
Real World AWS for Everyone
Cloud Config
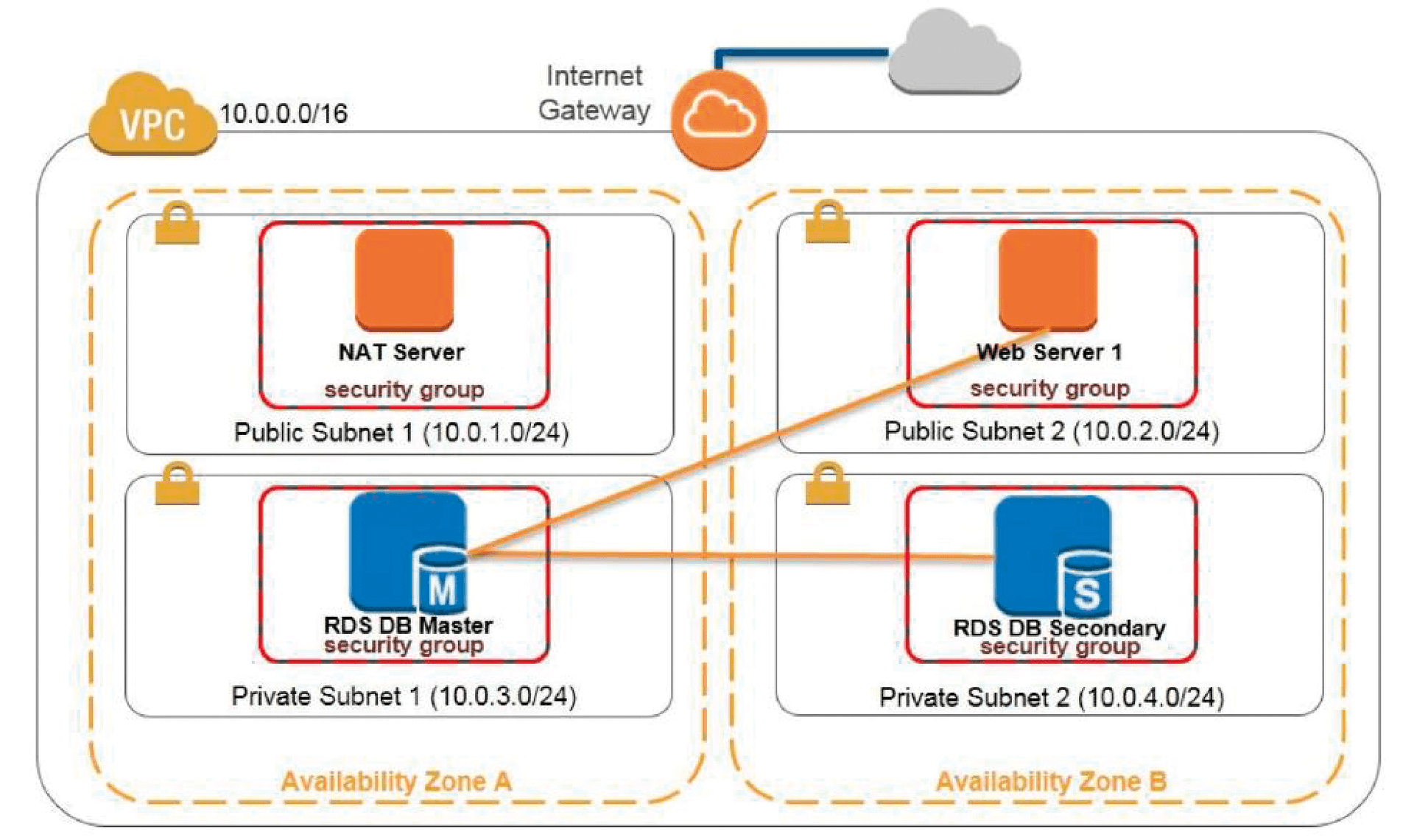
Amazon offers a comprehensive portfolio of public cloud services. The options cover the spectrum from IaaS, to PaaS, to SaaS to managed services. Due to the impressive usability, even small companies without available cloud experts find it easy to get started. In all, Amazon Web Services (AWS) [1] offers well over 50 cloud services, roughly divided into categories such as data processing and storage, database, and migration [2]. Amazon's services are similar to Lego bricks; you can combine them using a simple management console GUI to build virtual networks with different properties. You can also churn up Amazon services through a command-line interface or trigger them programmatically using the provided APIs. This article describes how to implement a web server with a high-availability back-end database in the Amazon cloud . The configuration is similar to the scenario depicted in Figure 1. A NAT server will provide connectivity with the Internet. The database is via Amazon's Relation Database Service (RDS).
Terms and Concepts
Amazon's data centers are subdivided into regions, with the USA traditionally best connected. Europe is represented by Dublin (eu-west-1), London (eu-west-2), and Frankfurt (eu-central-1), with each location offering redundancy via a regional mirror. The concept of Availability Zones (AZs) lets you design individual services with high availability if desired. The AZ can be found in the dashboard for the service under Service Health | Availability Zone Status. The scope and availability of the individual services varies according to region, AZ, and subnetwork. Your piece of the AWS cloud's total cloud cake is referred to as a Virtual Private Cloud (VPC). In addition to actual virtual machines (instances), which are generated from templates (Amazon Machine Images, or AMI), elements such as subnets, firewalls (security groups), routers, gateways, load balancers, and so on are also included.
Price Structure of AWS
The pricing structure of AWS [3] is complex because almost every service is based on a different billing model. The scenario described in this article includes the pricing structures of Amazon Elastic Compute Cloud (EC2), Amazon VPC, and Amazon RDS. Roughly speaking, compute services such as EC2 are calculated by usage time. Compute alone offers three ways of booking EC2 instances: on-demand, reserved instances, and spot-instances. Reserved (purchase of capacity in advance) can save up to 50 percent, and spot instances (a kind of instance exchange) up to 70 percent compared to on-demand costs. As long as you are in the IaaS environment, you are responsible for setting up your virtual machine (VM), integrating it into existing virtual networks, connecting to storage, and ensuring high availability – just as you would be in a local data center. However, a virtual server is much faster and easier to provision than a conventional server. In addition, creating, (re)configuring, and using networks (SDN) and storage (SDS) is much more easier than if you were working with real hardware.
Access Gate AWS Account
You need an AWS account to get started. Press Create a Free Account on the AWS home page to set up an account quickly – in principle, you do not need more than an email address and a credit card. You can use the AWS Free Tier [4] free of charge for 750 hours EC2, 750 hours RDS, and 5GB S3 storage. If you decide to continue, you'll need to choose a plan from one of the individual cost models; however, the Free Tier is a good option for testing. Log on to the AWS Management Console [5] with a root account and password. An AWS account and password is sufficient for the examples in this article. If you also want to manage tenants in your AWS account or use AWS resources via an API, click on your own username in the upper right-hand corner and switch to the AWS Security Credentials page [6]. Create access key pairs for the required tenants/users. An AWS access key always has a key ID in the form of AKIAJ4 PMEXHFYUHIXG2A and a secret access key such as :/ONT0HapjmLw7xni 6FPscmvPZJ Sc75hUXAQI+N3W. In addition to password and access key pairs, AWS also supports multi-factor authentication (MFA), CloudFront key pairs, and X.509 certificates. If you wish to access AWS from your own applications programmatically, you may also need the AWS Account ID and the Canonical User ID. Additionally, you can and should set up and use Identity and Access Management (IAM) users [7]. When you access the security credentials page, AWS asks if you want to work with security credentials or the role-based IAM model. IAM is excellently documented on the AWS side and experienced admins will easily find their way through it.
Your Own Public Cloud
Start by creating a VPC, which serves as a base from which you can launch AWS resources on a virtual network. A VPC can extend over several AZs. You also need security groups. An Internet gateway (IGW), created by default, controls the communication between the instances in the VPC and the outside world; you can adapt the routing tables of gateways and routers to your needs at any time. Once the prerequisites have been met, you can use a VM template (Amazon Machine Images) to create a VM, in this case for the web server, and start it later. AWS for VPN solutions such as Direct Connect [8] will provide administrative access to the VPC. You'll find the VPC Wizard under Services in the Networking & Content Delivery section of the VPC. Clicking on Start VPC Wizard leads you through the process of creating a VPC in a few steps and offers various starting points; in this case, VPC with Public and Private Subnets. Remember to set the region you want to use in the top-right corner. We are starting with a Class B IPv4 address for the VPC itself, as well as one private subnet and one public subnet with a Class C address each. Both should initially be located in the same AZ. To connect the private subnet to the Internet, you can either use the NAT gateway offered below the subnet configuration and request an Elastic IP (EIP) address, or you can click on Use a NAT instance instead to the right if you want to set up the NAT gateway yourself (Figure 2).
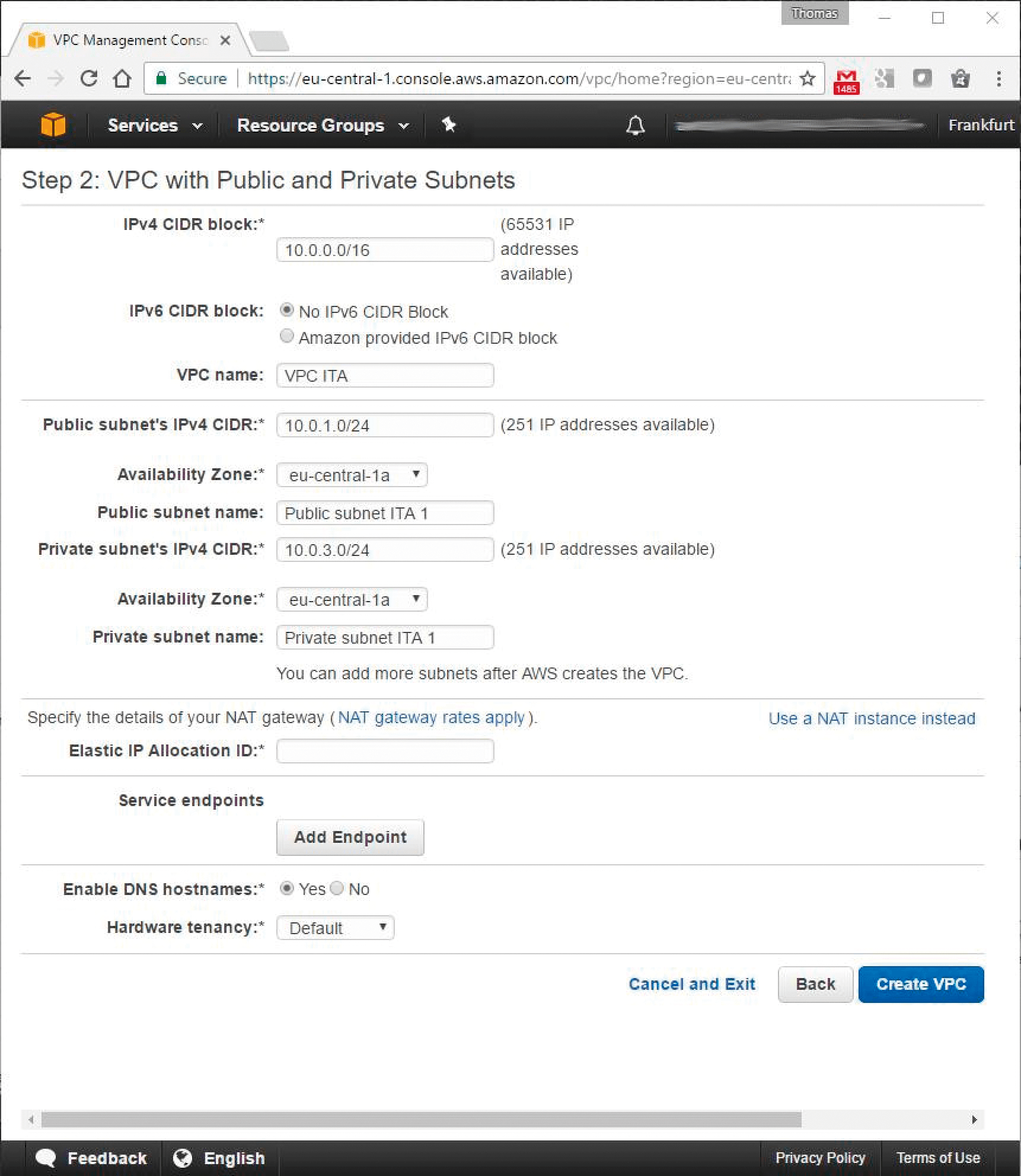
This example will use the t2.micro NAT instance, which is included in the Free Tier option. You'll need a key pair to use the t2.micro NAT. Create two additional subnetworks Private 2 and Public 2 in the second availability zone for the planned high-availability DB scenario under VPC / Your VPC / Subnets services. You are free to choose which address ranges you want to use as long as they are in the IP address range of the VPC. One level above, in the VPC dashboard, you will see the entire inventory list, which currently consists of two VPCs (including one default VPC), two routing tables, two security groups, and, if applicable, a NAT gateway; I decided to use a dedicated VM as a NAT gateway. For this reason, an EIP public IP address has already been assigned.
Firewall and Network ACLs
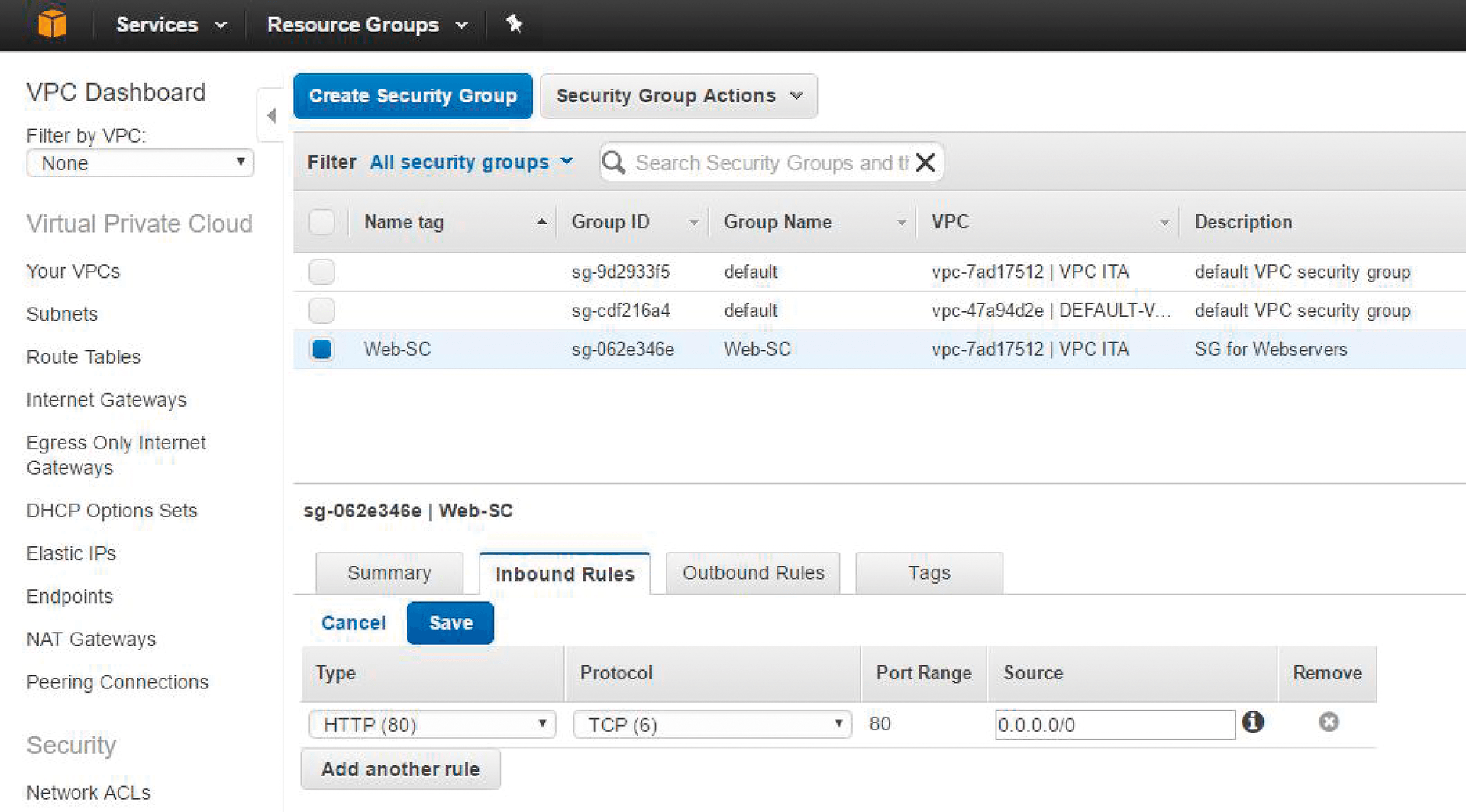
Once you are accustomed to the usability and functionality of the AWS management interface and the logic of the various wizards, you will find it easy to create security groups or routing tables and install VMs from templates. I'll launch an initial security group called Web-SG to allow HTTP access to the newly created VPC; in the simplest case, you'll need an inbound rule of type HTTP for all incoming connections (Source 0.0.0.0/0). You can configure Network ACLs and Security Groups through the Security subsection (Figure 3). Network ACLs operate on all traffic that reaches or leaves the subnet; Security Groups, on the other hand, operate at instance level. In other words: Security groups act as a firewall for the EC2 instance, while network ACLs act as a firewall at the subnet level. However, there is a default network ACL that is virtually wide open.
Creating the Virtual Web Server
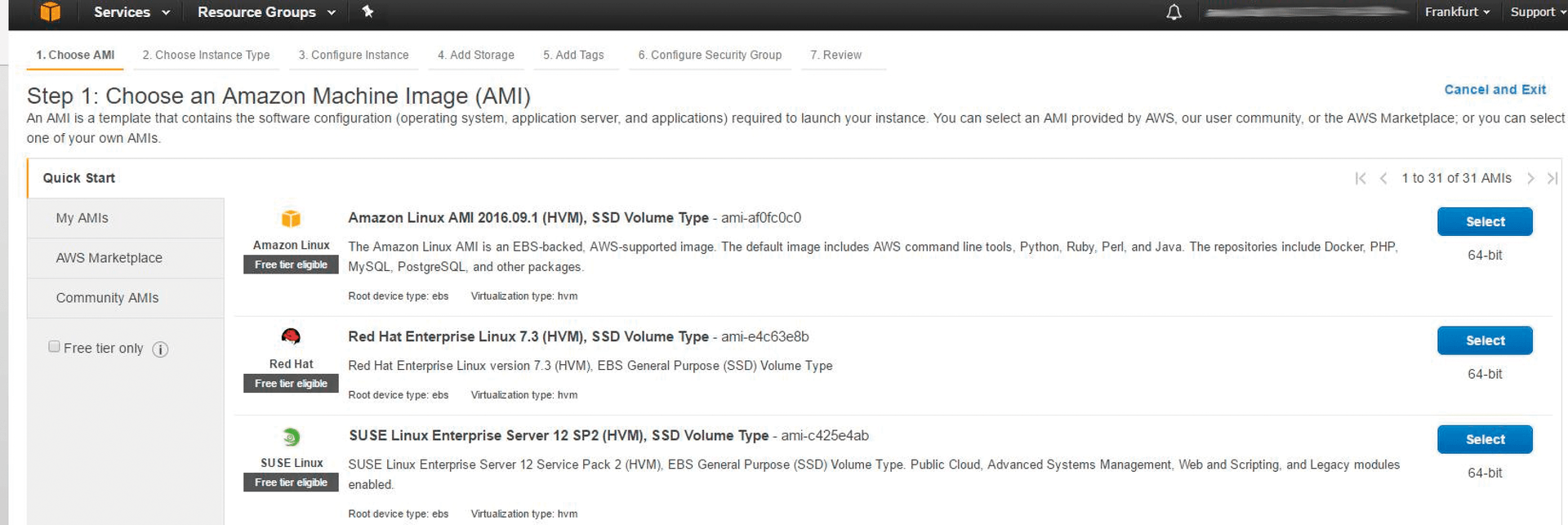
Now you can set up the actual web server as a virtual instance. I will use the Amazon Linux AMI as a base template (Figure 4). The launch process is accompanied by an intuitive wizard. First select the instance type, the target VPC, and the subnet on which the new instance will reside. Auto-assign Public IP = Enable ensures that every new virtual network card added to this subnet automatically receives a public IP address. By the way, public IPs are volatile, in contrast to EIPs, meaning that, after a shutdown or reboot of the instance, they are replaced by a new IP address from the AWS pool for the region.
An EIP does not generate any extra costs, because as long as you are using it, Amazon is already earning money with the instance. Costs only arise if you do not use or assign an EIP. Amazon wants to prevent people from hoarding public IP addresses. In the Advanced Details area, you can specify a start configuration for the instance. For Linux machines, the technology is based on cloud-init; Windows systems work with PowerShell scripts. You could also create a script that installs the necessary services and performs some configuration tasks (Listing 1).
Listing 1: Installing Services
01 #!/bin/bash -ex 02 yum -y update 03 yum -y install httpd php mysql php-mysql 04 chkconfig httpd on 05 /etc/init.d/httpd start 06 if [ ! -f /var/www/html/prep.tar.gz ]; then 07 cd /var/www/html 08 Wget here could be a script that prepares the web server for interaction with the database 09 tar xvfz prep.tar.gz 10 chown apache:root /var/www/html/rds.conf.php
As storage for the WWW root, I will use Elastic Block Storage (EBS) and choose Magnetic to avoid additional costs. In the beginning, AWS only supported local storage of the underlying commodity hardware. However, this is naturally volatile, because it should not usually be assumed that your own instance will start on the same underlying hardware after a relaunch. The launch instance wizard also runs through the creation and assignment of security groups. If you also want direct SSH access to the web server, you need to set up and assign another security group for SSH. A final click on Launch starts the instance. AWS offers to generate a key pair and then download both keys (AWS does not store private keys in the cloud) if SSH access is desired. After you click on View Instances, the new instance first appears in the instance list with the pending status, which changes to running after the time required for booting and processing cloud-init. The currently valid public IP appears as a column in the list; more details are revealed in the Description tab at the bottom. Access to the web server should work via the public IP. In this example, an EIP is not assigned. I use Amazon Linux AMI to create an instance for the NAT server in the second AZ and a matching NAT-SG security group, within which the private subnets gain access to the NAT device via port range 0-1024.
Databases from a Single Source
The next step is to set up a MySQL database as a back end for the web server on the private subnet. You can set up a new VM, install MySQL on it, and save it as a separate AMI template, from which you could then create additional DB-VMs. The other options is to use Amazon's RDS. In addition to open source-based databases such as PostgreSQL and MySQL, RDS offers commercial alternatives such as Oracle or Amazon Aurora. Aurora is a MySQL-compatible enterprise database service that, according to Amazon, only costs 10% of what you can expect for commercial database engines. However, keep in mind that the prices for Database-as-a-Service options are added on top of those of the utilized EC2 resources or Elastic Block volumes. In contrast to MySQL, Aurora supports up to 15 low-latency read replicas, an automatically scalable storage capacity of up to 64TB, and six-way replication across three AZs if required. But whether Aurora or MySQL: The advantage of setting up the database as a managed service is that it is relatively easy to configure the database across multiple AZs. A firewall rule for communication between the database instance and the web server is required in the activity zone; I will create another security group to provide this rule. The group allows incoming traffic of the MySQL/Aurora type on port 3306 with the web server security group as the source. In order to instantiate the database in two AZs, a construct of the subnet group is also required. The starting point for creating subnet groups is the RDS dashboard under Services | RDS (Figure 5). Clicking on Subnet Groups leads to the wizard called Create DB Subnet Group. You'll also need to add two subnets to the other AZ.
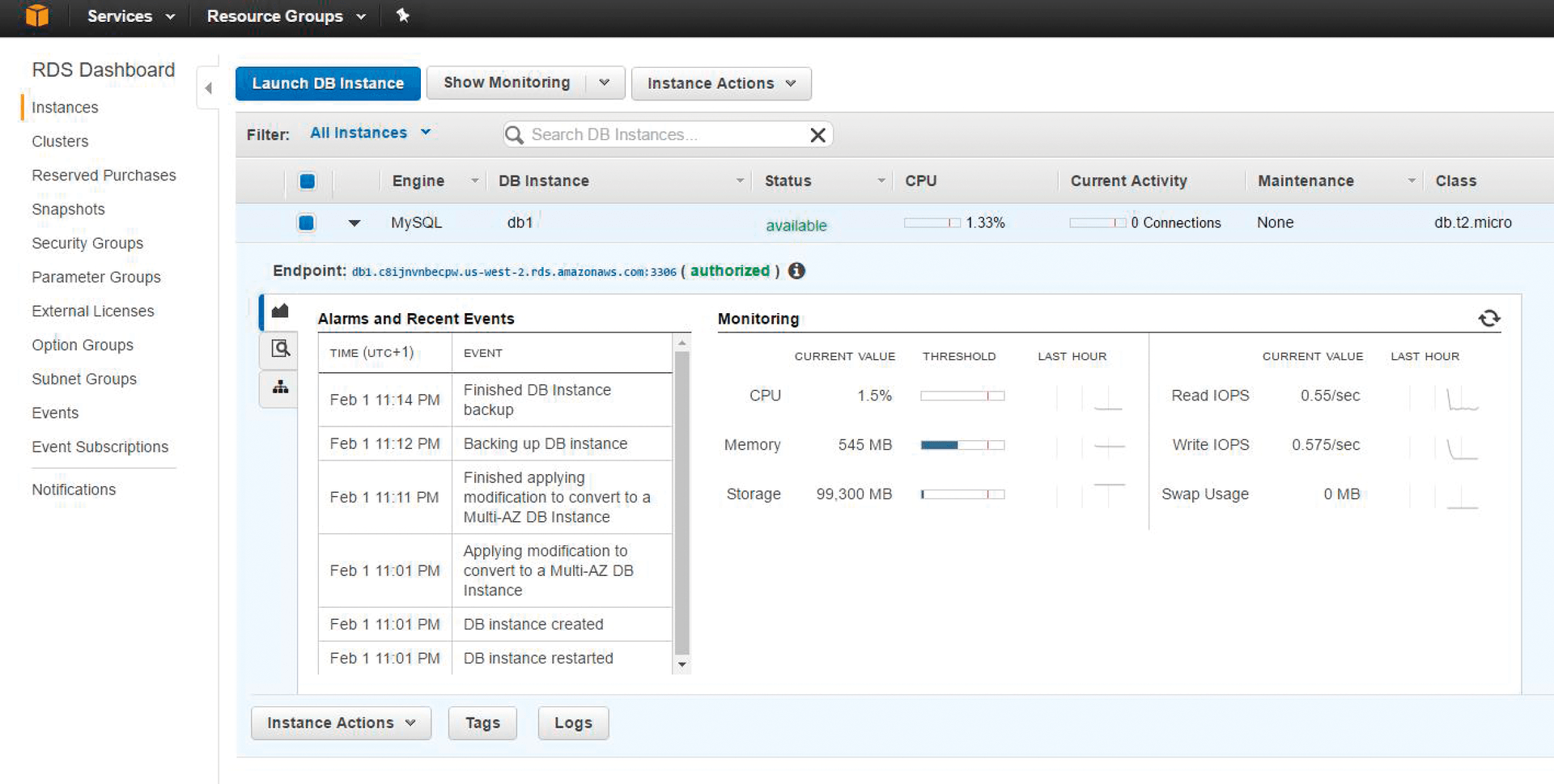
The database is then instantiated with Launch DB Instance in the Instances area. The wizard is largely self-explanatory. MySQL is fine as an engine; Amazon Aurora is not included in the Free Tier quota. DB Engine Version gives you a free choice from 5.5.40 to 5.7.16. As a DB Instance Class, I will use db.t2.micro - 1 vCPU - 2 vCPU, 1GB RAM. However, the desired Multi-AZ Deployment option is not available in MySQL in the Free Tier. The corresponding check mark at the top of the dialog has to be removed to enable the setting. For the storage type (Elastic Block Storage), I started with General-Purpose (SSD). If you have also specified a DB Instance identifier, as well as a master user and password, Configure Advanced Settings is all about placing the database instance in the desired VPC and the appropriate subnet group or VPC security group and enabling public access if necessary. With the Database Options and Backup settings, you can essentially accept the default settings and activate the instance by clicking on Launch DB Instance. Clicking on View your DB Instances then lists all active database instances. The initial creating status changes to modifying and, after about ten minutes, to available. The RDS dashboard offers many other interesting options, such as the management of snapshots, but for this scenario, it is initially important just to make a note of the entry underneath the instance list that is valid for the instance marked above under Endpoint (in this case, db1.c8ijnvnbecpw.us-west-2.rds. amazonaws.com:3306, which you need to interact with the web server). Armed with this information, switch back to the instance list of the EC2 dashboard, note the public IP of the web server, and call the corresponding web page in the browser. Click on the RDS menu link and insert the string for Endpoint in the input field. Then add the username and password and click on Submit to transfer the configuration. To test whether the PHP application communicates properly with the database, use the web interface to add, edit, and remove a contact.
Scaling Made Easy
You can convert the configuration into an auto-scaling setup in a few easy steps, so that additional instances will start up during peak loads. Also, with some access to the AWS shelf, you could operate several web servers behind a load balancer. Look for the AWS Elastic Load Balancer (ELB) in the EC2 dashboard under Load Balancing. Finally, various VPN solutions supported by AWS make it easy to access your own subnets from the outside or even build up a hybrid structure. For example, you could operate one or more Windows servers on premise and other Windows servers as EC2 instances – configured as read-only domain controllers. You could also provide branch offices with identity and authentication services that are available via the AWS Virtual Private Gateway. An IIS on a public subnet as the basis for your own Exchange infrastructure with Outlook Web Access would also be a conceivable scenario for SMEs. You can monitor virtually all AWS resources using Amazon Cloud Watch [9], which provides a host of base metrics free of charge. Additional costs are only incurred with special metrics or smaller sample rates up to real time.
Conclusions
The scenario in this article uses only a fraction of the services available in AWS. Each step of the configuration is possible using a GUI, although the primary strength of AWS lies in API control. With the help of AWS Cloud Formation [10], entire deployments can be created on a template basis without additional costs. Using the Cloud Formation Designer, companies can visually create complex AWS constructs such as a VPN gateway in a fraction of the time. The one question that is deceptively difficult to answer is whether the total cost incurred for all monthly IaaS, PaaS, and SaaS services is lower than the cost of installing, operating, and maintaining a comparable, on-premise infrastructure. The AWS pricing model is very complex [3], and it isn't easy to compare the cloud versus home scenarios directly. For instance, the cost for auto-scaling on-premise deployments is difficult to estimate. Detailed analysis of AWS discount and billing models is therefore just as important as the design of a coherent security plan. Nevertheless, AWS's service diversity, usability, and functionality go further than Google or Azure's current offers, and building a private cloud with OpenStack or VMware vRealize Automation is unlikely to be an option for small-to-midsized businesses.
