
Vulnerability assessment best practices for enterprises
Measure Twice, Cut Once
To understand how you can protect an organization's information technology properly through the use of a vulnerability assessment (VA), it is important to frame how you define a VA. For the context of this discussion, a VA is the process of identifying and quantifying vulnerabilities within a system. It can be used against many different types of systems, such as a home security alarm, a nuclear power plant, a military outpost, and a corporate computer environment. A VA is different from a risk assessment, even though they sometimes share some of the same commonalities.
VAs are concerned with the identification of vulnerabilities, the possibilities of reducing those vulnerabilities, and the improvement of the capacity to manage future incidents. In this article, I focus primarily on VA as it pertains to information technology infrastructures. Many times, an information technology VA can be conducted in conjunction with or overlapping a physical security VA. For the discussion here, I deal with information technology VAs only.
Preparation and Execution
A VA is a critical process that should be followed in any organization as a way to identify, assess, and respond to new vulnerabilities before they can be exploited by an external or internal threat. Generally, the assessing organization will perform a few common steps – outlined here and discussed in this article – when conducting a VA project for another organization:
- Obtain written approval from the organization for which you are conducting the VA.
- Find and document which information systems within the organization will be part of the VA and, just as importantly, which information systems will not be included.
- Define what tools, processes, and steps will take place before, during, and after the VA is conducted.
- Determine when the VA will occur (accurate date and time).
- Conduct the VA.
- Compile reports based on your findings from the VA.
- Brief the organization in person and in writing of your findings from the VA.
- If requested by the organization, put a plan in place to remediate the vulnerabilities found.
To understand how to frame a successful VA, a brief discussion of assets, threats, and vulnerability is useful.
Assets
An asset in the general sense is an organization's property or information that is of significant value (i.e., a critical asset). In risk management, an asset refers to the amount of damage losing an asset will cause if something bad occurs. Given that most enterprise networks have hundreds or thousands of networked information systems, vulnerability analysis and assessment by manual methods are virtually impossible. Additionally, it is impossible to ensure completely that all assets are secure. Therefore, it is imperative that information security managers and system owners focus on identifying only their critical assets – that is, those assets without which the organization's key missions would be significantly degraded or cease to function. This is a key part of the risk assessment process.
Threats
Risks to critical assets can come from a variety of threats that can be considered possible hazards and usually fall into three categories: man-made (intentional), natural disaster, and accidental (unintentional) disruptions. Therefore, an effective approach to threats will consider the full spectrum of threats and hazards, including natural disasters (e.g., floods, fires, hurricanes), domestic or international criminal activity, construction mishaps (e.g., cut fiber optic lines), and other types of incidents.
Vulnerabilities
Vulnerabilities are often defined as openings or pathways that a given threat can exploit to do harm to a critical asset.
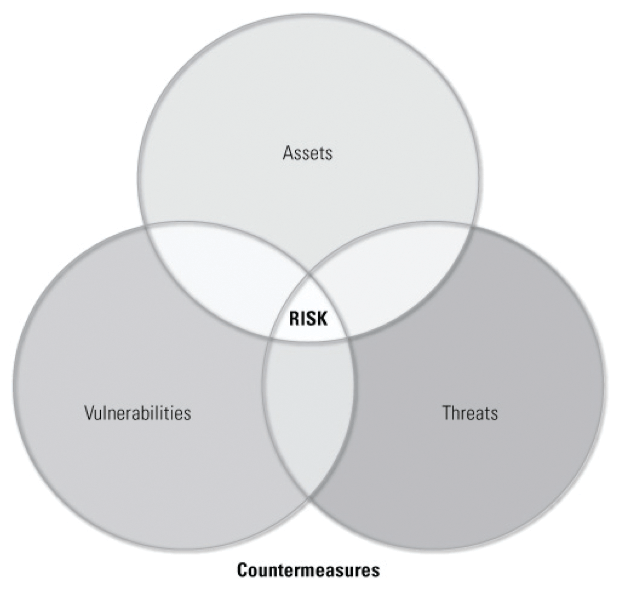
With the main components of risk in mind, a picture of risk can be formulated as the intersection of all three components (Figure 1).
Clear Guidance
VA activities must have acceptance from the highest levels of an organization. The management team within the organization must understand the importance of the assessment to the organization as a whole and then give the assessment team the approval they need to perform the activities. Once all of the parameters of the assessment are worked out and the risks are laid out, the organization assumes the risks of having their systems scanned.
The assessment team should clearly outline and exchange the following information with the organization being assessed:
- Written authority to perform the assessment from the management of the organization. Note: Be sure to have a finalized version of your authorization, highlighting executive sign-off from the organization with which you are working.
- The systems that will be included in the VA.
- The systems that will not be included in the VA.
- The members of the assessment team.
- Clear identification of the assessment team member who will initiate the scans as part of the VA.
- The tools that will be used in the VA scans, with a list provided to the organization receiving the assessment.
- The time parameters of the VA (how long and when it will take place).
- The time when the most intrusive or the most intensive aspects of the VA take place (e.g., after hours, during the weekend, during a scheduled outage).
- The data likely to be obtained during the VA.
- Assurances (if required by the organization) that the VA will only look at data within the systems agreed to be a part of the VA.
- Assurances (if required by the organization) that the VA will only scan systems and not access the data on those systems (port scanning),
- How the data obtained during the VA will be secured to protect the organization.
- Provisions to account for false positives that may occur during the VA. Do the false positives add to the organization's vulnerability and could they be avoided in the future as a mechanism for remediation?
- Emergency contact information within the organization's management team in case an unforeseen issue occurs during the VA, including during non-working hours.
- The type and scope of the reports that will be generated by the VA.
- Other mechanisms that will be utilized within the VA (i.e., social engineering techniques), with a detail of the framework for these other mechanisms.
- The type of VA to be conducted (e.g., black box, white box, gray box; see the "Black/White/Gray Box Testing Defined" box).
A successful VA program will include awareness training for the system owners once the VA is complete. Additionally, scanning will produce entries in logfiles that appear to be malicious in nature, so it is always a good idea to let the organization's administrators know, unless you are conducting a black box test. Typically the administrators you educate about the VA tools you will be using will also be the same group that will do the patching and remediation efforts generated from your assessment.
Gathering Information
The organization for which you are conducting the VA needs to make available the IT staff and management personnel that will help you properly ascertain the IT environment of the organization. The IT staff and management interviews can be just as useful in finding vulnerabilities within an organization as any technical control that could be deployed – that is, unless you are conducting a black box test, which would dictate that you have no prior knowledge of the system and the discovery of the IT infrastructure would in fact be part of the VA/penetration test. These types of assessments take more time and effort, which you should explain to the organization you are assessing.
Table 1 shows a broad list of possible question you can ask IT staff and management that might be helpful in evaluating the organization and their vulnerabilities.
Tabelle 1: Assessment Interviews
|
Risk Assessment |
|---|
|
Has the organization developed, documented, and disseminated a risk assessment policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance? |
|
Has the organization developed, documented, and disseminated procedures to facilitate the implementation of the risk assessment policy and associated risk assessment controls? |
|
Are the procedures and policies reviewed and updated (e.g., a risk assessment policy every five years, risk assessment procedures annually)? |
|
Does the organization develop, disseminate, and review or update the following at an organization-defined frequency: |
|
* Formal, documented security assessment and authorization policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance? |
|
* Formal, documented procedures to facilitate the implementation of the security assessment and authorization policy and associated security assessment and authorization controls? |
|
Has the authorizing official approved in writing the mitigation of risks found on a tested and validated mission-critical IT system? |
|
Do all security personnel and administrators receive orders and directives to conduct internal defensive measures, including vulnerability alerts and bulletins? |
|
Information Security (INFOSEC) |
|
Has the organization developed and disseminated an organization-wide information security program plan? |
|
Is the security plan approved by a senior official with responsibility and accountability for the risk being incurred to organizational operations (including mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the nation? |
|
Has a security manager or someone with equivalent responsibility been designated in writing to ensure that classified and controlled unclassified information is properly handled during its entire life cycle? |
|
Cybersecurity |
|
Does the organization have a program established to prevent damage to, protect, and restore computers, electronic communications systems, electronic communications services, wire communication, and electronic communication, including information contained therein, to ensure its availability, integrity, authentication, confidentiality, and nonrepudiation? |
|
Are all mission IT systems and networks reviewed through a configuration management process to ensure changes do not have a significant effect on security (e.g., new network connections, operating system changes, and a new mission or new threats)? |
|
Has the organization conducted a comprehensive annual cybersecurity review that evaluates whether the existing policies interconnect with the current system configurations to ensure consistency? |
|
Has the organization done an analysis to identify assets and support for critical infrastructure networks and components, including cyber systems and assets? |
|
Does the organization integrate cybersecurity considerations into their business continuity planning? |
|
Is cybersecurity incorporated into the annual exercise, either in the form of a live exercise or a tabletop exercise? |
|
Are the system(s) within the organization installed according to the installation policies and standard configuration? |
|
Does the organization mandate that all systems have the latest security patches installed? |
|
Does each system have separate accounts and passwords (i.e., email, applications, etc.)? |
|
Does the organization ensure separation of duties between individuals involved in information system support functions and audit operations? |
|
Do the information systems enforce a limited number of consecutive invalid login attempts by a user during an organization-defined time period? |
|
Do the information systems automatically lock out a user account when a predefined maximum number of unsuccessful attempts are exceeded and then only permit reinstatement by an administrator? |
|
How are audit records and logs reviewed and maintained? |
|
Are backups conducted on IT systems? |
|
Are backups periodically checked to ensure they can recover the system? |
|
How are backups conducted: tapes, backup server (disk packs), storage area network (SAN)? |
|
Are backups stored at a geographically separate site? |
|
Are backups stored in a fireproof container? |
|
Are web servers placed in demilitarized zones (DMZs) and are all unnecessary services and processes removed or disabled? |
|
Is only authorized and licensed software used on the system? |
|
Are all ports, protocols, and services that are not required for operations blocked? |
|
Does each administrator who has access to IT systems have a password? |
|
Are spare parts or replacement equipment readily available? |
|
Are any routers configured with a dial-in modem? |
|
Do routers and switches have appropriate security controls (e.g., access only by authorized personnel)? |
|
Network Security |
|
Does the network architecture implement a layered security approach: e.g., proxy servers, DMZ, network intrusion detection systems (NIDSs), virtual private networks (VPNs), host-based intrusion detection systems, early warning devices, and firewalls? |
|
Does the organization have appropriate measures to ensure that continuous monitoring of the network is maintained to identify any potential security breaches? |
|
Does a current and comprehensive baseline inventory exist of all hardware (to include manufacturer, type, model, physical location, and network topology or architecture) and software (operating system, applications)? |
|
How does the organization review and update the baseline configuration of the information system? |
|
Is a security analysis conducted on the effect of any and all changes to the system, before implemented, to ensure network integrity? |
|
Does the organization provide basic security awareness training to information system users? |
|
Industrial Control Systems (ICS) |
|
Has risk assessment been completed as it relates to ICS? |
|
Are data flow controls tested to ensure that other systems cannot directly access devices within the ICS environment? |
|
Does the organization implement a security plan that concentrates on continuous security improvements and that focuses on the life cycle of the ICS? |
|
Does the ICS organization implement an effective defense-in-depth strategy? |
|
Does the organization implement policies and procedures governing access to control centers, field devices, portable devices, media, and other ICS components? |
|
Is the ICS assets list reviewed and updated annually? |
|
Does the organization have in place procedures for operating the ICS in manual mode, with all external electronic connections severed until secure conditions can be restored? |
|
Does the organization have clear roles and responsibilities for responders? |
|
Does the organization have a list for all personnel that have access to the ICS? |
|
Does the organization implement real-time monitoring of ICS, to include patch management, policy management software, and other security mechanisms? |
|
Is the ICS manned 24 hours a day seven days a week? |
|
Are all ICS control panels locked and alarmed? |
|
Are ICS vendor's laptops allowed to connect to ICS? |
Categorization of Assets
An IT asset is classified as any organization-owned information, system, software, and hardware used in the course of the organization's business activities. The most important question is: What information technology assets do you want to scan? The simple answer is everything you can get your scanners to reach and is within the scope of your VA.
With today's blended organizations, a threat can attack almost anything running within a UDP or TCP environment. The common set of devices that might be included within your VA include workstations (laptops, desktops, thin clients, and kiosks), servers (Windows, Unix, Linux, Solaris, etc.), network gear (routers, switches, access points, load balancers, video conference units, etc.), and miscellaneous equipment (network-enabled printers, standalone webcams, facility HVAC controls, shipping equipment, electronic door controls, fire alarms, audio/video gear, industrial control systems, etc.).
Once you have defined a list of assets that are within your VA, you must then categorize where these assets fit within the organization. What are the most critical assets to the organization that are within the scope of the VA? What assets might have a cascading effect on other assets and make them vulnerable? These questions and many others need to be answered to get as clear a picture as possible of the organization's IT vulnerabilities; then, you can conduct your VA and, one hopes, give the organization mitigation solutions that enable them to harden their IT systems. The main objective of a VA is to find vulnerabilities and patch them before they can be exploited by an attacker.
Discovery of Assets
Several methods will allow you to discover company assets. The first, and the least painful, method is to obtain network diagrams from the IT staff and management team in the organization for which you are conducting the VA. Network diagrams should give you a head start in discovering the network ranges and boundaries and will definitely help in identifying the network's equipment.
Second, meeting with the IT staff and management team will aide greatly in understanding the scope of where the assets will be found. It should be noted here that if you point your VA scanner at devices that are not within your scope of work, you could find yourself in legal trouble. As you should know, most organizations you have the potential to work with do not like a foreign entity scanning their devices without their express permission. Be sure you document what network information you discover. All subnets that are controlled by the organization should be documented as well, as long as those subnets are within the scope of your VA.
Third, utilizing the mapping you have created might help your VA. The term "mapping," when referring to vulnerability scanners, typically implies a very simple TCP, UDP, or ICMP scan to discover devices on the network. With these details in hand, you should be able to glean a clear picture of the organization's IT infrastructure that might surprise you, as well as the organization you are assessing.
Most Internet protocol-enabled devices when sent a TCP SYN packet will respond and thus identify themselves as an active device. Sections of any network divided into parts can be mapped effectively in a reasonable amount of time. You could find in certain scenarios that this discovery method will not identify all devices. Some network-based devices do not respond to ICMP ping sweeps, will not have common TCP ports open, could be blocked with firewalls, or have a combination of these conditions. Be aware of these devices because they can still be susceptible to network-based attacks and should be included in your assessment.
Whether mapping networks or querying staff is used, you should begin to see where the assets within an organization can be found on the network. The type of assessment will determine many of the factors above. Will a foreign partner actively contribute to the VA or will they rely on you? The organization for which you are conducting the VA needs to be viewed as a partner in this endeavor.
Precautions
Potential threats caused by the scan process itself can pose risks to IT systems by, for instance, crashing an already vulnerable server if all "plugins," including high-risk ones are enabled, for example, a denial of service (DoS) scan. Therefore, risk assessment and careful planning are necessary before scanning. Usually, for a preproduction system, it might be acceptable to enable all plugins; however, for ongoing, continual scans on a production system, administrators should consider disabling certain high-risk plugins.
Additionally, when scanning with a network-based scanner, a large number of system requests and a great deal of network traffic are generated. The administrator should note any deterioration in the system and network performance of the target groups during scanning.
Vulnerability Scanners and Scanning Parameters
Before continuing the discussion, I need to define a vulnerability scanner: a software application that assesses security vulnerabilities in networks or host systems and produces a set of scan results. However, because both administrators and attackers can use the same tool for fixing or exploiting a system, administrators need to conduct a scan and fix problems before an attacker can do the same scan and exploit any vulnerability found.
The benefits of a vulnerability scanner are, first, that it allows early detection and handling of known security problems. By employing ongoing security assessments using vulnerability scanners, it is easy to identify security vulnerabilities that may be present in the network, from both the internal and external perspective.
Second, a new device or even a new system might be connected to the network without authorization. A vulnerability scanner can help identify rogue machines that might endanger overall system and network security.
Third, a vulnerability scanner helps verify the inventory of all devices on the network. The inventory includes the device type, operating system version and patch level, hardware configurations, and other relevant system information. This information is useful in security management and tracking.
Vulnerability scanners have several drawbacks: (1) They can only assess a "snapshot in time" in terms of a system's or network's security status. Therefore, scanning needs to be conducted regularly because new vulnerabilities can emerge or system configuration changes can introduce new security holes. (2) They can only report vulnerabilities according to the plugins installed in the scan database. They cannot determine whether the response is a false negative or a false positive. Human judgment is always needed in analyzing the data after the scanning process. (3) They are designed to discover known vulnerabilities only. They cannot identify other security threats, such as those related to physical, operational, or procedural issues.
Vulnerability scanners can be divided broadly into two groups: network-based scanners that run over the network and host-based scanners that run on the target host itself.
Network-Based Scanners
A network-based scanner is usually installed on a single machine that scans a number of other hosts on the network. It helps detect critical vulnerabilities, such as misconfigured firewalls, vulnerable web servers, risks associated with vendor-supplied software, and risks associated with network and systems administration.
Different types of network-based scanners include: port scanners that determine the list of open network ports in remote systems, web server scanners that assess the possible vulnerabilities in remote web servers (e.g., potentially dangerous files or CGIs), and web application scanners that assess the security aspects of web applications running on web servers (e.g., cross-site scripting and SQL injection). It should be noted that web application scanners cannot provide comprehensive security checks on every aspect of a target web application. Additional manual checking (e.g., whether a login account is locked after a number of invalid login attempts) might be needed to supplement the testing of web applications.
One of the most popular network-based scanners is Nessus. Nessus is a network scanning tool that was developed by Tenable Network Security. This software offers a variety of functionalities, such as vulnerability scanning, system configurations auditing, malware detection, and web application scanning.
Nessus supports the widest range of systems and devices and includes the latest security tests for available security patches, disclosed vulnerabilities, and common worms. This software enhances network inventory with advanced features like asset discovery, multi-network scanning support, and automated scans. If you are interested in trying Nessus, you can find it at: http://www.tenable.com/products/nessus-vulnerability-scanner.
Another popular network-based scanner is BeyondTrust's Retina Network Security Scanner. BeyondTrust's Retina Network Security Scanner is a vulnerability assessment solution program that offers continuous observation to strengthen enterprise security by identifying IT asset vulnerability and sensitive data across detersive environments. It also covers priority-based risk assessment from small to large environments by realizing optimal network performance and scanning network devices, operating systems, applications, and databases without affecting the network availability or performance.
Retina NSS can be deployed as a standalone vulnerability scanner or distributed throughout an environment. It can also be integrated with Retina CS for enterprise deployments. To know the required system and hardware specs to run this tool, visit the following link for a free trial: http://www.beyondtrust.com/Modal/trial/retina-network-security-scanner.
Host-Based Scanners
A host-based scanner is installed on the host to be scanned and has direct access to low-level data, such as specific services and configuration details of the host's operating system. It can therefore provide insight into risky user activities, such as using easily guessed passwords or even no password. It can also detect signs that an attacker has already compromised a system, including looking for suspicious file names, unexpected new system files or device files, and unexpected privileged programs. Host-based scanners can also perform baseline (or filesystem) checks. Network-based scanners cannot perform this level of security check because they do not have direct access to the filesystem on the target host.
A database scanner is an example of a host-based vulnerability scanner. It performs detailed security analysis of the authorization, authentication, and integrity of database systems and can identify potential security exposures in database systems, ranging from weak passwords and security misconfigurations to Trojan horses.
Nessus and Retina can be used locally to conduct host-based scanning. One other free tool that can assist with host-based scanning is Nmap. Nmap includes the following features:
- Active port scanning: allows you to scan and discover open ports on specific networks/hosts.
- Host discovery: lets you identify potential hosts that are responding to network requests.
- OS detection: used to discover the operating system name and version, along with network details where the host is running.
- Application version detection: nmap can also determine what applications are running, along with the version numbers.
Download Nmap at: https://nmap.org/.
Deployment Practices
Whether a network-based scanner is located in front of or behind the firewall will have an effect on the scan result. Scanning an internal network from outside the firewall will only detect services that are available to the outside, but not vulnerabilities within the internal network that cannot be seen because of the protections provided by the firewall. On the other hand, scanning DMZ hosts from the inside might not provide a complete picture of the security position. Therefore, both external and internal scanning should be conducted to build a more complete picture.
Network-based port scanning detects which ports are available (i.e., being listened to by a service). Because open ports could imply security weaknesses, port scanning is one of the basic reconnaissance techniques used by attackers. Therefore, security scanning should always include port scanning. However, some vulnerability scanners have a predefined default port range set (e.g., from port 0 to 15000). System administrators should be aware of these default settings and ensure all necessary ports are scanned.
False Positives
A false positive is an alert for a problem that does not actually exist. Handling false positives is yet another important step in a VA. No VA software or scanner can completely eliminate false positives, and your team should be prepared to deal with these events when they are identified.
Vulnerability scanners will use several methods to determine whether a system is susceptible to a known weakness. The assessment team at times during the VA will have to do on-the-ground detective work to determine whether the found vulnerability is real or a false positive. The improper diagnosis of a false positive could skew your report results and degrade your credibility with the organization that entrusted you to conduct the VA.
Reporting the Results
Generating reports against your collected assessment data is critical to the VA program. Providing the right data to the right people is the key to a successful effort.
Some of the important details that should be contained within the assessment reports you generate include:
- Definition of VA and the goals for utilizing the applied technology.
- The specified time frame of the VA.
- The top 10 vulnerabilities found during the VA and an explanation of the found vulnerabilities.
- Categorization of the data in the report (i.e., host, vulnerability, OS, asset, service, network mapping, port able to be accessed).
- Detailed information pertaining to the identified vulnerabilities. (This will help the team that will be responsible for patching the system.)
- Report displayed by severity (each system affected by the vulnerability).
- Report displayed by system (each vulnerability on the device listed).
- Areas of the infrastructure that were part of the assessment (scope) and what was left out.
- An explanation of how the VA scanning appliances operated.
- An explanation of how the generated reports can be used to show details about the vulnerabilities and where the patches can be found.
Handling Scan Results
Leaks of the scanning results, which contain system vulnerability information, could facilitate attackers in exploiting the loopholes identified. Therefore, it is important to safeguard this information by keeping it in a safe place or keeping it encrypted to prevent unauthorized access. If an external party is employed for the assessment process, the organization should ensure that any party involved is trustworthy and that both findings and proprietary information will be kept secure.
Irrelevant data, giant reports, and reports filled with false positives are the easiest ways to get people to take your vulnerability reporting less seriously and can jeopardize the credibility of your VA. The goal is to create high-quality, relevant, and filtered reports for the teams that will be conducting the remediation. Your VA will give the remediation team a path forward.
After a VA, the assessed organization should institute (if not already in place) an organization-wide Cyber Security Awareness Training Program. The awareness training should include details about the completed VA. The level of detail provided during training regarding the completed VA might have to be scaled according to the audience. The possibility of an insider threat could reduce the amount of detail the senior management in the organization may be willing to provide.
The awareness training should include, but is not limited to, depending on the scope of the VA and the requested support after a VA has taken place, several of the list items that appear under the "Reporting the Results" section, plus a couple of other items:
- A definition of VA and the goals for the technology used.
- An explanation of how the VA scanning appliances operated.
- The areas of infrastructure that were part of the assessment (scope) and that were left out.
- How the generated reports can be used to show details about the vulnerabilities and where the patches can be found.
- How the additional technology used during assessment can be used to benefit the various departments in the future.
- Details about the severity levels of a threat to an organization and at what level the organization deems something mission critical.
Compliance and Life Cycles
VA has a never-ending life cycle of continual scans, reports, assessments, remediations, and evaluations and must be addressed in such a way to be truly effective. Daily, new attack signatures are developed, viruses and worms are written, buffer overflows are discovered, and changes in an organization's infrastructure and new technologies are developed that increase the susceptibility of an organization to vulnerabilities. Each of these actions affects the risk posture of the organization. Any one piece of the life cycle cannot be effective without the other.
Once the VA is complete, the reports have been presented, and the organization has been briefed, you need to give them the tools to stay protected against new vulnerabilities. No interconnected IT environment is 100% removed from potential attacks, but if you can impress upon the organization you are working with the importance of regularly scanning their systems, they will be better off than when you arrived, which is your ultimate goal.
Conclusion
A single piece of malware can cause widespread trauma to an organization and even significant injury to an entire region of the world. A good VA program can help prevent these problems from ever happening. A VA program can assist with reducing an organization's overall risk level and, in turn, allow an organization to perform effective due diligence in order to uncover the true vulnerabilities. By creating a comprehensive VA program, an organization can add another layer to its in-depth defense strategy. By identifying key vulnerabilities and providing future mitigation guidance to your organization, you will be strengthening your risk management program as well. A successful and comprehensive VA program can help any organization safeguard its critical information and systems.
