
Kali Linux is the complete toolbox for penetration testing
Under the Magnifying Glass
Every IT infrastructure offers points of attack that hackers can use to steal and manipulate data. Only one thing can prevent these vulnerabilities from being exploited by unwelcome guests: You need to preempt the hackers and identify and close the gaps. Kali Linux can help.
To maintain the security of a network, you need to check it continuously for vulnerabilities and other weak points through penetration testing. You have a clear advantage over attackers because you know the critical infrastructure components, the network topology, points of attack, the services and servers executed, and so on. Exploitation tests should look for vulnerabilities in a secure, real environment, so you can shut down any vulnerabilities found – and you need to do this over and over again.
The variety of IT components dedicated to security does not make selecting a suitable tool any easier, because all possible attack vectors need to be subjected to continuous testing. Kali Linux [1] meets these requirements – and does much more.
Kali Linux at a Glance
The Debian-based Kali Linux distribution is at the heart of most penetration testing systems. The package contains more than 300 security tools, including those shown in Table 1.
Tabelle 1: A Few Kali Linux Security Tools
|
Tool |
Function |
|---|---|
|
OpenVAS |
The only free security scanner that meets professional requirements. |
|
Maltego |
Collects information about individuals or companies on the Internet. |
|
Kismet |
A passive sniffer to examine local wireless networks. |
|
Social Engineer Toolkit (SET) |
Includes programs that focus on social engineering. |
|
Nmap |
The well-known network scanner for network analysis, including the graphical user interface Zenmap. |
|
Wireshark |
The classic graphical network sniffer. |
|
Ettercap |
A network manipulation tool that helps hackers perform man-in-the-middle attacks. |
|
John the Ripper |
Cracks and tests passwords. |
|
Metasploit |
The classic tool for testing and developing exploits on target systems. |
|
Aircrack-ng |
A collection of tools for analyzing and exploiting vulnerabilities in WiFi networks. |
|
Nemesis |
A packet counterfeiter and injection utility. |
|
RainbowCrack |
A cracker for LAN manager hashes. |
Kali Linux groups the most frequently used and most important programs in the Favorites menu (Figure 1). However, you should be aware of one legal aspect before using it: Local data protection legislation applies when you use Kali Linux. In practical terms, this means that in many places you can only use Kali Linux for pentests if you have explicit permission to do so. Know your local laws.
Kali Linux is particularly resource-friendly and can be run in a virtual machine, so any notebook can become a full-fledged penetration test system with very little effort. Most administrators are familiar with classics like Wireshark and Nmap, so I will focus on the less common applications.
Security Scanners
Penetration testing begins with an overview of the infrastructure and then searches for specific weak points. To do this, you first use a security scanner. Depending on their nature and type, these tools are capable of checking entire networks or individual systems or applications for known weak points.
The most functionally comprehensive tool of this kind is OpenVAS [2], which knows thousands of vulnerabilities in common infrastructure components and can check their defenses. Once OpenVAS has identified open ports, you can use Nmap to discover details. Wireshark lets you identify any form of critical content and network activity that points to specific attack patterns. The classic Wireshark tool can also identify bottlenecks that might indicate hacker attacks and require a thorough check.
In the corporate world, web-based applications – often relying on the Apache, MySQL, and PHP stack – dominate the landscape. They are popular targets for hackers because they usually offer a great deal of attack potential. Kali Linux provides more than two dozen specialist tools for testing web applications. The scanners can be found in the Web Application Analysis menu. The Burp Suite and w3af tools are considered the best of their kind.
Burp Suite, which helps you identify and test vulnerabilities, is particularly easy to use. Kali Linux includes the open source version; the Pro version can even perform such tests automatically. For example, brute force attacks can be launched from the Intruder module, which uses request records grouped in the Proxy | Intercept tab to inject a desired payload into the web system.
Burp Suite also detects poor security configurations. An incorrect configuration of security settings can occur at all levels of the application stack (i.e., on web servers, application servers, and in databases and the web applications that use them). To detect such vulnerabilities with Burp Suite, first identify the target and then switch to the Target | Site map tab after mapping. Select the directory you want to check and execute the command Spider from here in the context menu. You can then determine any misconfigurations from the output.
In general, caution is required when analyzing production systems with security scanners, which are not primarily designed to handle systems that must be examined with kid gloves. Although many actions serve to identify points of attack, you should also expect that the systems tested will be affected. Therefore, you should perform these tests with mirrored systems. Ideally, these mirrors are protected by the same firewalls and intrusion detection systems (IDSs) of the production system, so you can check the effectiveness of existing protection mechanisms. Various tools (e.g., Nmap) can run in specific modes that make it difficult for IDSs to detect scans. In intelligent modes, they often remain undetected.
Sounding Out the Weak Points
If you know where the confirmed security gaps are, the next logical step is to sound them out. An essential part of any penetration test is the use of tools that help simulate as many known attack patterns as possible. Metasploit (Figure 2) is generally considered the most commonly used penetration tool, and one of the most important tools for penetration testers. The first step is to use the program's console to select and configure the exploit. Optionally, a vulnerability check is performed that tests whether the target system is at all vulnerable to the selected exploit. As a rule, you will have carried out a vulnerability scan in advance and have the necessary information.
The second step is payload selection. Meterpreter lets you search for files, escalate privileges, run port scans, redirect network traffic, and launch file downloads and uploads through an SSL connection to the target computer. In the third step, the exploit code is executed. Once you have successfully gained access to the system, you can usually perform further actions on the target computer with some payload.
If you regularly perform security checks with Metasploit, an environment for central management of the various configurations and actions is ideal. The Armitage graphical user interface lets you define different target criteria and quickly switch between them. You can create dozens, hundreds, or even thousands of hosts in special target sets. Armitage can import data from multiple security scanners, making preparation easier. The management tool displays the current targets graphically, so you can see at a glance where exploits are running.
Checking Wireless Networks
WiFi networks are certainly some of the most popular targets in an IT infrastructure. Kali Linux provides a variety of tools for testing WiFi networks and forcing access. The Wireshark network sniffer provides valuable services for the analysis of data frames.
The seemingly simplest way to protect a WiFi network is to make it invisible. Most access points support this function, but with Kali Linux, it is easy to detect the invisible networks and start a login attempt. In the standard configuration, all access points send their SSIDs in what is known as the beacon frame, one of the IEEE 802.11-based management frames in WiFi networks. It contains all the details of the network. Beacon frames are sent continuously to indicate the existence of a WiFi network. Only clients that know the SSID can connect to such a network. If you are using a notebook, you first need to set the wireless LAN adapter to monitor mode. To do this, execute the following two commands:
$ airmon-ng airmon-ng start wlan1
Now you can record wireless traffic with Wireshark. When searching for weak points and vulnerabilities, you are particularly interested in unencrypted traffic, so you must first find out which channel the access point is using:
$ airodump-ng --bssid <MAC address> mon0 where <MAC address>
Next, you can restrict traffic to this channel:
wlan.bssid == <MAC address>
To access a hidden SSID, you need to bypass the beacon frame with a little trick and use a passive technique to legitimize the client at the access point. Look for a sample response entry in the logs and open the SSID parameters. If you now examine a corresponding package entry and open its SSID information, you will notice the ID, so it is quite easy to find hidden wireless networks.
Alternatively, you can use aireplay-ng (Figure 3) to send a de-authentication packet to all potential access points:
aireplay-ng -0 5 -a <MAC address> --ignore-negative wlan0
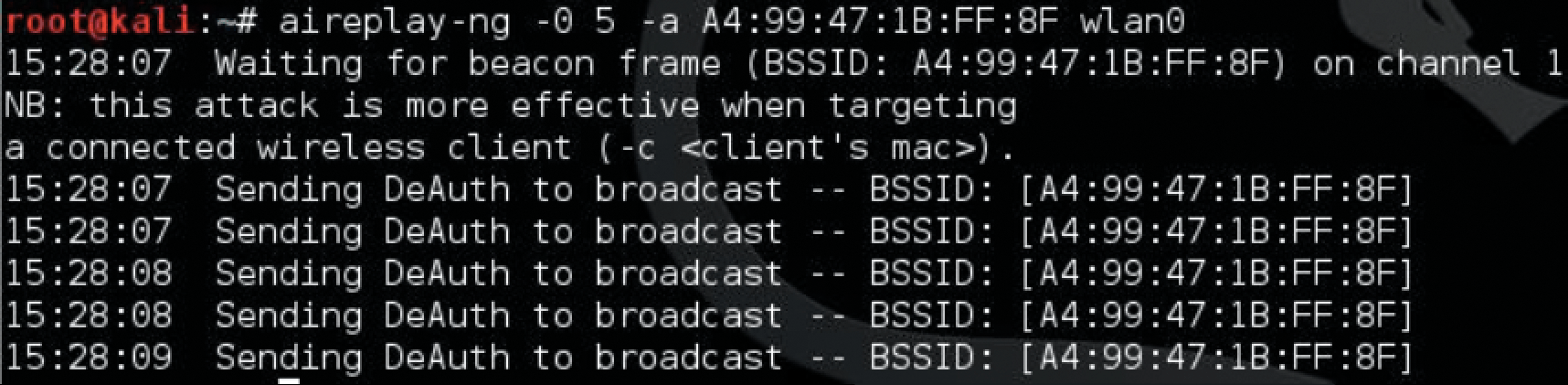
aireplay-ng tool offers valuable help in finding and compromising access points.Enter the MAC address of the router. The -0 option executes the de-authentication attack, and the value 5 determines the number of de-authentication packets. The option -a lets you indicate that the following address belongs to the access point.
This command causes all legitimate client connections to be interrupted and re-established. You need to record these actions with Wireshark. Next, you're interested in the de-authentication packages. Limit the view in Wireshark to these packages. If you now look again at the sample responses with Wireshark, the uncovered access point name is listed there in the SSID node. airodump-ng provides further important information on possible points of attack.
The cracking follows, and for this, you need aircrack-ng, which you feed the Recording.cap Wireshark file. For a better understanding: aireplay-ng executes the attack, and aircrack-ng cracks the safeguards. If the tool has enough recordings available for analysis, it ideally outputs the message KEY FOUND! after about five to 10 minutes, with the key displayed in square brackets.
Most wireless networks today use WPA2 encryption; it offers clear security benefits, because the passphrase and the SSID are encrypted and combined with each other more than 4,096 times. The protections this method offers are considerable and not easy to circumvent, but hackers do not necessarily fail here either.
To test the WPA2 decryption, use a precalculated pairwise master key (PMK). The PMK's preliminary calculation requires a given SSID based on a word list, which is what the genpmk program does:
genpmk -f wordlist -d PMK-test -s "test"
For testing purposes, create a WPA-PSK network with the passphrase and record the traffic. With cowpatty, you can now try to decode the phrase. You'll be amazed: This too is often successful.
Social Engineering
Even the smallest piece of information about a target system is relevant for potential attackers, including social information. Who uses which system? What are the relationships between users? Who do they communicate with? Social engineers spy on the personal environment of their victims, spoof identities, or exploit behaviors (e.g., authority) to obtain secret information.
The goal of social engineering is usually to penetrate a foreign computer system with the obtained information, also called social hacking. Other variants are human-based and reverse-social engineered. Social engineering depends to a large extent on a combination of all the collected data. Kali Linux also provides various tools for this often underestimated point of attack. The challenge in social engineering is not so much to collect the data as to put it into a meaningful structure. The optimal combination and visualization is crucial.
In Kali Linux, you'll find a program in your Favorites menu that you probably haven't heard of yet: Maltego. The program, developed by South African software developer Paterva, serves to link and visualize relationships between different components. Network and other resource entries can be created in Maltego, whether a server application, a router configuration, or personal data. With Maltego, you can link people, groups, companies, websites, infrastructure components (e.g., domains, DNS names, and IP addresses), phrases, documents, and files.
In addition to entities, Maltego distinguishes a second important feature, transformations, which lets you add further information to an entity. For example, you can assign an IP address to a website. In this way, links are created between the different elements, which you can then examine with Maltego in different representations. Maltego has well over 100 such transformations and 15 entity types.
Maltego's graphical user interface helps you visualize the relationships between different elements that you have not previously seen, even if the connections are routed through multiple points rather than directly. The question of what all this has to do with penetration testing is quite justified. But so is the answer: Maltego supports you in the information gathering phase with everything that is related to security.
Using the program is easy. To begin, you create a new document. The palette shows the different entity types divided into the categories Devices, Infrastructure, Locations, Penetration Testing, Personal, and Social Network. Various types are available through the transformation mechanism. For example, the To Domain transformation finds a person's top-level domains. The same thing works with email addresses. In addition to automatisms, such as Company Stalker, you can add your own information and links to the visualization.
Conclusion
Without a doubt: Kali Linux is the distribution of choice if you are looking for a complete toolbox for penetration testing. The package contains the right tools for every conceivable requirement – all under one roof. Its use is so simple that Kali Linux is also suitable for beginners. A more user-friendly way of getting started with penetration testing is hardly conceivable. For information on a pentesting tool for mobile devices, see the "Half-Hearted Mobile NetHunter" box.
