHCPv6 is the stateful autoconfiguration protocol. DHCPv6 is based on the basic specifications defined in RFC 1541 for use with IPv4 computers. For IPv6 networks, the DHCP protocol was extended to cover the special requirements and a multitude of additional functions were added. The DHCP protocol gives a network administrator the ability to centrally manage and maintain all TCP/IP configuration parameters. So DHCP is an approach to building a plug-and-play TCP/IP network.
The advantage of this approach lies in the experience that IT managers have with DHCP, which has been deployed in production operations with IPv4 for years.
Logging IPv6 Traffic with Wireshark
If you have some familiarity with Wireshark, you'll recognize the following features of the Wireshark GUI:
- Packet list: Displays each packet in a single line and some identification parameters (for example, target IP address and protocol).
- Packet details: Log details for the selected packet.
- Packet bytes: The raw bytes of the marked packet.
The IPv6 traffic on the local network can be visualized with the following simple steps: First determine the default gateway address using ipconfig. Make a note of this address and start Wireshark logging now. Pinging the default gateway address gives you the IPv6 address of the default gateway. Then stop Wireshark logging and analyze the outgoing and incoming packets.
Outgoing IPv6 Traffic
The outgoing IPv6 traffic on the local network is visualized as follows: The upper part of the Wireshark packet list shows the logged packets. For example, if you are only looking for ICMPv6 traffic, you need to suppress any other IPv6 traffic. To display only ICMPv6 traffic, type icmpv6 (in lower case) in the filter field. Then select the first ICMPv6 packet or scroll down to find the first packet tagged Echo (Ping) Request. When you select this packet, Wireshark displays the specifics of the packet in the packet details. The packet is usually an IPv6 packet for Ethernet v2. This Ethernet packet contains IPv6 on layer 2 and the ICMPv6 based on it.
Click on the Ethernet II tab to display the Ethernet details. In this case, the destination address in the Ethernet packet should match the MAC address of the default gateway. The sender address in the Ethernet packet should contain the MAC address of the sender of the ping message. The type field in the Ethernet packet contains the value 0x86dd. This value specifies that the following packet is an IPv6 datagram.
Click on the Internet Protocol Version tab to access the IPv6 details. The sender address in the IPv6 datagram should contain the IPv6 address of the ping message's sender, and the target address in the IPv6 datagram should match the IPv6 address of the default gateway.
Incoming IPv6 Traffic
The following steps are very similar to those for outgoing traffic analysis but differ in important details. You can analyze incoming IPv6 traffic on the LAN by first selecting the next ICMPv6 packet tagged Echo (ping) Reply from the Wireshark packet list. When you select this packet, the packet details provide the specifics of the packet. In this case also, the packet is usually an IPv6 packet for Ethernet v2 and here, too, the Ethernet packet of layer 2 contains IPv6 and ICMPv6 based on it.
Now click on the Ethernet II tab to display the Ethernet details. The target address in the Ethernet packet should contain the MAC address of the ping message's recipient. And the sender address in the Ethernet packet should match the MAC address of the default gateway. Also, in this case, the type field in the Ethernet packet returns the value 0x86dd. This value tells us that the subsequent packet is an IPv6 datagram.
A click on the Internet Protocol Version tab reveals the IPv6 details. In this case, the sender address in the IPv6 datagram should match the IPv6 address of the default gateway and the destination address in the IPv6 datagram should contain the IPv6 address of the ping message's recipient.
You can either quit the analysis and discard the recorded data or save the data in a file.
Display Filter
If you are only interested in a subset of the captured packets (Figure 2), you can display them using a display filter (Figure 3). To use a display filter, define a filter expression in the filter bar. Such a filter expression can have the following format:
- Protocol: IPv6
- Attribute == Value: For example,
ipv6.src == fe80::f957:3844:95e5:9d17. - Complex: Combinations of two or more expressions with the help of "and" (
&&) or "or" (||).
Alternatively, select arbitrary packet parameters with the right mouse button and then select Apply as filter. After that, Wireshark only displays the packets that have the same value for the parameters you specify. You can save the filters you set by pressing the button next to the filter bar.
Only Certain Parameters Are of Interest
In packet analysis, the IT manager is typically only interested in specific parameters. Instead of going through the details of each packet and checking each of these parameters in all packets, Wireshark lets you display these parameters as columns in the Packet List section. All you need to do is right-click on a parameter in the Packet Details window and select Apply as Column. This option can be useful, for example, when analyzing RA packets. The four flags M, O, L and A can be clearly displayed as columns.
Wireshark offers the possibility to color-highlight the different protocols. Use the Coloring Rule menu, which you can access via the Customize Colors option in the View menu. In the configuration profiles, user-defined configurations (e.g., the saved display filters and color schemes) can be stored. You can save the various profiles via the Configuration Profiles menu, which you can access via the Edit menu. Switch between the profiles in the status bar by clicking on Profile.
Sometimes it is helpful to add comments to packets during packet analysis. A comment lets you share additional information with another user who is viewing the PCAP file. Add a comment by right-clicking on a packet and selecting the Comment Packet option.
Conclusions
Once you have gotten used to the syntax and command set, Wireshark is an incredibly flexible and useful tool for IPv6. It helps administrators troubleshoot and analyze problems on the IPv6 network. Armed with some knowledge of the peculiarities of IPv6, you can use Wireshark to monitor traffic and troubleshoot problems on your IPv6 network.
